ChatGPT’s Voice mode is already pretty good, but OpenAI is working on a new feature that will allow you to control…
The Las Vegas Metropolitan Police Department announced the arrest of eight individuals, including a top Israeli official, in a sting…
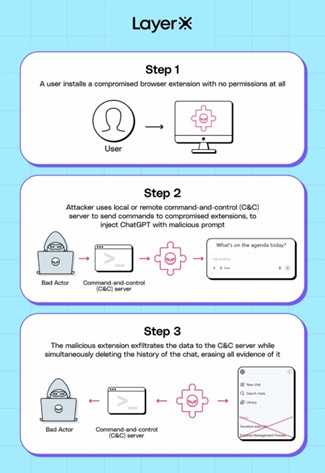
Man-in-the-Prompt: The invisible attack threatening ChatGPT and other AI systems Pierluigi Paganini August 16, 2025 Man-in-the-Prompt: a new threat targeting…
Researchers at Hunt.io have made a significant discovery in the cybersecurity field by obtaining and analyzing the complete source code…
F5 Networks has disclosed a new HTTP/2 vulnerability affecting multiple BIG-IP products that could allow remote attackers to launch denial-of-service…
Google has awarded a record-breaking $250,000 bounty to security researcher “Micky” for discovering a critical remote code execution vulnerability in…
Security researchers have uncovered a severe pre-authentication command injection vulnerability in Fortinet’s FortiSIEM platform that allows attackers to completely compromise…
A critical vulnerability in the Microsoft Web Deploy tool could allow authenticated attackers to execute remote code on affected systems. …
Introduction In today’s fast-evolving threat landscape, traditional breach detection systems often fall short in providing early warnings. CISOs are under…
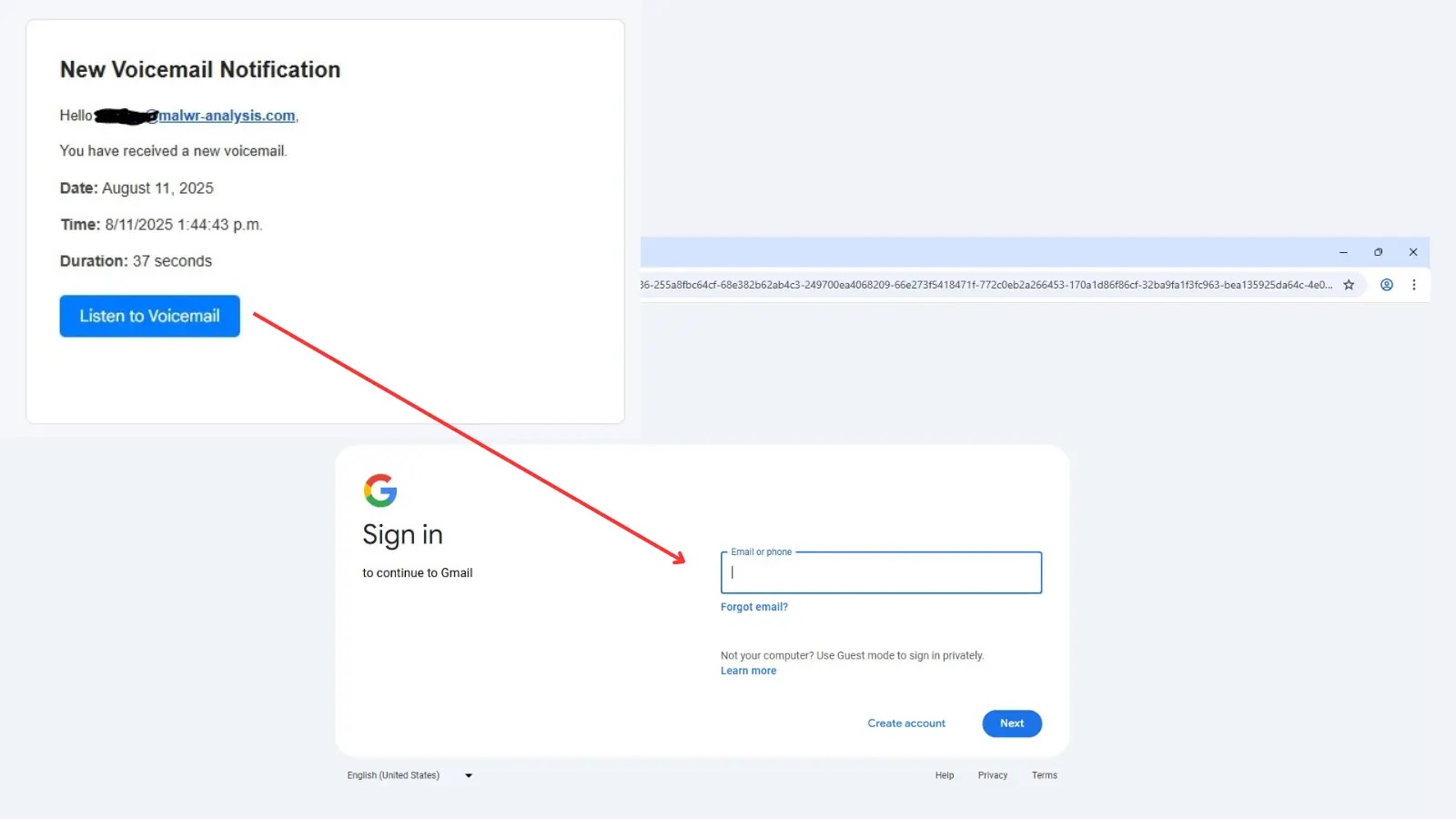
A sophisticated new phishing campaign targeting Gmail users through a multi-layered attack that uses legitimate Microsoft Dynamics infrastructure to bypass…
Rotherham hacker Al-Tahery Al-Mashriky jailed for 20 months after global cyberattacks, stealing millions of logins and targeting government websites. When…
Security researchers have uncovered four serious vulnerabilities in ImageMagick, one of the world’s most widely used open-source image processing software…