An urgent security update has been released for Xerox FreeFlow Core software, addressing two critical vulnerabilities that could allow attackers…
It’s all part of the ongoing tussle between the cheat developers and games companies, which spend money on developing anti-cheat…
Security researchers at AmberWolf have uncovered critical vulnerabilities in leading Zero Trust Network Access (ZTNA) solutions from major cybersecurity vendors,…
ESET researchers have discovered a previously unknown vulnerability in WinRAR, exploited in the wild by Russia-aligned group RomCom. If you…
Smart Buses flaws expose vehicles to tracking, control, and spying Pierluigi Paganini August 11, 2025 Researchers showed how hackers can…
Over 29,000 Exchange servers exposed online remain unpatched against a high-severity vulnerability that can let attackers move laterally in Microsoft…
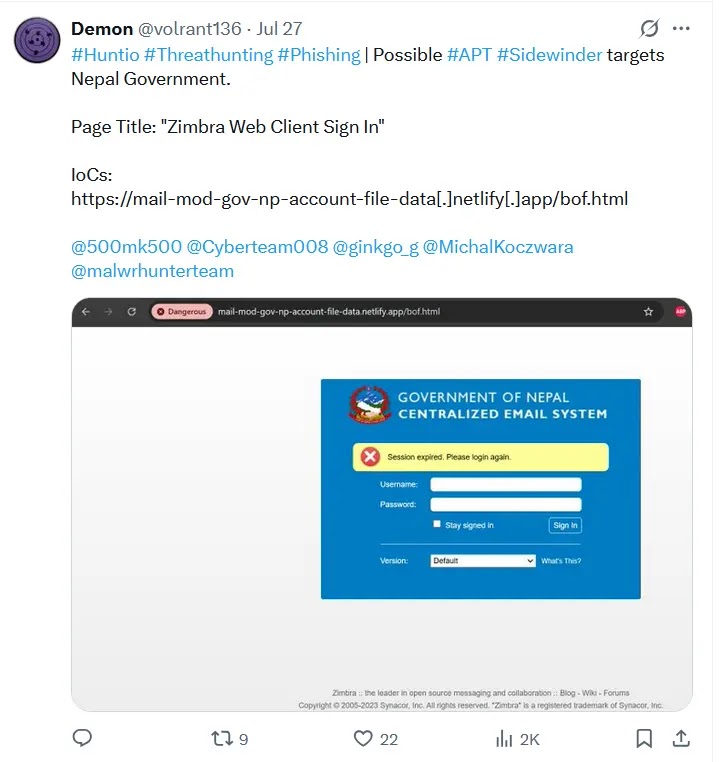
APT Sidewinder, a persistent threat actor believed to originate from South Asia, has launched a sophisticated credential harvesting campaign targeting…
A malware operation has surfaced in the context of a complex cyber threat landscape, using tainted Google Ads to pose…
London, United Kingdom, August 11th, 2025, CyberNewsWire New Heimdal study reveals how tool sprawl creates blind spots, with over half…
SSHAmble is a powerful open-source reconnaissance tool designed to identify and exploit vulnerabilities in SSH implementations across internet-facing systems. Presented…
A vulnerability in Microsoft Windows’ Remote Procedure Call (RPC) protocol has been discovered that allows attackers to manipulate core system…
Businesses have long chased the promise of a single customer view. As far back as 1999, a group of suppliers,…