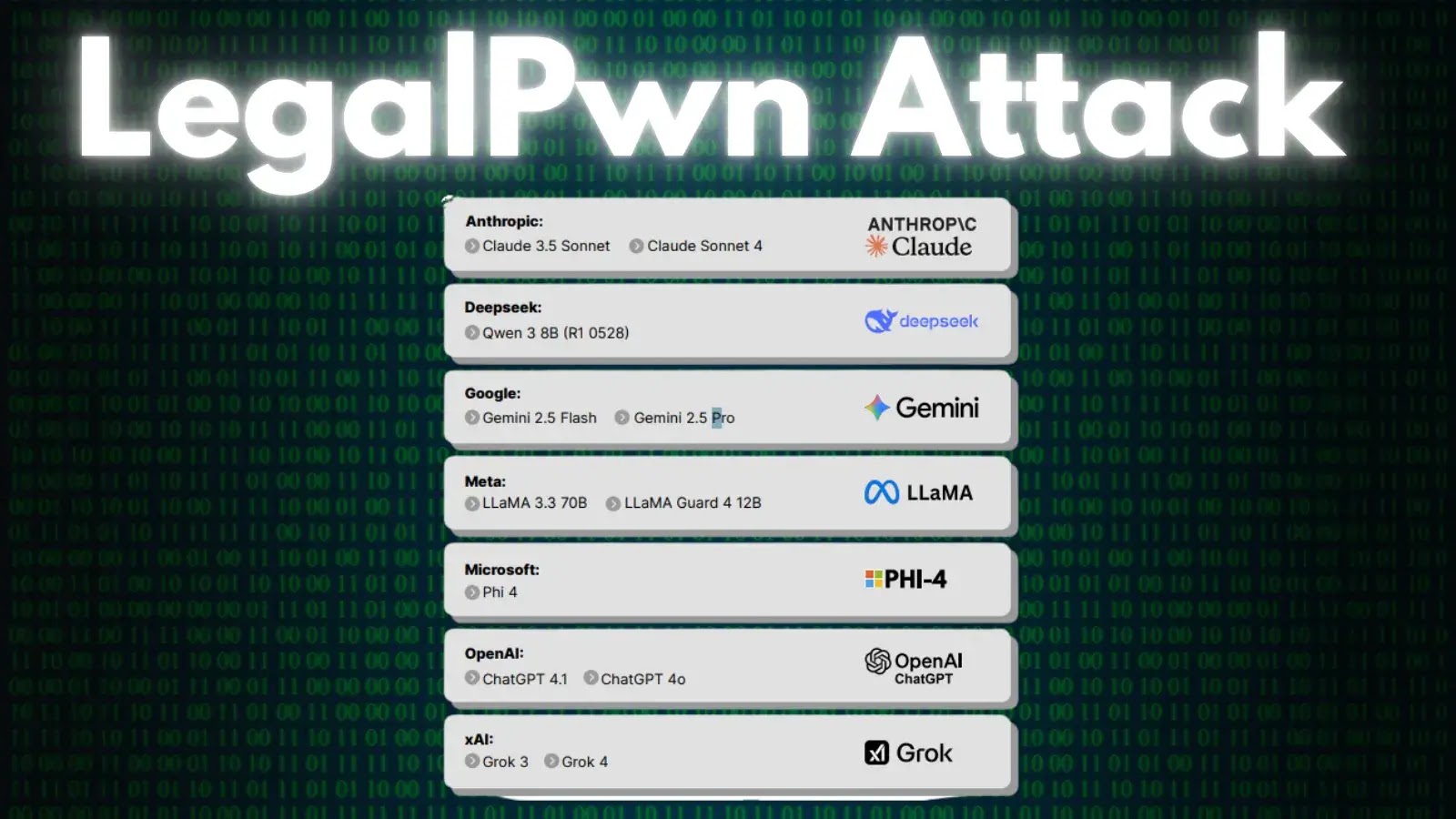
Security researchers have discovered a new type of cyberattack that exploits how AI tools process legal text, successfully tricking popular…
SpecterOps has released BloodHound 8.0, the latest iteration of its open-source attack path management platform, featuring major enhancements and expanded…
To protect digital privacy, the UAE Cybersecurity Council has issued a strict warning against the use of unofficial and unverified…
Is it deceptive, standards-violating content scraping or a security and internet infrastructure company on a crusade against artificial intelligence startups? …
The cybersecurity landscape faces a persistent threat as Raspberry Robin, a sophisticated malware downloader also known as Roshtyak, continues its…
Generative AI models, multi-cloud strategies, Internet of Things devices, third-party suppliers, and a growing list of regulatory compliance obligations all…
I think the future of Substack is self-hosting. Or—more directly—I don’t think they have much of a future. I’m sure…
Security researchers have discovered critical vulnerabilities in Anthropic’s Claude Code that allow attackers to bypass security restrictions and execute unauthorized…
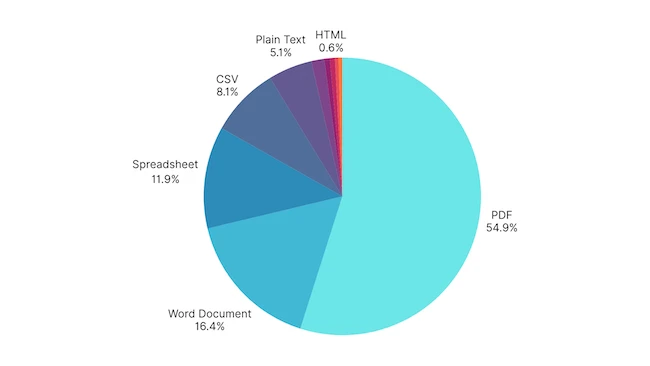
In Q2 2025, Harmonic reviewed 1 million GenAI prompts and 20,000 uploaded files across more than 300 GenAI and AI-powered…
CW – OT Security Officer SSE | United Kingdom | On-site – View job details As a CW – OT…
Sektor has announced a new distribution agreement with SentinelOne across Australia and New Zealand. The partnership will see Sektor offer…
The conversation around the UK’s Online Safety Act has transformed over the past week. Since it came into force last…