The P2PInfect botnet worm is going through a period of highly elevated activity volumes starting in late August and then picking up again in September 2023.
P2PInfect was first documented by Unit 42 in July 2023 as a peer-to-peer malware that breaches Redis instances using a remote code execution flaw on internet-exposed Windows and Linux systems.
Cado Security researchers who have been following the botnet since late July 2023, report today seeing global activity, with most breaches impacting systems in China, the United States, Germany, Singapore, Hong Kong, the UK, and Japan.
Additionally, Cado says the latest P2PInfect samples feature additions and improvements that make it more capable of spreading to targets and showcase the continuous development of the malware.
Steep rise in activity
Cado sees P2PInfect botnet activity, indicating that the malware has entered a new period of code stability that allows it to ramp up its operation.
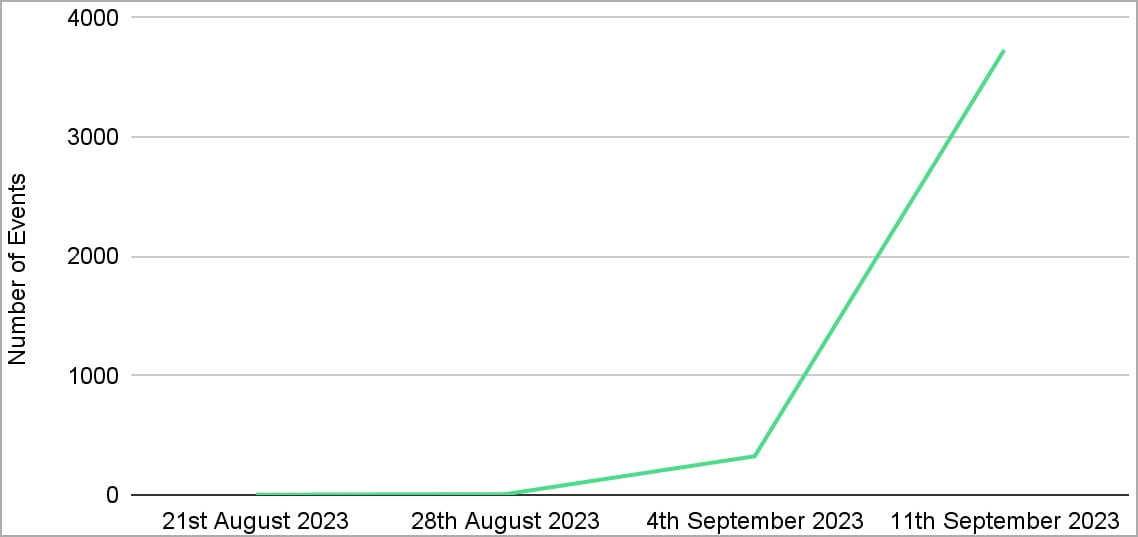
The researchers report observing a steady increase in the number of initial access attempts performed by P2PInfect on their honeypots, leading to 4,064 events from a single sensor as of August 24, 2023.
By September 3, 2023, initial access events had tripled but remained relatively low.
Then, in the week between the 12th and 19th of September 2023, a surge in P2PInfect activity occurred, with Cado recording 3,619 access attempts during this period alone, which is a 600x rise.
“This increase in P2Pinfect traffic has coincided with a growing number of variants seen in the wild, suggesting that the malware’s developers are operating at an extremely high development cadence,” explains Cado.
New P2PInfect features
Alongside the increased activity, Cado observed new samples that make P2PInfect a stealthier and more formidable threat.
First, the malware’s authors have added a cron-based persistence mechanism that replaces the previous ‘bash_logout’ method, triggering the main payload every 30 minutes.
Additionally, P2Pinfect now uses a (secondary) bash payload to communicate with the primary payload via a local server socket, and if the main process stops or is deleted, it retrieves a copy from a peer and restarts it.
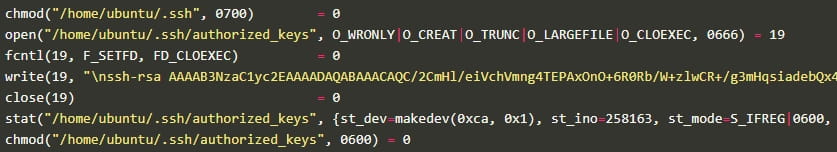
The malware now also uses an SSH key to overwrite any SSH authorized_keys on the breached endpoint to prevent legitimate users from logging in via SSH.
If the malware has root access it will perform a password change for any other users on the system using an automatically generated 10-character password to lock them out.
Finally, P2PInfect now uses a C struct configuration for its client that is updated dynamically in memory, whereas previously, it didn’t have a configuration file.
Unclear goals
Cado reports that the P2PInfect variants it observed recently attempted to fetch a miner payload but did not see actual cryptomining activity on compromised devices. Therefore, it’s unclear if the malware operators are still experimenting with the final step of the attack.
The botnet’s operators may be enhancing the miner component or seeking buyers of subscriptions to P2PInfect, so they use the miner as a dummy for demonstration.
Given the current botnet’s size, spread, self-updating features, and fast expansion this month, P2PInfect is a substantial threat to keep an eye on.
