The privacy watchdog has launched an investigation after Louis Vuitton Hong Kong suffered a data breach that compromised the personal…
Singapore has made a rare move to identify the UNC3886 cyberthreat group that it says is attacking local critical infrastructure….
Pakistan’s National Cyber Emergency Response Team (NCERT) has issued a high-alert advisory to 39 key ministries and institutions, warning of…
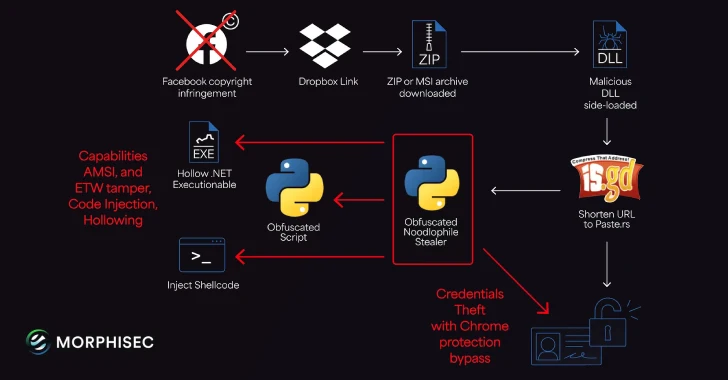
Aug 18, 2025Ravie LakshmananMalware / Enterprise Security The threat actors behind the Noodlophile malware are leveraging spear-phishing emails and updated…
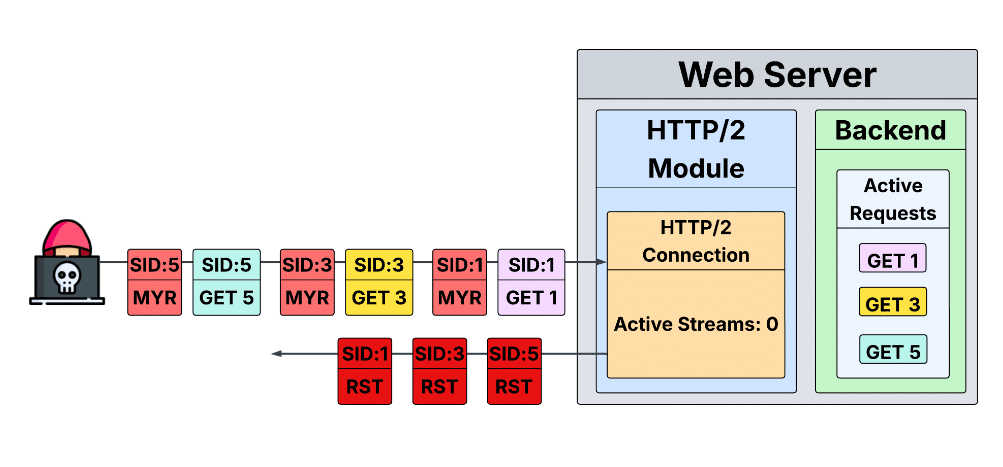
A new HTTP/2 denial of service (DoS) vulnerability that circumvents mitigations put in place after 2023’s “Rapid Reset” vulnerability is…
Fewer than one in every 10 eligible Malaysians has signed up for a digital identity card in a flat rejection…
AI for Cybersecurity: Building Trust in Your Workflows Pierluigi Paganini August 18, 2025 In cybersecurity, speed matters, but trust is…
The moment when you realize what was previously impossible is now trivial I just wrote a new piece about the…
Microsoft accused Chinese state-sponsored hackers of using flaws in its SharePoint document management software in a hacking campaign that has…
The source code for version 3 of the ERMAC Android banking trojan has been leaked online, exposing the internals of the malware-as-a-service platform…
Cybersecurity researchers have uncovered a sophisticated campaign where threat actors leverage a Microsoft Help Index File (.mshi) to deploy the…
Microsoft warns that a fake ChatGPT desktop app was used to deliver PipeMagic malware, linked to ransomware attacks exploiting a…