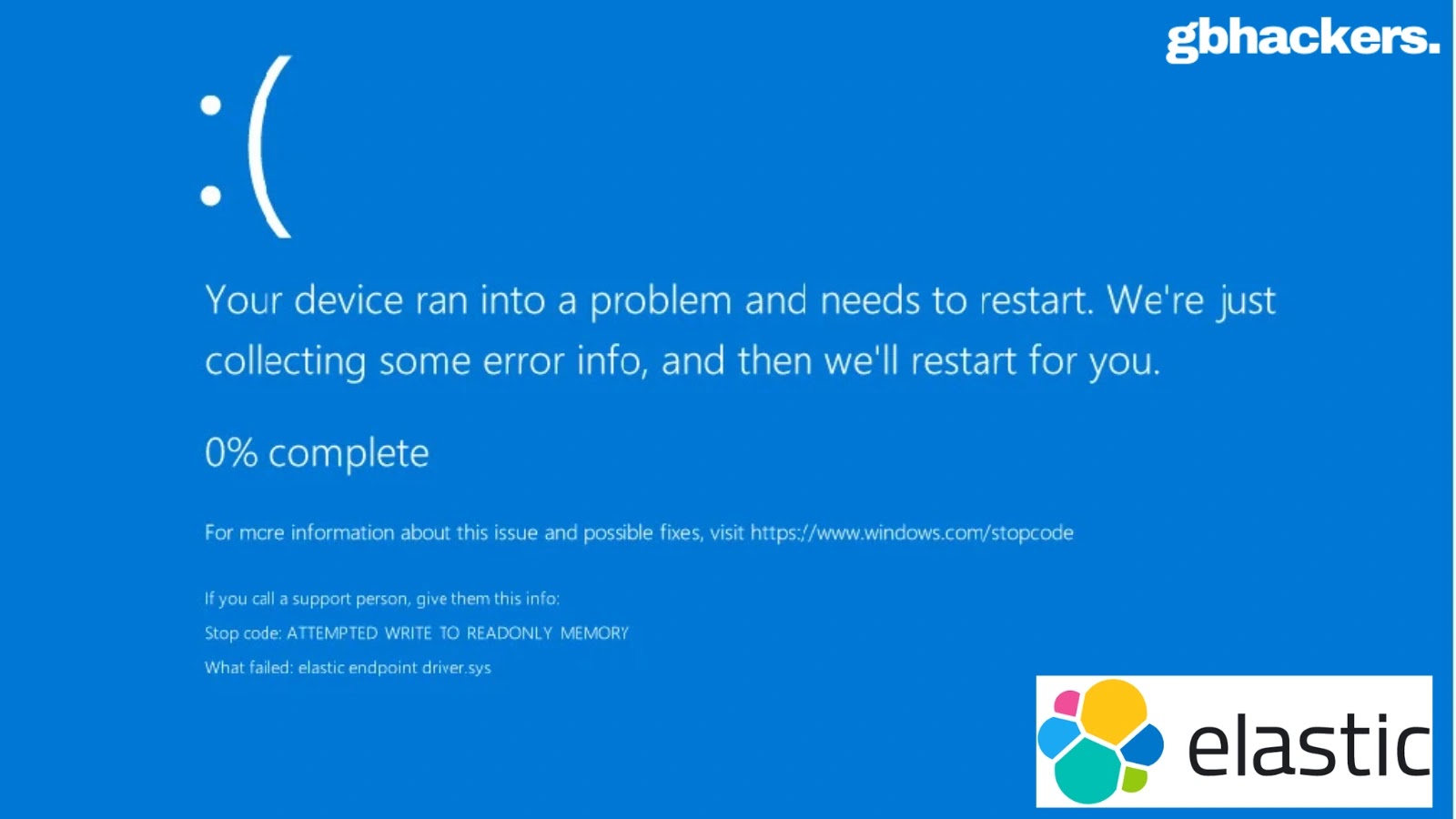
AshES Cybersecurity has disclosed a severe zero-day vulnerability in Elastic’s Endpoint Detection and Response (EDR) software that transforms the security…
Personal finance Increased competition in financial services and the desire among customers for a more tailored experience has meant personalised…
Zero trust frameworks challenge traditional perimeter-based security models by adopting a “never trust, always verify” approach. Unlike legacy security systems,…
When Google first announced in early 2020 its plans to end support for third party cookies, it quickened a growing…
Helping hands At Seven West Media, AI has become an integral tool for senior graphic designer Jessica Hankinson and her…
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malware…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: WinRAR zero-day was exploited by…
