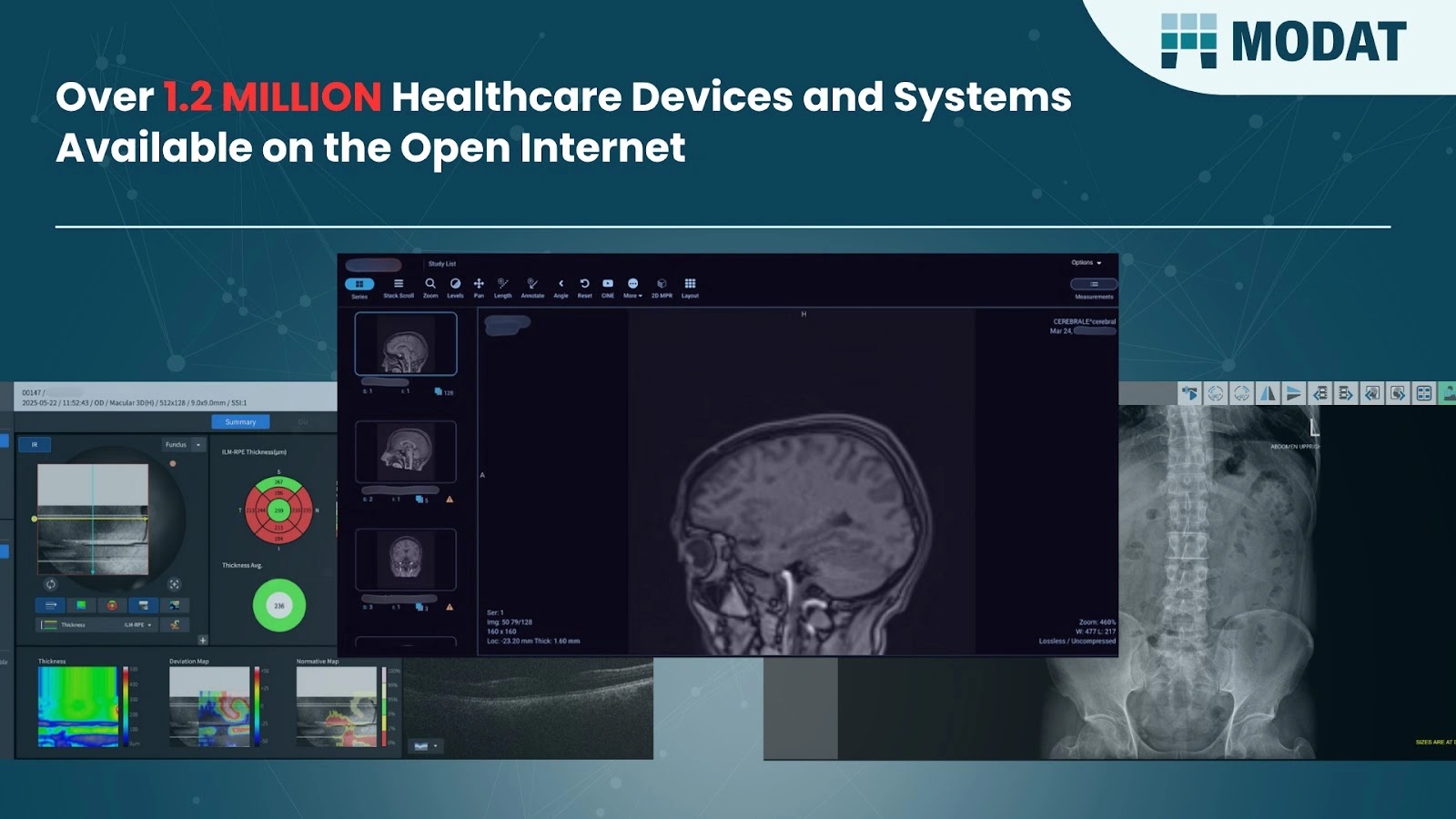
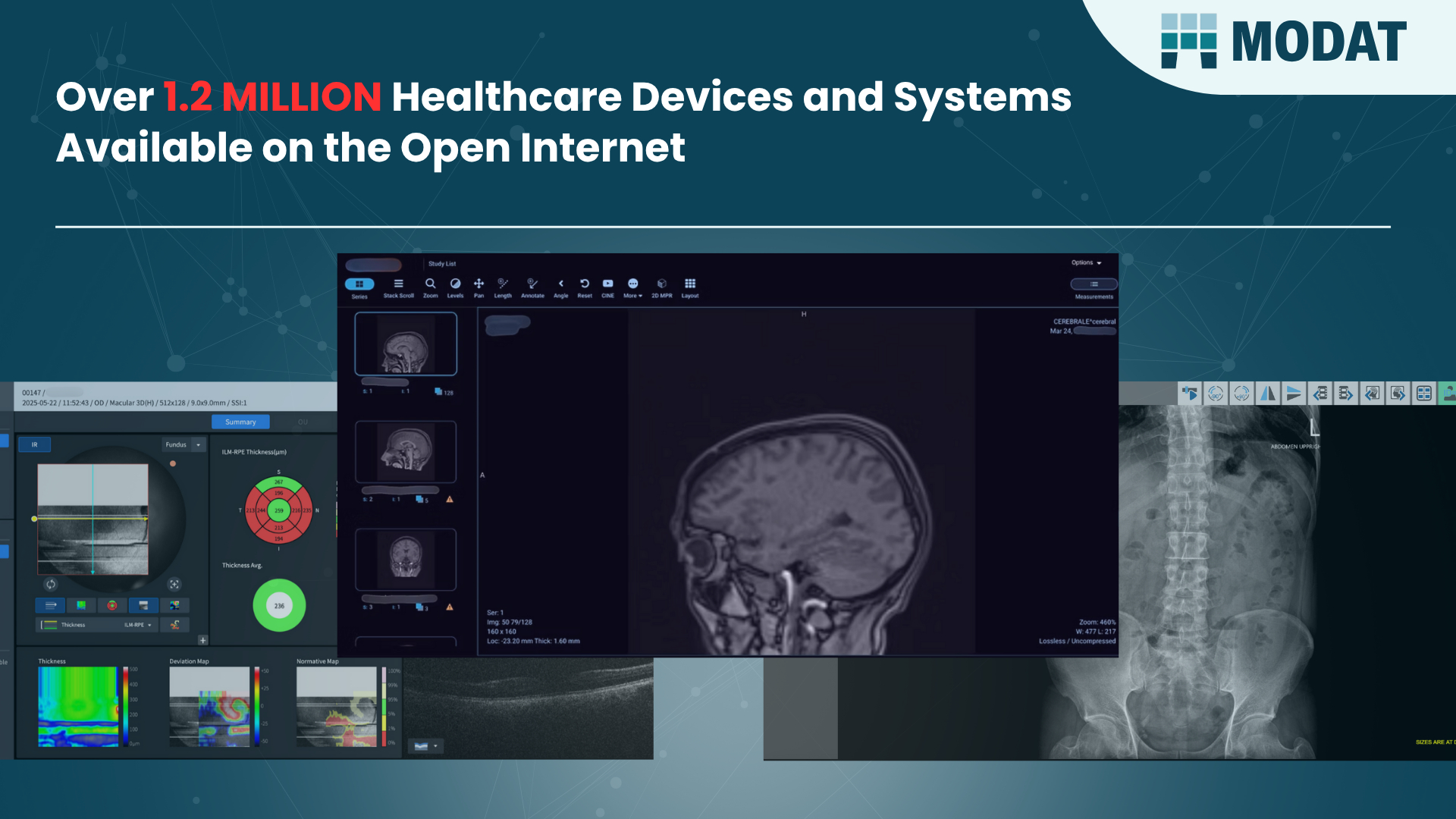
Over 1.2 million internet-connected healthcare devices and systems with exposure that endanger patient data shown in new research by European cybersecurity…
Security researchers have unveiled a sophisticated new attack technique called “Ghost Calls” that exploits popular web conferencing platforms to establish…
Black Hat USA 2025 was packed with innovation, with companies showing off tools built to get ahead of what’s coming…
How CTEM Boosts Visibility and Shrinks Attack Surfaces in Hybrid and Cloud Environments Pierluigi Paganini August 07, 2025 CTEM is…
Microsoft has warned customers to mitigate a high-severity vulnerability in Exchange Server hybrid deployments that could allow attackers to escalate…
A sophisticated attack method exploits Google’s Gemini AI assistant through seemingly innocent calendar invitations and emails. The attack, dubbed “Targeted…
