Over 3,300 Citrix NetScaler devices remain unpatched against a critical vulnerability that allows attackers to bypass authentication by hijacking user sessions, nearly two months after patches were released.
Tracked as CVE-2025-5777 and referred to as CitrixBleed 2, this out-of-bounds memory read vulnerability results from insufficient input validation, enabling unauthenticated attackers to access restricted memory regions remotely on devices configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server.
Successfully exploiting this security flaw could enable threat actors to steal session tokens, credentials, and other sensitive data from public-facing gateways and virtual servers, allowing them to hijack user sessions and bypass multi-factor authentication (MFA).
Proof-of-concept (PoC) exploits targeting CVE-2025-5777 were released less than two weeks after the flaw was disclosed, while active exploitation in zero-day attacks was detected weeks before the release of these PoC exploits.
A similar Citrix security flaw, known as “CitrixBleed,” was exploited two years ago to hack NetScaler devices and move laterally across compromised networks in ransomware attacks and breaches targeting government entities.
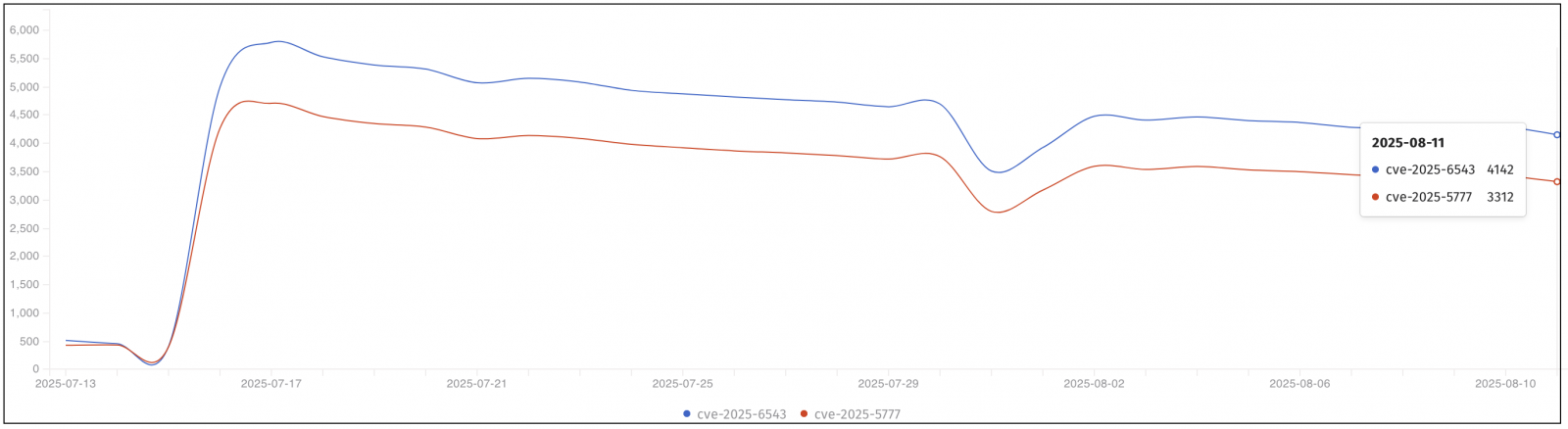
On Monday, security analysts from the internet security nonprofit Shadowserver Foundation reported that 3,312 Citrix NetScaler appliances were still vulnerable to ongoing CVE-2025-5777 attacks.
Shadowserver also spotted 4,142 such devices left unpatched against another critical vulnerability (CVE-2025-6543), which Citrix has tagged as actively exploited in denial-of-service (DoS) attacks.
While Citrix states that CVE-2025-6543 is a memory overflow vulnerability that can lead to unintended control flow and denial of service, the Netherlands’ National Cyber Security Centre (NCSC) warned on Monday that attackers have exploited this flaw as a zero-day since at least early May to breach multiple critical organizations in the country.
“The NCSC has determined that multiple critical organizations in the Netherlands have been successfully attacked via a vulnerability identified as CVE-2025-6543 in Citrix NetScaler,” the NCSC said..
“The NCSC assesses the attacks as the work of one or more actors with an advanced modus operandi. The vulnerability was exploited as a zero-day, and traces were actively removed to conceal compromise at affected organizations.”
Although the agency did not name any of the affected organizations, the Openbaar Ministerie (the Netherlands’ Public Prosecution Service) disclosed a breach on July 18th following an NCSC alert. As a result of the attack, the Openbaar Ministerie experienced significant operational disruption and only recently restored its email servers.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also added the two vulnerabilities to its catalog of actively exploited vulnerabilities, ordering federal agencies to secure their systems against CVE-2025-5777 attacks within a day and against CVE-2025-6543 exploitation by July 21st.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
