The Cybersecurity and Infrastructure Security Agency (CISA) has issued urgent alerts regarding two critical vulnerabilities in N-able N-Central that are…
Learn how AI technologies can be applied to enhance security, create safe and responsible applications, develop intelligent agents, and improve…
Aug 14, 2025Ravie LakshmananVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added two security…
Critical security vulnerabilities in Microsoft Exchange Server enable attackers to perform spoofing and tampering attacks over network connections. The vulnerabilities…
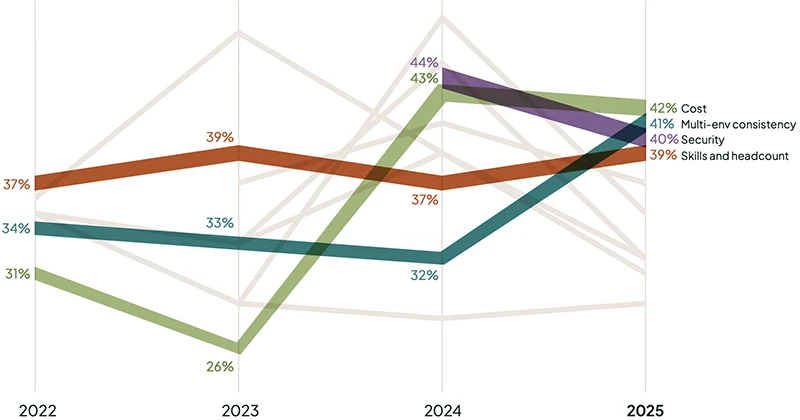
AI is changing how enterprises approach Kubernetes operations, strategy, and scale. The 2025 State of Production Kubernetes report from Spectro…
The rise of the ‘hyper connected’ consumer is transforming retail and prompting sector leaders to implement secure, responsive networks to…
A critical security vulnerability in GitHub Copilot and Visual Studio Code has been discovered that allows attackers to achieve remote…
GitLab has released emergency security patches addressing multiple critical vulnerabilities that could enable attackers to perform account takeovers and execute…
Google Gemini’s one of the most powerful features is Deep Research, but up until now, it has been strictly limited…
U.S. CISA adds Microsoft Internet Explorer, Microsoft Office Excel, and WinRAR flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini…
Indian IT services company Infosys will take a 75 percent stake in Versent Group, a wholly owned unit of Telstra,…
OpenAI is slowly addressing all concerns around GPT-5, including rate limits and now its personality, which has been criticized for…