CloudSEK uncovered a Pakistan-based family cybercrime network that spread infostealers via pirated software, netting $4.67M and millions of victims. The…
Aug 16, 2025Ravie LakshmananAndroid / Malware Cybersecurity researchers have detailed the inner workings of an Android banking trojan called ERMAC…
WIRED copublished an investigation this week with The Markup and CalMatters showing that dozens of data brokers have been hiding…
Cisco Talos researchers have uncovered a sophisticated Chinese-speaking advanced persistent threat (APT) group, designated UAT-7237, that has been actively targeting…
EncryptHub abuses Brave Support in new campaign exploiting MSC EvilTwin flaw Pierluigi Paganini August 16, 2025 EncryptHub actor exploits Windows…
Taiwan Web Infrastructure targeted by APT UAT-7237 with custom toolset Pierluigi Paganini August 16, 2025 APT group UAT-7237, linked to…
Cybersecurity researchers from watchTowr Labs have published a comprehensive technical analysis of a critical pre-authentication command injection vulnerability affecting Fortinet…
Aug 16, 2025Ravie LakshmananMalware / Vulnerability The threat actor known as EncryptHub is continuing to exploit a now-patched security flaw…
Here’s a different way to think about the change coming to the workforce and economy from AI. Imagine everyone in…
Palo Alto Networks has published an extensive malware analysis tutorial detailing the dissection of a sophisticated .NET-based threat that delivers…
The cybersecurity landscape faces a new sophisticated threat as the Crypto24 ransomware group demonstrates an alarming evolution in attack methodology,…
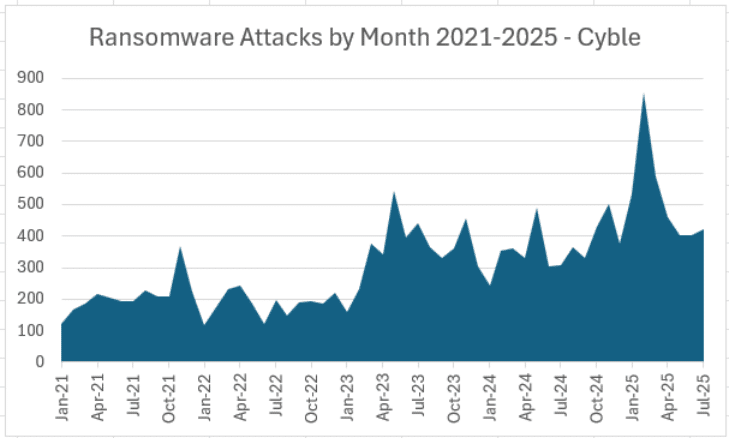
Qilin continues to stake a claim as the top ransomware group in the wake of the decline of RansomHub earlier…