Security researchers at Cymulate Research Labs have discovered a critical zero-click NTLM credential leakage vulnerability that successfully bypasses Microsoft’s security…
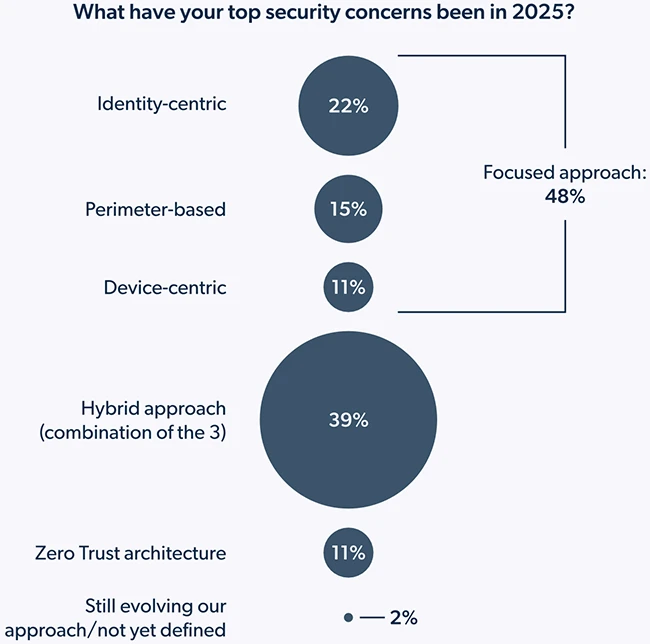
Most organizations are juggling too many tools, struggling with security blind spots, and rushing into AI adoption without governance, according…
Microsoft’s August 2025 Patch Wednesday collection of security updates for its software products contains a fix for a vulnerability rated…
A new study from Dragos and Marsh McLennan puts hard numbers on the global financial risk tied to OT cyber…
Network infrastructure has historically been treated as a passive connectivity tool by state government agencies, but that perspective is now…
SAP fixed 26 flaws in August 2025 Update, including 4 Critical Pierluigi Paganini August 13, 2025 SAP’s August 2025 Patch…
August 2025 Patch Tuesday fixes a Windows Kerberos Zero-Day Pierluigi Paganini August 12, 2025 Microsoft Patch Tuesday security updates for…
Hackers have released stolen data belonging to US insurance giant Allianz Life, exposing 2.8 million records with sensitive information on…
Microsoft’s August Patch Tuesday fixes 107 vulnerabilities, including 13 critical RCE flaws, impacting Windows, Office, Azure, and more, urging fast…
Claude Sonnet 4 has been upgraded, and it can now remember up to 1 million tokens of context, but only…
Microsoft today released updates to fix more than 100 security flaws in its Windows operating systems and other software. At…
OpenAI has begun updating its pricing page to include a new plan called ‘ChatGPT Go.’ It costs 399 INR (Indian…