Nvidia has issued a comprehensive denial regarding allegations that its graphics processing units contain backdoors, kill switches, or spyware, emphasizing…
The Hague, Netherlands, August 7th, 2025, CyberNewsWire Over 1.2 million internet-connected healthcare devices and systems with exposure that endanger patient data shown…
Aug 07, 2025The Hacker NewsDevSecOps / Supply Chain Security Python is everywhere in modern software. From machine learning models to…
Organizations using Exchange hybrid deployments should prepare for new changes taking effect over the next few months. Microsoft has announced…
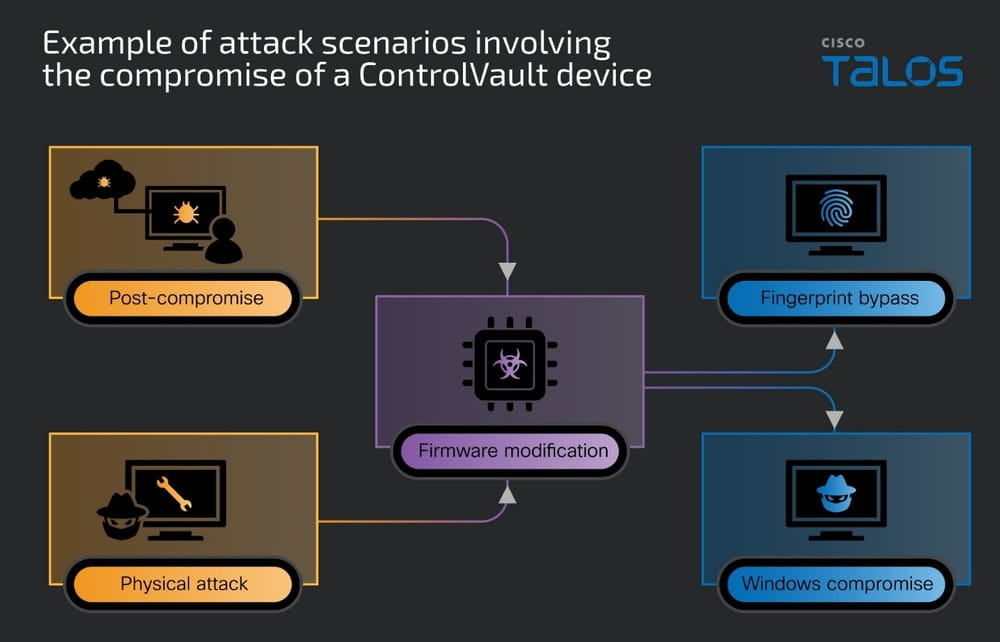
Over 100 Dell models exposed to critical ControlVault3 firmware bugs Pierluigi Paganini August 07, 2025 ReVault flaws in Dell ControlVault3…
Security researchers have unveiled a fundamental vulnerability in HTTP/1.1 that could allow attackers to hijack millions of websites, highlighting a…