Researchers discovered 49,000 misconfigured and exposed Access Management Systems (AMS) across multiple industries and countries, which could compromise privacy and physical security in critical sectors.
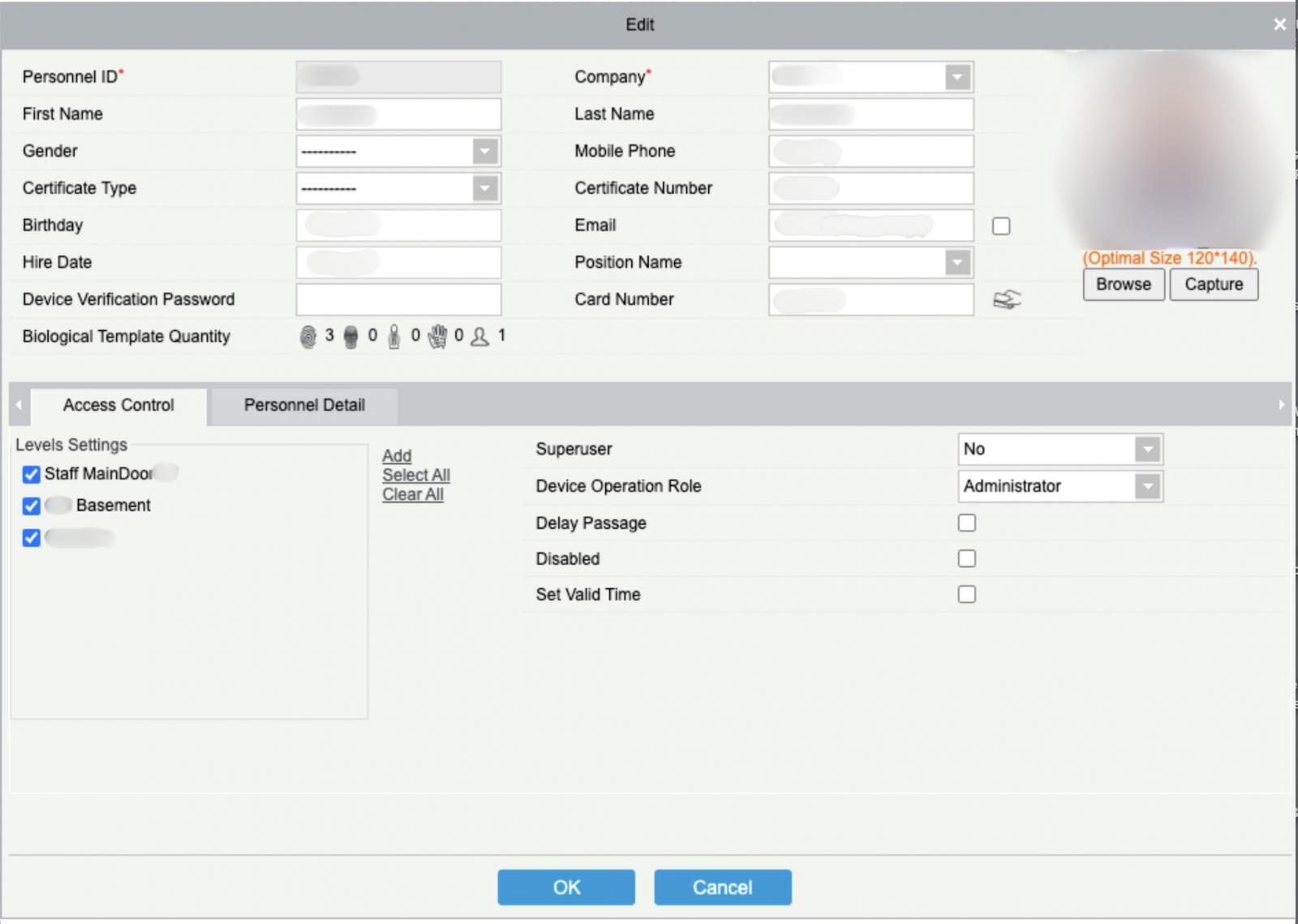
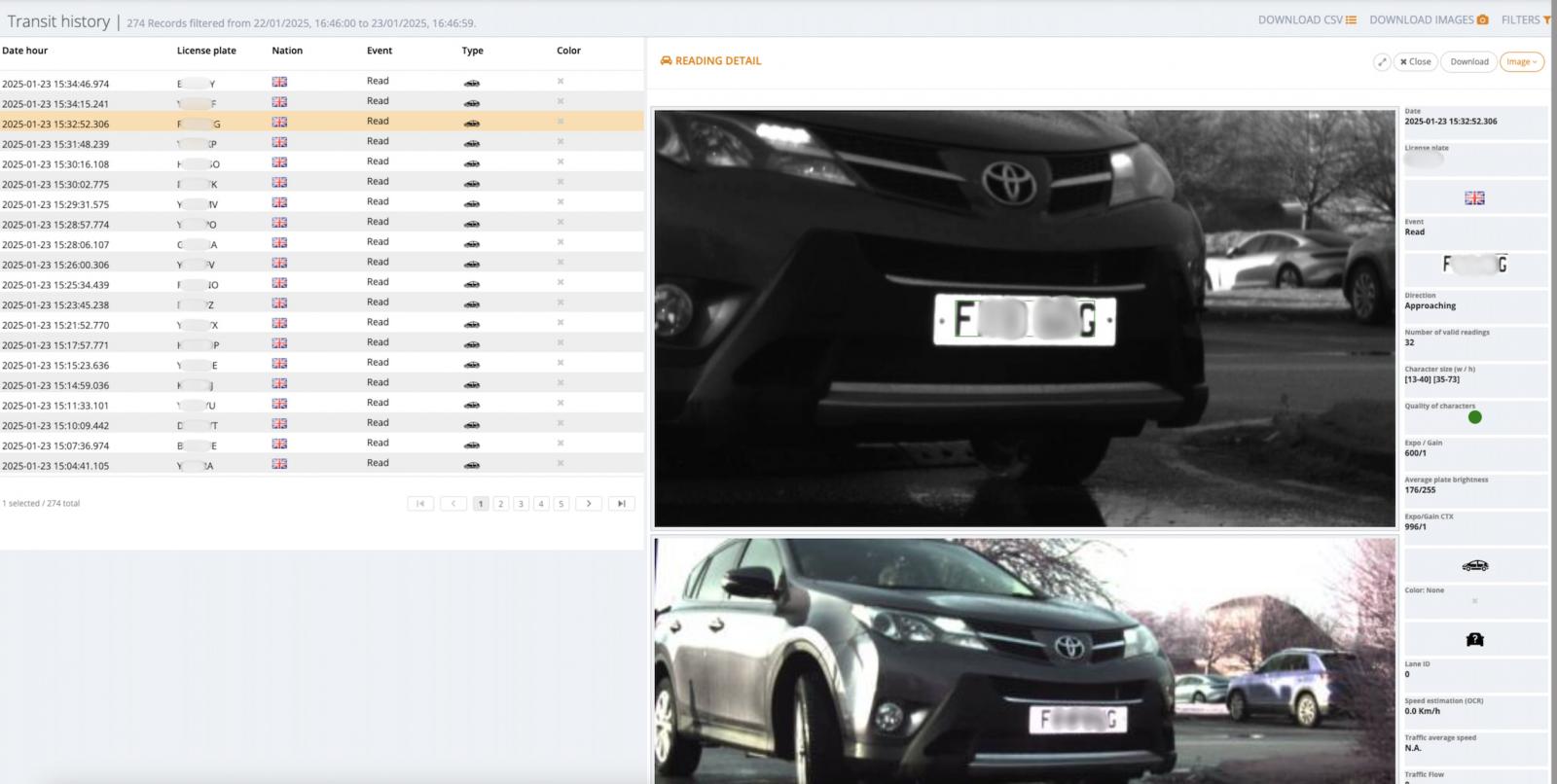
Access Management Systems are security systems that control employee access to buildings, facilities, and restricted areas via biometrics, ID cards, or license plates.
Security researchers at Modat conducted a comprehensive investigation in early 2025 and discovered tens of thousands of internet-exposed AMS that were not correctly configured for secure authentication, allowing anyone to access them.
The exposed AMS contained sensitive unencrypted employee data, including:
- Personal identification details (names, email addresses, phone numbers)
- Biometric data like fingerprints and facial recognition
- Photographs
- Work schedules
- Access logs indicating who entered/exited and when
In some cases, Modat could edit employee records, add fake employees, change access credentials, or manipulate building entry systems to restrict access to legitimate employees or allow unauthorized physical access to malicious actors.
Source: Modat
The physical security risks are particularly worrying for exposed AMS for government buildings and critical infrastructure such as power stations and water treatment units.
Apart from physical security, the exposed information could also be leveraged to empower spear-phishing and social engineering attacks against the exposed organizations.
