As organizations increasingly rely on application programming interfaces (APIs) to facilitate communication and data exchange between software systems, these “gates”…
Critical WinRAR flaw CVE-2025-8088 exploited by Russia-linked hackers to spread RomCom malware, update to version 7.13 now to stay protected….
A critical vulnerability in OpenAI’s ChatGPT Connectors feature allows attackers to exfiltrate sensitive data from connected Google Drive accounts without…
Cybercriminals are no longer primarily focused on large enterprises. They now see small- and medium-sized businesses (SMBs) as prime targets…
August 9, 2025: A severe security vulnerability in the Linux kernel, dubbed CVE-2025-38236, has been uncovered by Google Project Zero…
In response to recent cyberattacks, the federal judiciary said its been in the process of implementing new safeguards to address…
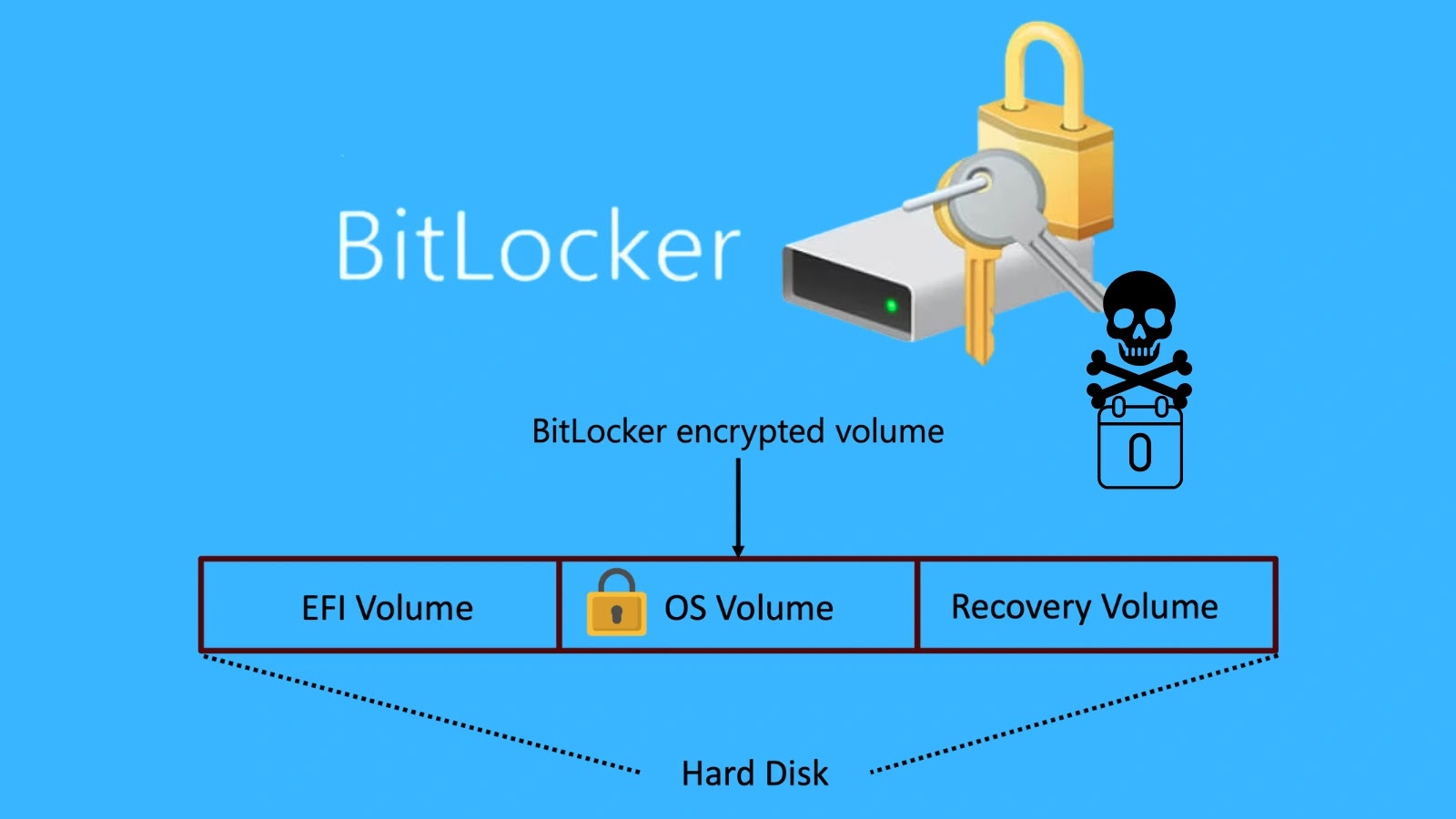
Microsoft security researchers have uncovered four critical vulnerabilities in Windows BitLocker that could allow attackers with physical access to bypass…
The cybersecurity community faces a significant threat as scanning data reveals over 28,000 unpatched Microsoft Exchange servers remain exposed on…
August 9, 2025 — A critical vulnerability in the Linux kernel, identified as CVE-2025-38236, has exposed a flaw that could…
Germany limits police spyware use to serious crimes Pierluigi Paganini August 09, 2025 Germany’s top court ruled police can use…
At DEF CON 33, security researcher Mike Weber of Praetorian Security unveiled ChromeAlone — a Chromium-based browser Command & Control…
IBM X-Force has uncovered CastleBot, a nascent malware framework operating as a Malware-as-a-Service (MaaS) platform, enabling cybercriminals to deploy a…