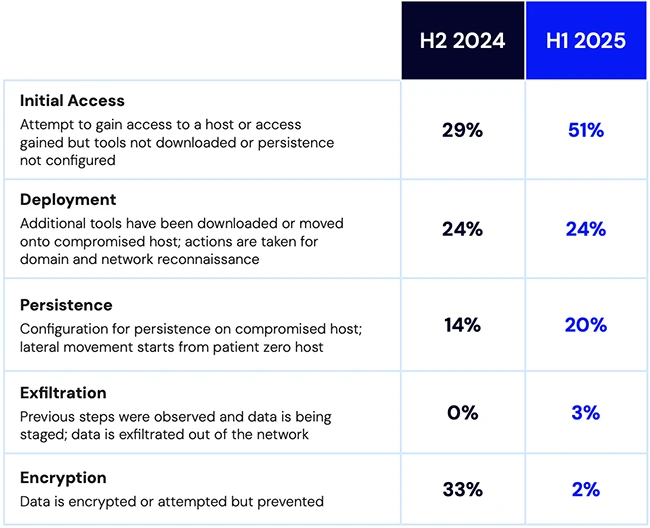
Security researchers have successfully demonstrated a sophisticated exploit of the Retbleed vulnerability, a critical CPU security flaw that allows attackers to…
Cybercriminals are getting better at lying. That’s the takeaway from a new LevelBlue report, which outlines how attackers are using…
The Australian Information Commissioner (AIC) has filed civil penalty proceedings in the Federal Court against Singtel Optus Pty Limited and…
A new and custom firmware for the popular Flipper Zero multi-tool device is reportedly capable of bypassing the rolling code…
Here’s a look at the most interesting products from the past week, featuring releases from Black Kite, Descope, Elastic, ExtraHop,…
Optus is set to face a privacy lawsuit stemming from its 2022 data breach, with Federal Court proceedings filed by…
A new report from Accenture reveals that a staggering 97% of Australian organisations are not adequately prepared to secure their AI-driven future….
Melbourne, Australia – For too long, backups have been the weak link in IT – especially when managed by the same…
The U.S. judiciary announced plans to increase security for sensitive information on its case management system following what it described…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. LAS VEGAS…
The tables show the potential target jobs for IT workers. One sheet, which seemingly includes daily updates, lists job descriptions…
OpenAI launched its GPT-5 artificial intelligence model, the highly anticipated latest installment of a technology that has helped transform global…