When was the last time you revisited your organization’s email security practices? Is your current software up to the task…
Cisco Systems has disclosed a data breach that compromised basic profile information of users registered on Cisco.com following a successful…
A sophisticated North Korean cryptocurrency theft campaign has resurfaced with renewed vigor, weaponizing twelve malicious NPM packages to target developers…
A sophisticated phishing campaign attributed with medium confidence to the Pakistan-linked APT36 group, also known as Transparent Tribe or Mythic…
Cisco has disclosed that cybercriminals stole the basic profile information of users registered on Cisco.com following a voice phishing (vishing)…
North Korean state-sponsored cyber-espionage group Kimsuky has unveiled a sophisticated new campaign targeting South Korean entities through malicious Windows shortcut…
Veracode Threat Research has uncovered a sophisticated North Korean cryptocurrency theft operation that continues to evolve, building on campaigns previously…
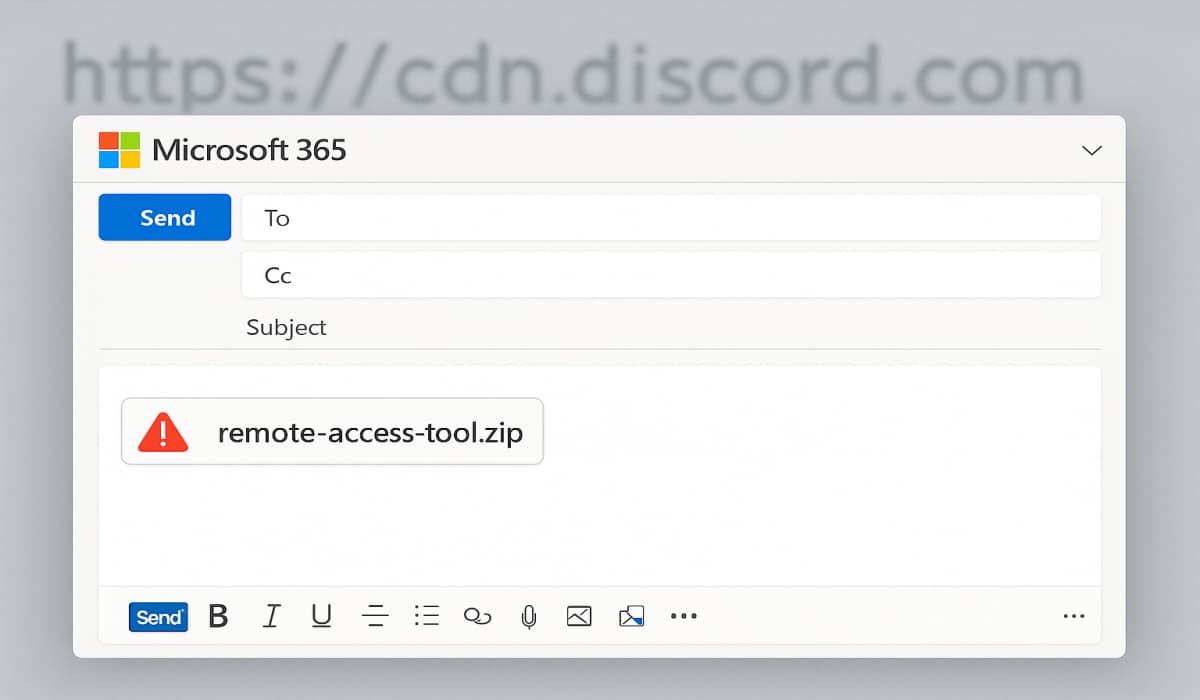
In a new threat discovered by cybersecurity firm Sublime Security, which was observed on the Microsoft 365 email platform, hackers…
In SaaS security conversations, “misconfiguration” and “vulnerability” are often used interchangeably. But they’re not the same thing. And misunderstanding that…
Exposed Without a Breach: The Cost of Data Blindness Pierluigi Paganini August 05, 2025 These are in plain sight without…
SonicWall has warned customers to disable SSLVPN services due to ransomware gangs potentially exploiting an unknown security vulnerability in SonicWall…
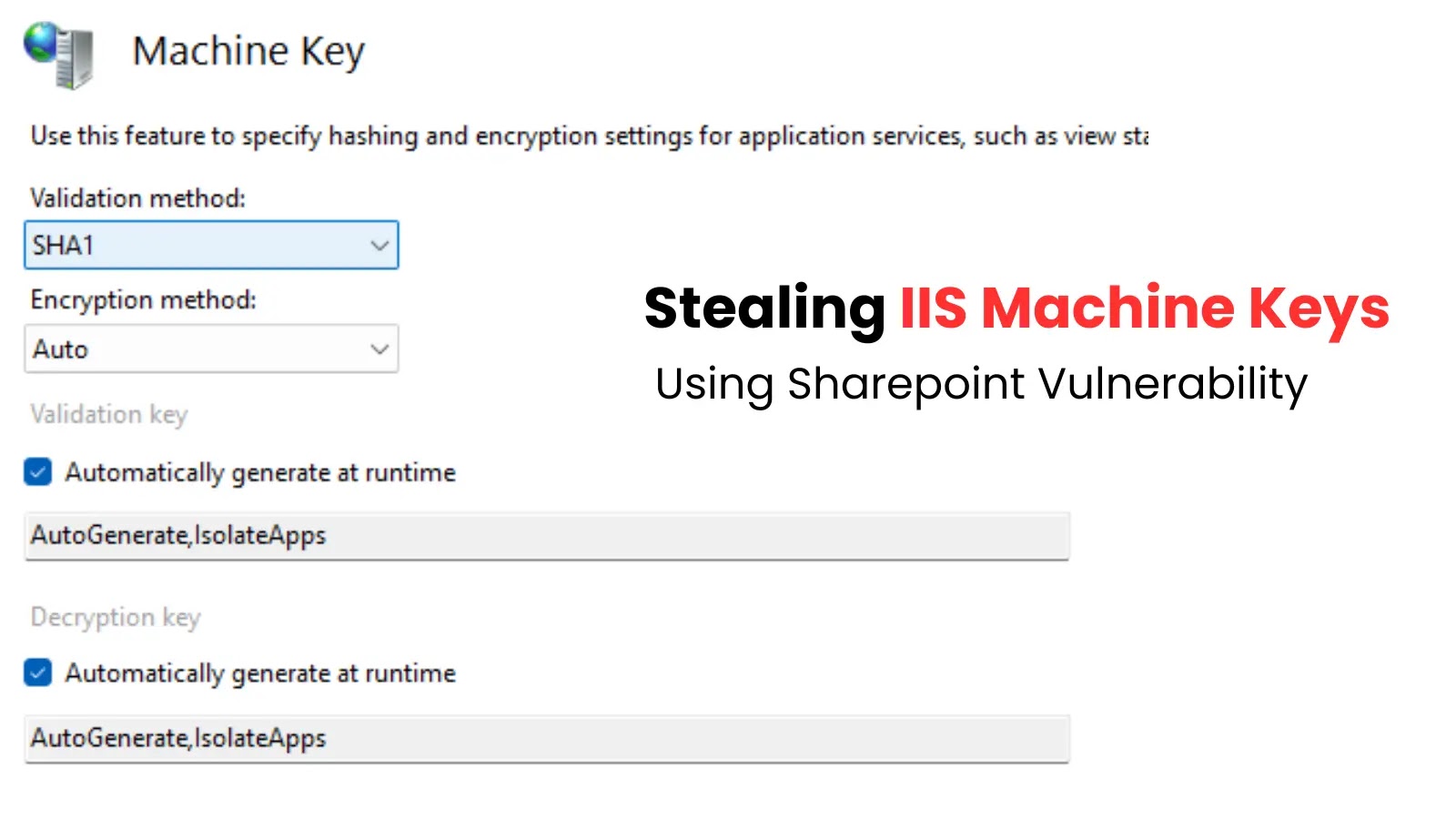
A sophisticated attack method where hackers are exploiting a deserialization vulnerability in SharePoint to steal Internet Information Services (IIS) Machine…