Can you tell the difference between legitimate marketing and deepfake scam ads? It’s not always as easy as you may…
As South Korean President Lee Jae-myung pushes ahead with his ambitious plan to relocate the presidential office back to the…
American pharmaceutical company Inotiv has disclosed that some of its systems and data have been encrypted in a ransomware attack,…
“There are limitations to what we can see with this data, but what we have so far is accurate,” says…
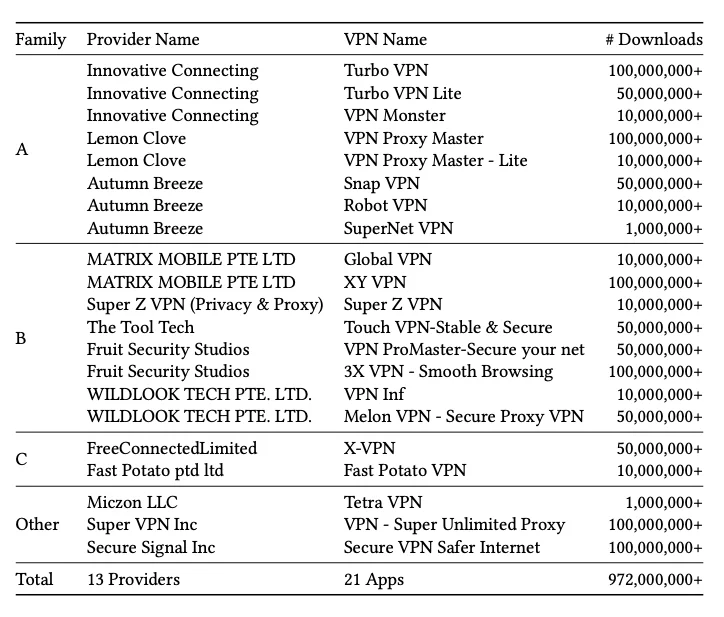
Three families of Android VPN apps, with a combined 700 million-plus Google Play downloads, are secretly linked, according to a…
The Cyber Express, in collaboration with Suraksha Catalyst, has kicked off the Black Hat USA 2025 CISO Series Podcast with…
The United Kingdom has withdrawn its demand that Apple create a backdoor to its encrypted cloud systems following months of…
Malaysia’s communications regulator has assured the public that their privacy remains intact, despite a government move to hoover up data…
Microsoft has confirmed that the August 2025 Windows security updates are breaking reset and recovery operations on systems running Windows…
A newly identified Android phishing campaign is aggressively targeting Indian users by masquerading as the legitimate PM Surya Ghar: Muft…
Aug 19, 2025Ravie LakshmananVulnerability / Cyber Espionage A new exploit combining two critical, now-patched security flaws in SAP NetWeaver has…
The Washington Post is investigating a cyberattack on the email accounts of some of its journalists, a source familiar with…