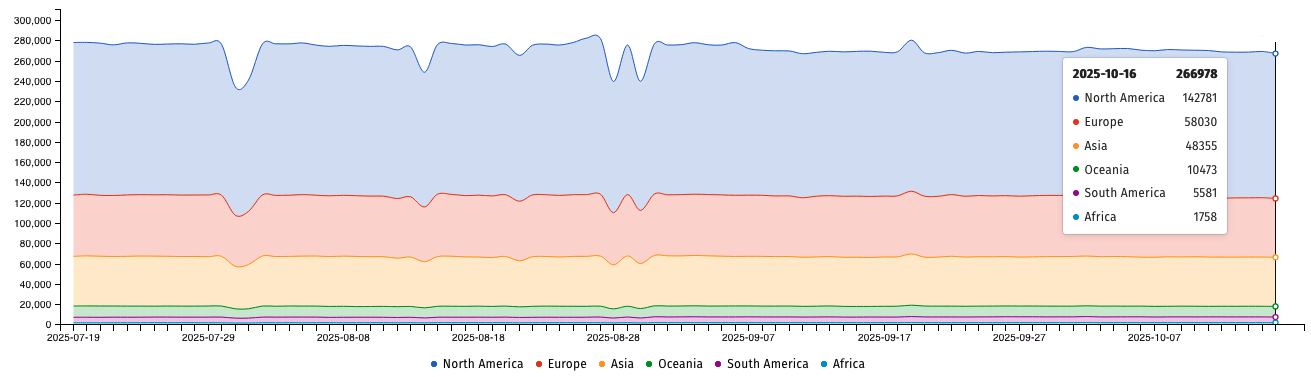
Internet security nonprofit Shadowserver Foundation has found more than 266,000 F5 BIG-IP instances exposed online after the security breach disclosed by cybersecurity company F5 this week.
The company revealed on Wednesday that nation-state hackers breached its network and stole source code and information on undisclosed BIG-IP security flaws, but found no evidence that the attackers had leaked or exploited the undisclosed vulnerabilities in attacks.
The same day, F5 also issued patches to address 44 vulnerabilities (including the ones stolen in the cyberattack) and urged customers to update their devices as soon as possible.
“Updates for BIG-IP, F5OS, BIG-IP Next for Kubernetes, BIG-IQ, and APM clients are available now,” the company said. “Though we have no knowledge of undisclosed critical or remote code execution vulnerabilities, we strongly advise updating your BIG-IP software as soon as possible,”.
While it has yet to confirm it publicly, F5 has also linked the attack to China in private advisories shared with customers, according to a Thursday Bloomberg report,
F5 has also been sharing a threat-hunting guide with its customers that mentions the Brickstorm malware, a Go-based backdoor first spotted by Google in April 2024 during an investigation into attacks orchestrated by the UNC5291 China-nexus threat group. F5 also told customers that the threat actors were active in the company’s network for at least a year.
UNC5291 was previously linked to exploiting Ivanti zero-days in attacks targeting government agencies, using custom malware such as Zipline and Spawnant.
The Shadowserver Internet watchdog group is now tracking 266,978 IP addresses with an F5 BIG-IP fingerprint, nearly half of them (over 142,000) in the United States and another 100,000 in Europe and Asia.
However, there is no information on how many of them have already been secured against attacks that could potentially exploit the BIG-IP vulnerabilities disclosed this week.
This week, CISA also issued an emergency directive, mandating U.S. federal agencies to secure F5OS, BIG-IP TMOS, BIG-IQ, and BNK/CNF products by installing the latest F5 security patches by October 22, while for all other F5 hardware and software appliances on their networks, it extended the deadline to October 31.
CISA also ordered them to disconnect and decommission all Internet-exposed F5 devices that have reached end-of-support, as they will no longer receive patches and can be easily compromised in attacks.
“CISA is directing Federal Civilian Executive Branch (FCEB) agencies to inventory F5 BIG-IP products, evaluate if the networked management interfaces are accessible from the public internet, and apply updates from F5,” the cybersecurity agency said.
In recent years, both nation-state and cybercrime threat groups have been targeting BIG-IP vulnerabilities to map internal servers, hijack devices on victims’ networks, breach corporate networks, steal sensitive files, and deploy data-wiping malware.
Compromised F5 BIG-IP appliances can also allow threat actors to steal credentials and Application Programming Interface (API) keys, move laterally within targets’ networks, and establish persistence.
F5 is a Fortune 500 tech giant that provides cybersecurity, application delivery networking (ADN), and services to over 23,000 customers worldwide, including 48 of the Fortune 50 companies.
46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.