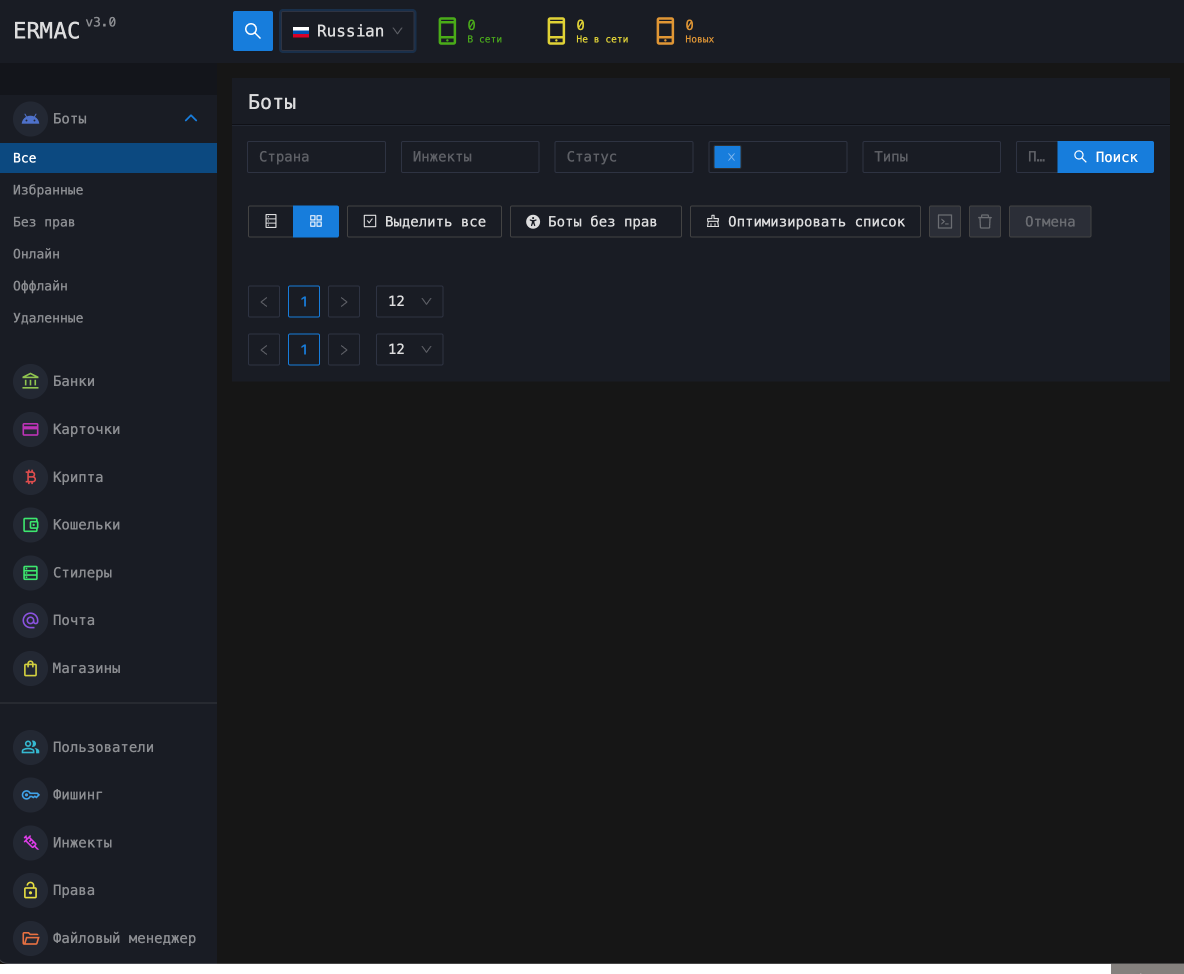
ERMAC 3.0 Source Code Leak Reveals Expanding Threat Pierluigi Paganini August 17, 2025 Hunt.io got ERMAC 3.0’s source code, showing…
CISA in collaboration with international partners, has released comprehensive guidance, titled “Foundations for OT Cybersecurity: Asset Inventory Guidance for Owners…
A newly discovered zero-day vulnerability in Elastic’s Endpoint Detection and Response (EDR) solution allows attackers to bypass security measures, execute…
A newly discovered zero-day vulnerability in Elastic’s Endpoint Detection and Response (EDR) solution allows attackers to bypass security measures, execute…
Accenture is to buy Australian cybersecurity firm CyberCX in its largest-ever deal in the sector, with the Australian Financial Review…