Hackers have already compromised thousands of Palo Alto Networks firewalls in attacks exploiting two recently patched zero-day vulnerabilities.
The two security flaws are an authentication bypass (CVE-2024-0012) in the PAN-OS management web interface that remote attackers can exploit to gain administrator privileges and a PAN-OS privilege escalation (CVE-2024-9474) that helps them run commands on the firewall with root privileges.
While CVE-2024-9474 was disclosed this Monday, the company first warned customers on November 8 to restrict access to their next-generation firewalls because of a potential RCE flaw (which was tagged last Friday as CVE-2024-0012).
Palo Alto Networks is still investigating ongoing attacks chaining the two flaws to target “a limited number of device management web interfaces” and has already observed threat actors dropping malware and executing commands on compromised firewalls, warning that a chain exploit is likely already available.
“This original activity reported on Nov. 18, 2024 primarily originated from IP addresses known to proxy/tunnel traffic for anonymous VPN services,” the company said on Wednesday.
“At this time, Unit 42 assesses with moderate to high confidence that a functional exploit chaining CVE-2024-0012 and CVE-2024-9474 is publicly available, which will enable broader threat activity.”
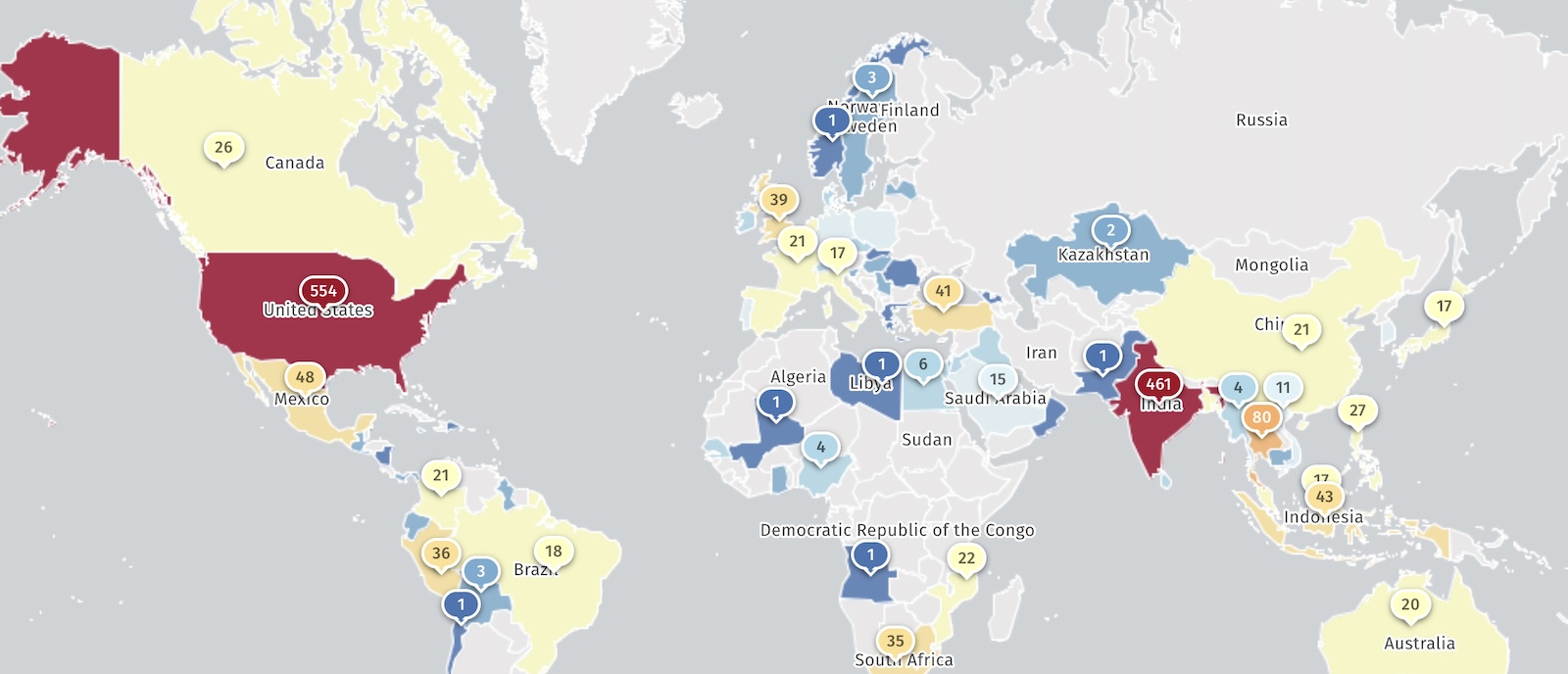
Even though the company says the attacks impact only a “very small number of PAN-OS” firewalls, threat monitoring platform Shadowserver reported on Wednesday that it’s tracking over 2,700 vulnerable PAN-OS devices.
Shadowserver is also tracking the number of compromised Palo Alto Networks firewalls, and it said that approximately 2,000 have been hacked since the start of this ongoing campaign.
CISA has added both vulnerabilities to its Known Exploited Vulnerabilities Catalog and now requires federal agencies to patch their firewalls within three weeks by December 9.
In early November, it also warned of attackers exploiting another critical missing authentication flaw (CVE-2024-5910) in the Palo Alto Networks Expedition firewall configuration migration tool, a flaw patched in July that can be exploited to reset application admin credentials on Internet-exposed Expedition servers.
Earlier this year, the company’s customers also had to patch another maximum severity and actively exploited PAN-OS firewall vulnerability (CVE-2024-3400) that impacted over 82,000 devices. CISA also added CVE-2024-3400 to its KEV catalog, asking federal agencies to secure their devices within seven days.
Palo Alto Networks “strongly’ advised its customers on Wednesday to secure their firewalls’ management interfaces by restricting access to the internal network.
“Risk of these issues are greatly reduced if you secure access to the management web interface by restricting access to only trusted internal IP addresses according to our recommended best practice deployment guidelines,” the company said.
