China has officially introduced a controversial national cyber ID system, despite concerns from some experts and netizens over privacy and…
A sophisticated zero-day exploitation script targeting SAP systems has emerged in the cybersecurity landscape, demonstrating advanced remote code execution capabilities…
Flight Centre’s Corporate travel division has elevated observability from a technical tool to a strategic platform that supports its productivity…
The US Federal Communications Commission said on Wednesday it plans to adopt rules to bar companies from connecting undersea submarine…
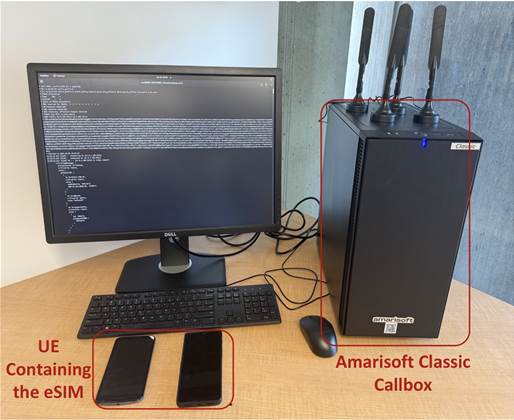
A security study has unearthed security concerns for travel electronic subscriber identity modules (eSIMs), showing that many providers route user…
A coordinated international operation has hit the infrastructure of a pro-Russian cybercrime network linked to a string of denial of…
TPG Telecom has revealed that iiNet’s order management system was breached by an unknown attacker who abused legitimate credentials to…
Microsoft on Friday said it will stop using China-based engineers to provide technical help to the US military after a…
Keeper Security has announced the release of a new global survey report from Enterprise Management Associates (EMA), Beyond the Vault: Elevating…
Security alerts from tech companies are supposed to warn us when something might be amiss—but what if the alerts themselves…
Singapore is dealing with a “serious” cyberattack against its critical infrastructure by a highly sophisticated entity linked by industry experts…
Cybersecurity researchers have uncovered a sophisticated campaign where threat actors leverage pirated game downloads to distribute HijackLoader, a modular malware…