The cybersecurity landscape continues to evolve as threat actors develop increasingly sophisticated methods to compromise Windows systems. A new ransomware…
A severe security vulnerability in the widely-used Squid HTTP proxy has been disclosed, potentially exposing millions of systems to remote…
In this Help Net Security interview, Marc Frankel, CEO at Manifest Cyber, discusses how overlooked AI-specific risks, like poisoned training…
Netskope has released new research showing a 50% spike in genAI platform usage among enterprise end-users in the three months…
Cybersecurity researchers at Aim Labs have discovered a critical vulnerability in the popular AI-powered Cursor IDE that enables attackers to…
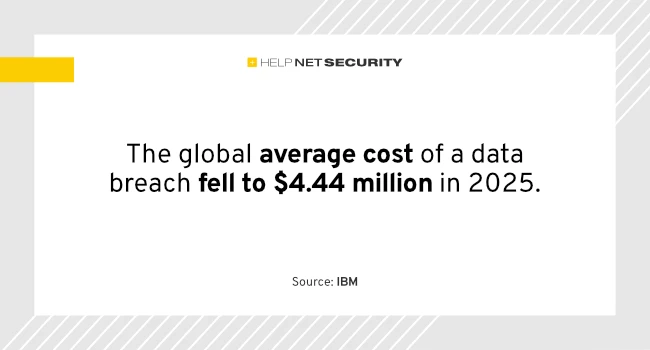
IBM released its Cost of a Data Breach Report, which revealed AI adoption is greatly outpacing AI security and governance….
Cloud success isn’t defined by what you can deploy, but by what you can operate, govern, and grow, with confidence,…
AU10TIX has launched a free Child Safety Age Assurance Risk and Readiness Assessment and Age Assurance Readiness Guide designed to…
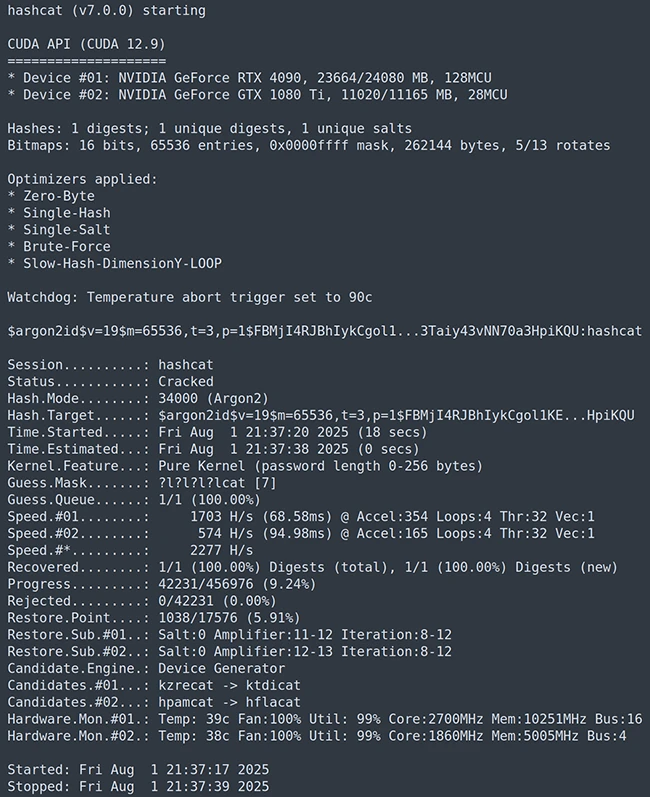
Hashcat is an open-source password recovery tool that supports five attack modes and more than 300 highly optimized hashing algorithms….
Enterprise risk leaders are most concerned about rising tariffs and trade tensions heading into the second half of 2025, according…
Meta Platforms is pressing ahead with efforts to bring in outside partners to help fund the massive infrastructure needed to…
The Northern Territory Police Force has adopted a top-down change management strategy to oversee the delivery of technology and transformation…