Westpac is embracing event-driven automation and AIOps as part of a multi-year infrastructure automation program underpinned by Ansible. Westpac’s Sean…
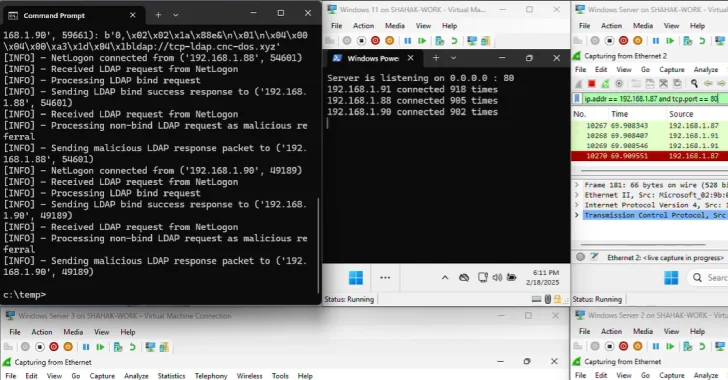
Aug 10, 2025Ravie LakshmananVulnerability / Network Security A novel attack technique could be weaponized to rope thousands of public domain…
Microsoft has raised the total potential rewards for its Zero Day Quest bug bounty program from US$4 million to US$5…
Aug 10, 2025Ravie LakshmananVulnerability / Network Security A novel attack technique could be weaponized to rope thousands of public domain…
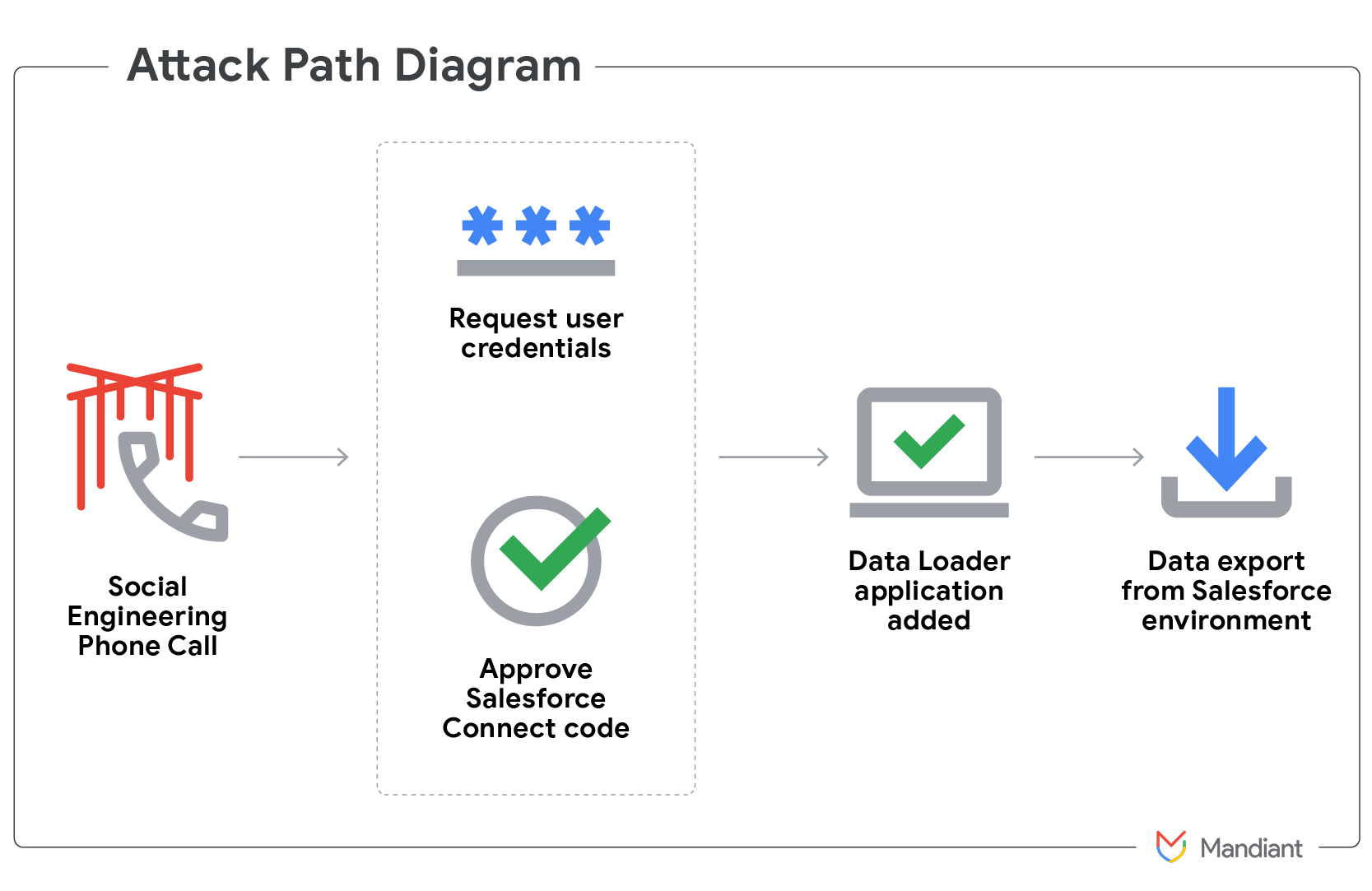
Google confirms Salesforce CRM breach, faces extortion threat Pierluigi Paganini August 10, 2025 Google disclosed a Salesforce Customer Relationship Management…
A cyberattack on Bouygues Telecom exposed data for 6.4 million customers. Find out what information was compromised and what you…
AI is transforming the way work gets done across industries. But while it improves business efficiencies, it also arms cybercriminals…
Aug 09, 2025Ravie LakshmananVulnerability / Hardware Security Cybersecurity researchers have uncovered multiple security flaws in Dell’s ControlVault3 firmware and its…
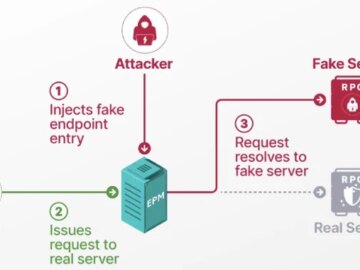
Aug 10, 2025Ravie LakshmananVulnerability / Endpoint Security Cybersecurity researchers have presented new findings related to a now-patched security issue in…
Telecommunications service providers (TSP) are foundational to the functioning of our modern technical society, serving as the conduit through which…
AgentFlayer is a critical vulnerability in ChatGPT Connectors. Learn how this zero-click attack uses indirect prompt injection to secretly steal…
Considering the widespread use of contactless payment systems, it’s no surprise that portable point-of-sale thefts are making a comeback. This…