BlackSuit’s technical infrastructure was seized in a globally coordinated takedown operation last month that authorities touted as a significant blow…
The cybersecurity landscape has witnessed an unprecedented evolution as threat actors increasingly weaponize artificial intelligence to amplify their attack capabilities…
Introduction: The Battlefield Inside Your Head In cybersecurity, we master firewalls and encryption. But are we neglecting the most critical…
Cyber protection specialists Halcyon and Sophos have teamed up to develop a new threat intelligence sharing joint venture that will…
Hacking group D4rk4rmy claimed the hack of Monte-Carlo Société des Bains de Mer Pierluigi Paganini August 04, 2025 The cybercrime…
Microsoft announced that the transcription, dictation, and read aloud features will stop working in older versions of Office 365 applications…
A sophisticated new cybercriminal campaign has emerged, leveraging a Python-based information stealer known as PXA Stealer to orchestrate one of…
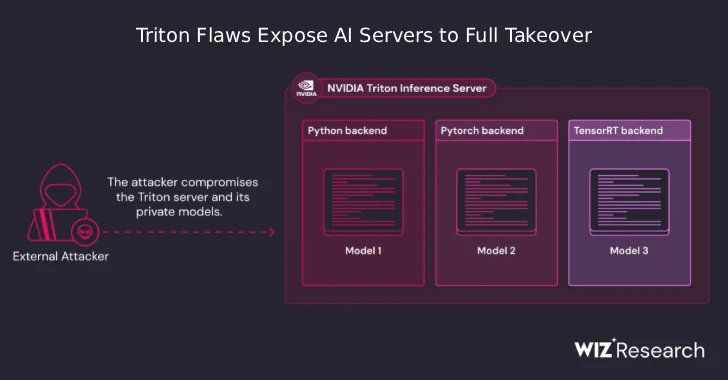
Aug 04, 2025Ravie LakshmananAI Security / Vulnerability A newly disclosed set of security flaws in NVIDIA’s Triton Inference Server for…
Cyber criminals and nation-states hostile to Western countries are weaponising artificial intelligence (AI) with gusto to carry out attacks and…
Northwest Radiologists data breach hits 350,000 in Washington Pierluigi Paganini August 04, 2025 A January 2025 breach at Northwest Radiologists…
Cybercriminals have escalated their attack sophistication by leveraging artificial intelligence to create a malicious NPM package that masquerades as a…
A new cybercrime campaign, dubbed JSCEAL, is actively targeting people who use cryptocurrency apps, reveals the latest research from security…