The threat actor known as ShinyHunters has publicly disclosed what they claim is a covert seizure of BreachForums, a notorious…
The global financial impact from catastrophic cyber events that disrupt operational technology could near $330 billion on an annual basis,…
Over 3,300 Citrix NetScaler devices remain unpatched against a critical vulnerability that allows attackers to bypass authentication by hijacking user…
Zoom has disclosed a critical vulnerability affecting multiple Windows-based clients, potentially allowing attackers to escalate privileges and compromise user systems….
Cybersecurity researchers at GreyNoise have detected an alarming surge in brute-force attacks against Fortinet SSL VPN systems, with over 780…
A new report from Bitdefender reveals the Russian-linked hacking group Curly COMrades is targeting Eastern Europe with a new backdoor…
The next time you shake your head at another online scam and vow that you’d never fall for it, remember…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Hackers have…
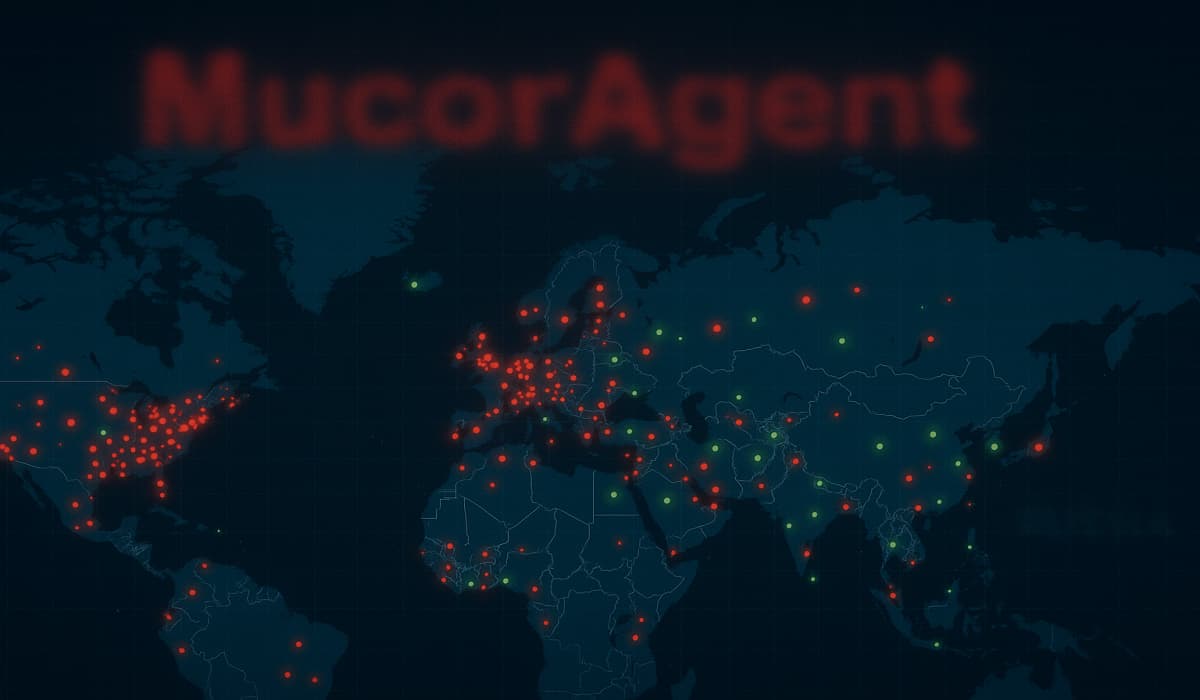
A new cyber-espionage threat group has been using a new backdoor malware that provides persistent access through a seemingly inactive scheduled…
Ivanti has released critical security updates addressing multiple high and medium-severity vulnerabilities across its Connect Secure, Policy Secure, and Zero…
Statistics shared by the World Economic Forum in 2024 show healthcare and finance to be the top two industries most targeted by…
Ivanti has released critical security updates addressing multiple vulnerabilities in its Connect Secure, Policy Secure, and ZTA Gateway products that…