The government is on a mission to make the UK an artificial intelligence (AI) superpower, by accelerating the adoption of…
Microsoft announced that it will phase out the Microsoft Lens PDF scanner app for Android and iOS devices starting in September….
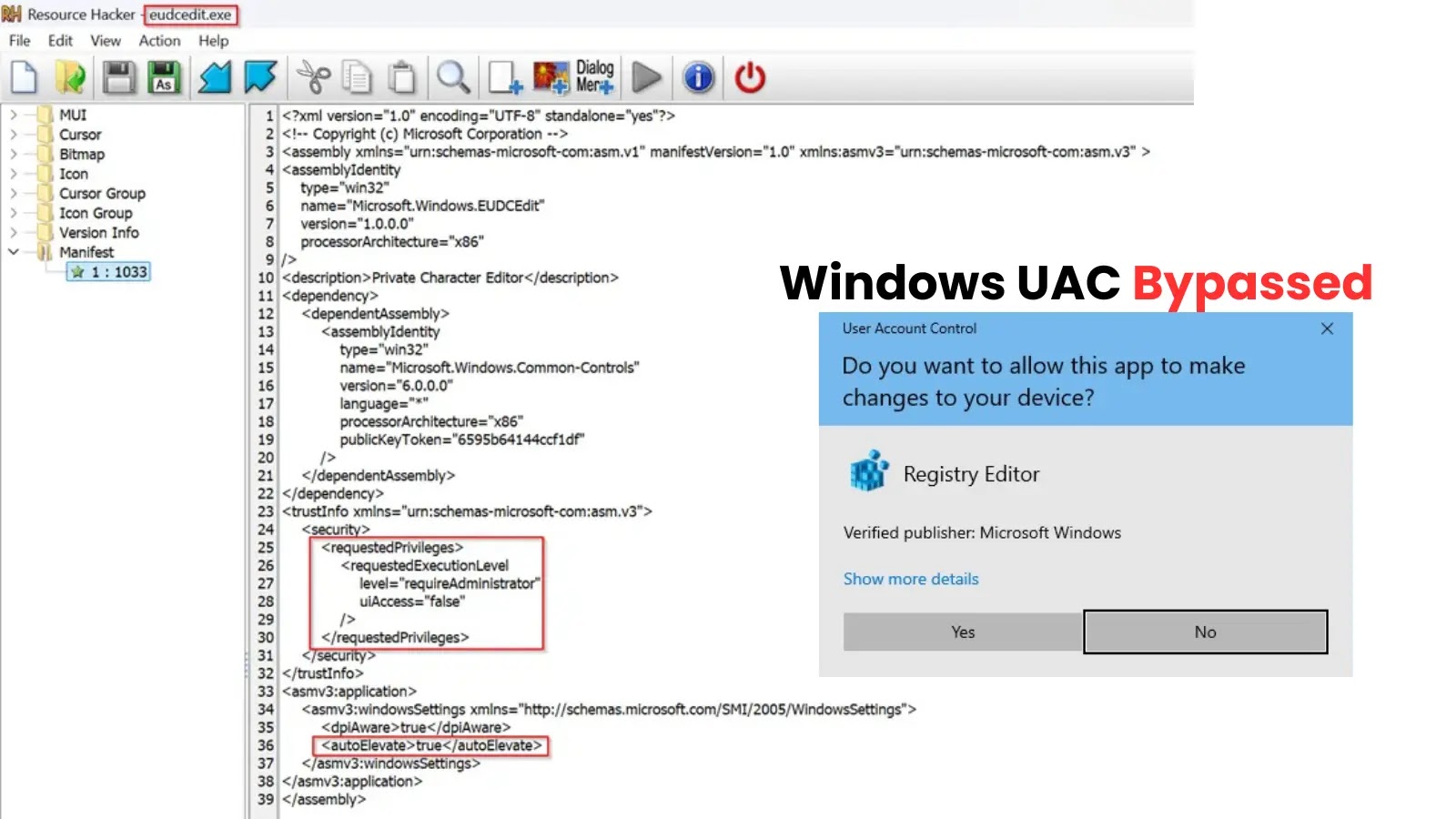
A sophisticated new technique that exploits the Windows Private Character Editor to bypass User Account Control (UAC) and achieve privilege…
The Cybersecurity and Infrastructure Security Agency (CISA) has released ten industrial control systems (ICS) advisories on August 7, 2025, highlighting…
OpenAI has updated its large language model (LLM) in ChatGPT to GPT-5, which it says takes a significant step towards…
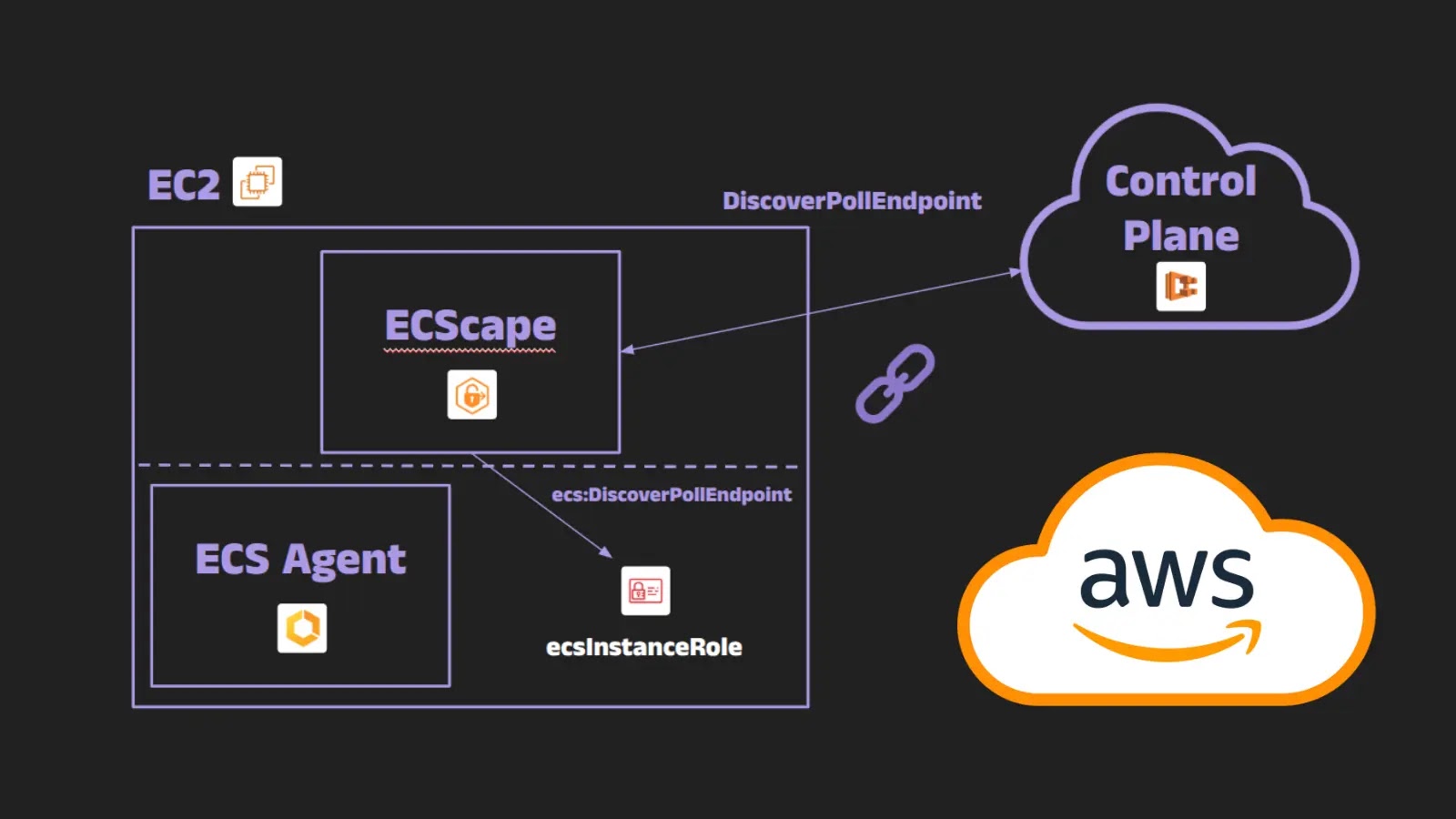
A sophisticated technique dubbed “ECScape” that allows malicious containers running on Amazon Elastic Container Service (ECS) to steal AWS credentials…
Security researchers have disclosed a critical vulnerability in Amazon Elastic Container Service (ECS) that allows malicious containers to steal AWS…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. LAS VEGAS…
In early 2025, OpenAI CEO Sam Altman made a trip to Abu Dhabi to engage in discussions with AI fund…
An unknown threat actor has stolen the sensitive personal, financial, and health information of nearly 870,000 Columbia University current and…
Cybersecurity researchers have uncovered a sophisticated malware campaign targeting the Go ecosystem through eleven malicious packages that employ advanced obfuscation…
Federal law enforcement agencies have successfully dismantled the critical infrastructure of BlackSuit ransomware, a sophisticated cybercriminal operation that has compromised…