Top-tier Security Operations Centers understand a fundamental truth: prevention beats reaction every time. The most successful cybersecurity tactics don’t wait…
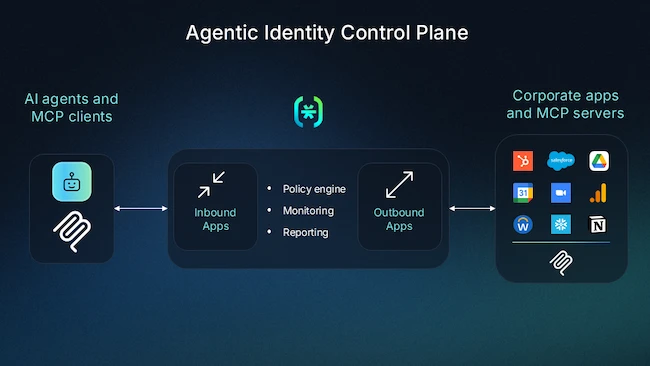
Descope launched Agentic Identity Control Plane, a solution that enables security teams to institute policy-based governance, auditing, and identity management…
Aug 06, 2025The Hacker NewsCompliance / Security Operations As the volume and sophistication of cyber threats and risks grow, cybersecurity…
Microsoft has unveiled Project Ire, an autonomous AI agent capable of reverse engineering and classifying malware at an unprecedented scale. …
The people who study nuclear war for a living are certain that artificial intelligence will soon power the deadly weapons….
Threat actors leveraged SEO poisoning techniques to manipulate Bing search results, directing users querying for “ManageEngine OpManager” to a malicious…
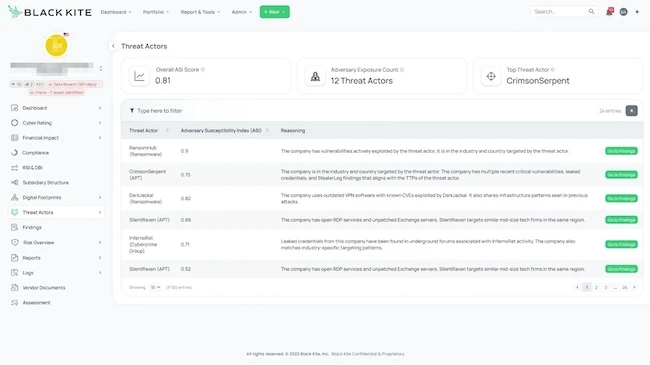
Black Kite has unveiled the Adversary Susceptibility Index (ASI), a tool designed for TPRM teams to proactively identify which vendors…
Trend Micro has warned customers to immediately secure their systems against an actively exploited remote code execution vulnerability in its…
Unit 42 researchers have identified significant overlaps between Microsoft’s reported ToolShell exploit chain targeting SharePoint vulnerabilities and a tracked activity…
Aug 06, 2025Ravie LakshmananCyber Espionage / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks…
Microsoft paid a record $17 million this year to 344 security researchers across 59 countries through its bug bounty program….
Security researchers have uncovered a highly advanced network of Chinese-speaking cybercriminal syndicates orchestrating smishing attacks that exploit digital wallet tokenization,…