A set of firmware vulnerabilities affecting 100+ Dell laptop models widely used in government settings and by the cybersecurity industry…
The apparently disjointed response from Iranian hackers to the 12-day conflict with Israel in June actually demonstrated a significant degree…
A critical vulnerability in Cursor IDE, the rapidly growing AI-powered development environment, enables persistent remote code execution through manipulation of…
Cybersecurity firm CTM360 has uncovered an ongoing malicious operation dubbed “ClickTok,” specifically targeting TikTok Shop users worldwide through a dual-pronged…
Manifest Cyber introduced Manifest AI Risk, the latest module part of the Manifest Platform, designed to help security and compliance…
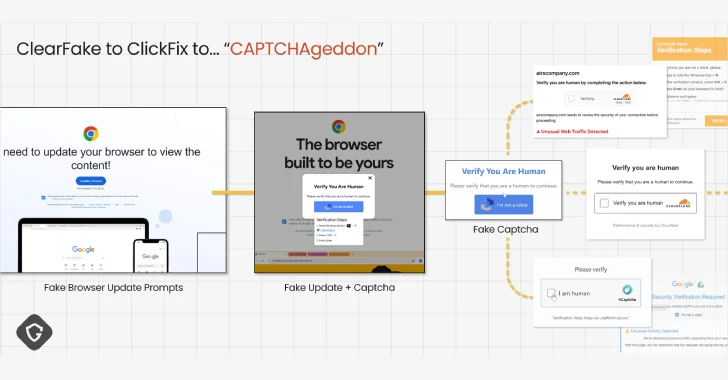
Aug 05, 2025Ravie LakshmananSocial Engineering / Malware A combination of propagation methods, narrative sophistication, and evasion techniques enabled the social…
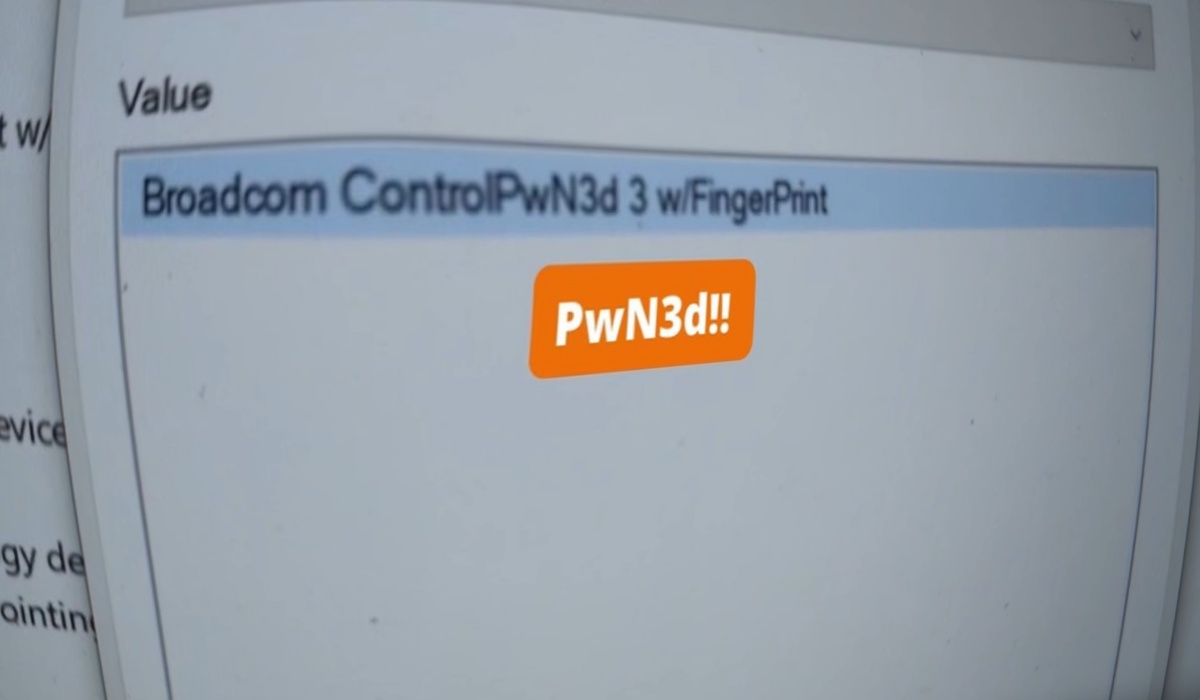
Over 100 models of Dell laptop PCs across the enterprise-centric Lattitude and Precision ranges, and many thousands of individual devices,…
Cybersecurity is about staying one step ahead. The security of business assets hinges on proactive threat detection and rapid response…
The North Korean state-sponsored group Kimsuky, also known as APT43, Thallium, and Velvet Chollima, has been accused of launching a…
Cybersecurity giant Cisco has found serious security vulnerabilities in more than 100 Dell laptop models, putting tens of millions of…
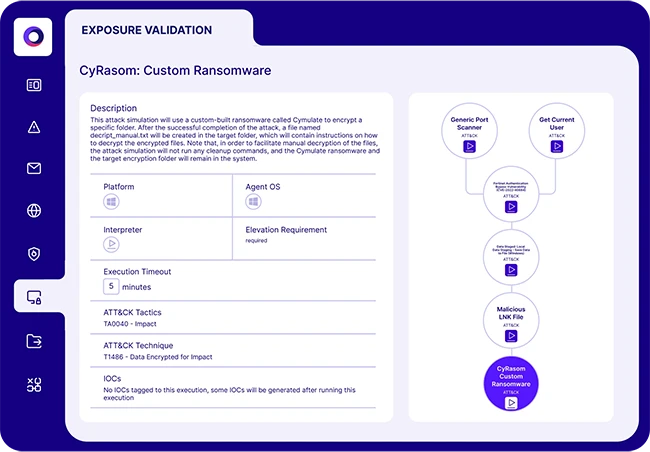
Cymulate announced the new Cymulate Exposure Management Platform, which validates, prioritizes and optimizes the entire security ecosystem – continuously. The…
SonicWall has issued an urgent security advisory following a significant increase in cyber incidents targeting its Gen 7 SonicWall firewalls…