Source: Modat
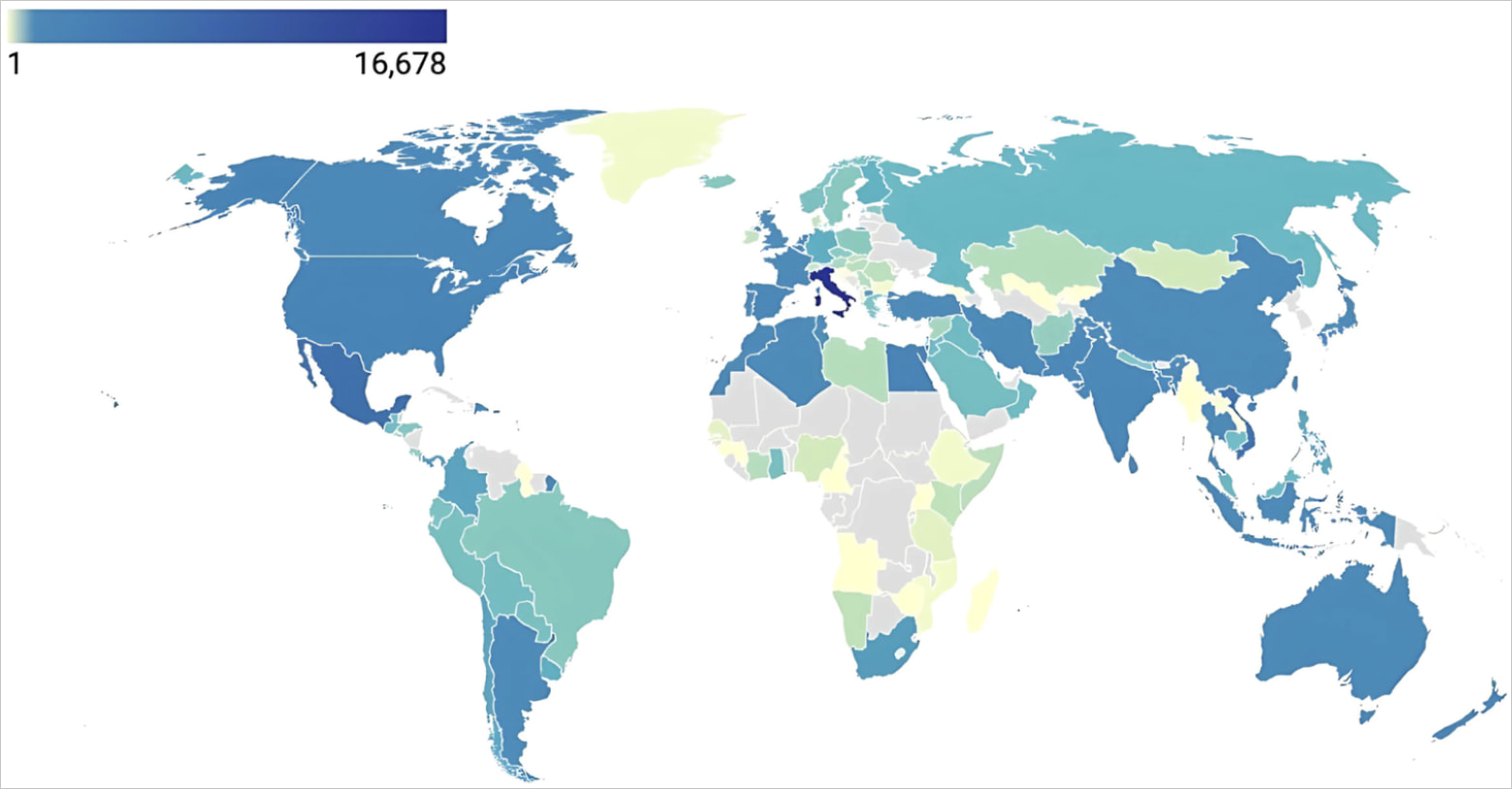
Out of the total 49,000 exposed AMS devices globally, most (16,678) are located in Italy, followed by Mexico (5,940) and Vietnam (5,035). In the U.S., Modat found 1,966 exposed AMS systems.
Source: Modat
Mitigating the problem
The researchers contacted all system owners directly to inform them of the AMS exposure and the risks this entails to their organizations. However, they told BleepingComputer they have not heard back yet, so it is unclear how many acted to secure their systems.
Vendors were also contacted, and some responded that they are working with impacted clients to fix the exposure.
Modat provided several security recommendations for AMS users, including taking their systems offline to prevent unauthorized remote access or placing them behind firewalls and VPNs to restrict access only to authorized personnel.
It is also recommended that the default admin credentials be changed as those are easy to brute-force, and multi-factor authentication (MFA) should be implemented if the option is available.
AMS admins should apply their vendors’ latest software and firmware updates and reduce unnecessary network services that may increase the attack surface.
Biometric data and PII should always be stored in encrypted form, and data of past employees should be purged to avoid unauthorized access via old accounts that haven’t been disabled on other systems.
