The North Korean-linked Chollima advanced persistent threat (APT) group, also known as Famous Chollima, has been orchestrating a persistent cyber…
Chaining NVIDIA’s Triton Server flaws exposes AI systems to remote takeover Pierluigi Paganini August 05, 2025 New flaws in NVIDIA’s…
French luxury fashion house Chanel has become the latest victim in a sophisticated cybercrime campaign targeting major corporations through their…
Aug 05, 2025Ravie LakshmananMalware / Mobile Security Cybersecurity researchers have lifted the veil on a widespread malicious campaign that’s targeting…
Google released its August 2025 Android Security Bulletin on August 4, revealing a critical vulnerability that poses significant risks to…
A critical security flaw in Streamlit, the popular open-source framework for building data applications, has been discovered that could allow…
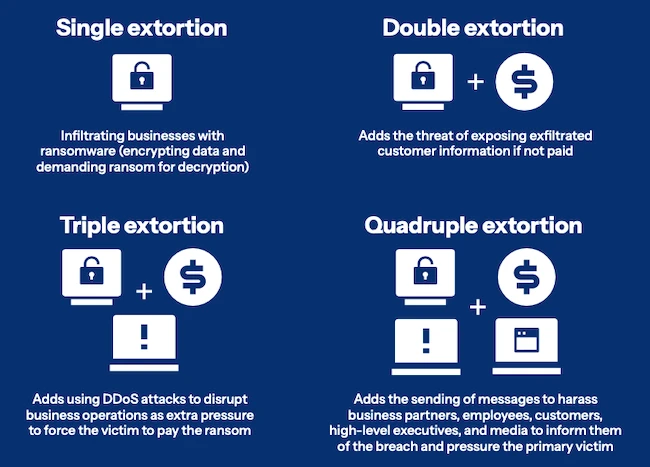
Threat actors are using a new quadruple extortion tactic in ransomware campaigns, while double extortion remains the most common approach,…
A sophisticated new Android malware campaign has emerged targeting Indian banking customers through convincing impersonations of popular financial applications. The…
A groundbreaking security research has revealed that parameter pollution techniques combined with JavaScript injection can bypass 70% of modern Web Application…
In this Help Net Security interview, Aayush Choudhury, CEO at Scrut Automation, discusses why many security tools built for large…
Aug 05, 2025Ravie LakshmananZero-Day / Network Security SonicWall said it’s actively investigating reports to determine if there is a new…
A critical vulnerability chain in NVIDIA’s Triton Inference Server that allows unauthenticated attackers to achieve complete remote code execution (RCE)…