Fake Home Office emails target the UK Visa Sponsorship System, stealing logins to issue fraudulent visas and run costly immigration…
Aug 14, 2025Ravie LakshmananThreat Intelligence / Linux Japan’s CERT coordination center (JPCERT/CC) on Thursday revealed it observed incidents that involved…
Intel’s woes have continued this week, after its CEO met with US president Donald Trump. Trump previously called for the…
Threat actors are leveraging a Unicode character to make phishing links appear like legitimate Booking.com links in a new campaign…
A critical security vulnerability in Apache Tomcat’s HTTP/2 implementation has been discovered, enabling attackers to launch devastating denial-of-service (DoS) attacks…
Why Businesses Must Upgrade to Quantum-Safe Encryption Before It’s Too Late Cybersecurity has always had to keep pace with the…
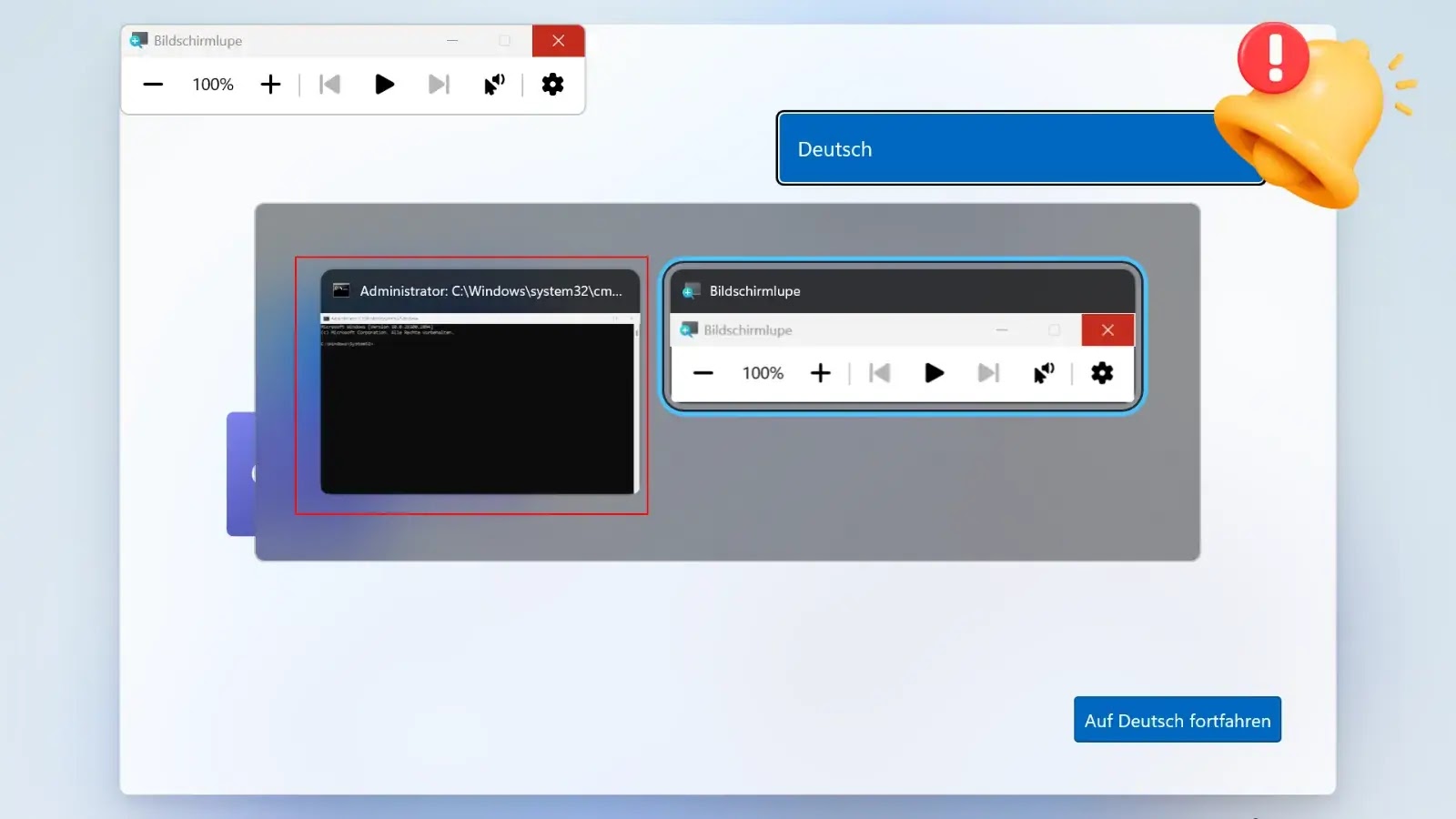
A newly documented vulnerability in Windows’ Out-of-Box-Experience (OOBE) allows users to bypass security restrictions and gain full administrative access to…
A surge in brute-force attempts targeting Fortinet SSL VPNs that was spotted earlier this month could be a portent of…
The House of Commons of Canada is currently investigating a data breach after a threat actor reportedly stole employee information…
Adobe has released a comprehensive security update addressing 60 critical vulnerabilities across 13 of its flagship products as part of…
With 7.9 billion email accounts worldwide and 4.3 billion active users, emails now play an essential role in fraud detection and identity verification….
Intezer’s Research Team has uncovered a new, low-detection variant of the FireWood backdoor, a sophisticated Linux-based remote access trojan (RAT)…