Searchlight Cyber has released a new AI capability that summarizes the activity of a threat actor in its dark web…
When Technology Resets the Playing Field In 2015 I founded a cybersecurity testing software company with the belief that automated…
Cyber-criminals have gradually shifted their focus toward the high-value infrastructure that trains, tunes and serves modern artificial-intelligence models. Over the…
Cybersecurity researchers have uncovered a critical vulnerability in Cursor IDE that allows attackers to execute arbitrary system commands through a…
Cyber attackers are finding new ways in through the overlooked and unconventional network corners. Forescout’s 2025H1 Threat Review reveals a…
Cybersecurity researchers have uncovered a sophisticated search engine optimization (SEO) poisoning campaign that exploited Bing search results to distribute Bumblebee…
Most security teams believe they can act quickly when a threat emerges. But many don’t trust the very data they…
My friend Marcus Hutchins put out a long, well-written, and entertaining piece about all the reasons he thinks AI is…
Microsoft has announced the return of its groundbreaking Zero Day Quest, the largest public hacking event in history, offering unprecedented…
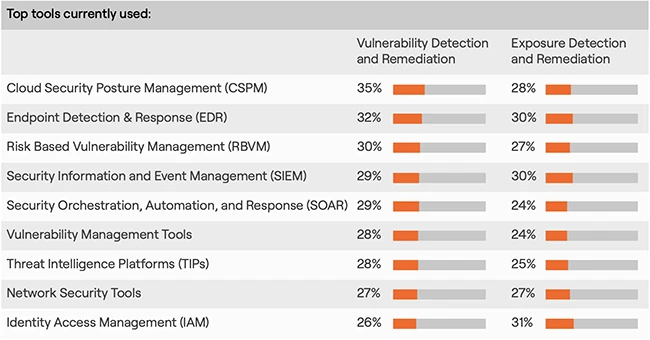
90% of cyber leaders find managing cyber risks harder today than five years ago, mainly due to the explosion of…
Researchers at Cisco’s Talos Intelligence have uncovered a vulnerability chain in security hardware used by IT maker Dell, which can…
A wide range of vulnerabilities affects millions of Dell laptops used by government agencies, cybersecurity professionals, and enterprises worldwide. The…