Artificial intelligence coding assistants, designed to boost developer productivity, are inadvertently causing massive system destruction. Researchers report a significant spike…
The AhnLab Security Intelligence Center (ASEC) has uncovered fresh instances of proxyware distribution by threat actors leveraging deceptive advertising on…
Brivo a strategic partnership with Envoy. The integration brings Envoy’s workplace platform, designed to connect people, spaces, and data, into…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two high-risk vulnerabilities in N-able N-central to its Known Exploited…
Manpower data breach impacted 144,180 individuals Pierluigi Paganini August 14, 2025 Global staffing and workforce solutions firm Manpower reports a…
Out-of-bounds read and write vulnerabilities represent critical security vulnerabilities that occur when software accesses memory locations beyond the allocated boundaries…
A new method has been identified to exploit Windows Out-of-Box-Experience (OOBE) that bypasses existing protections and grants administrative command line…
A severe security vulnerability has been discovered in a popular WordPress plugin used by over 70,000 websites worldwide, potentially exposing…
The Zelle lawsuit 2025 is making headlines as New York Attorney General Letitia James takes legal action against Early Warning…
A sophisticated cybercriminal organization known as VexTrio has been orchestrating a massive fraud empire through deceptive CAPTCHA robots and malicious…
Security researchers have disclosed critical vulnerabilities in Xerox FreeFlow Core that enable unauthenticated remote attackers to execute arbitrary code on…
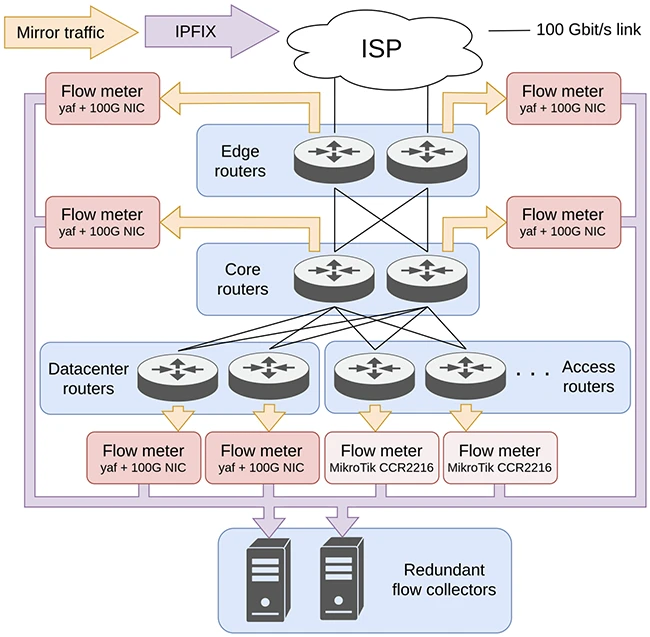
Flow monitoring tools are useful for tracking traffic patterns, planning capacity, and spotting threats. But many off-the-shelf solutions come with…