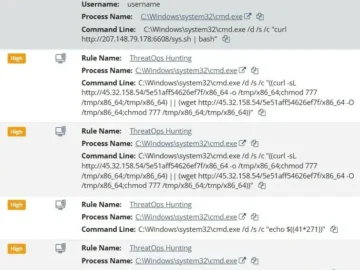
Summary On February 6, 2026, Microsoft reported the exploitation of SolarWinds Web Help Desk (WHD) servers The exploitation facilitated multi-stage…
Pakistan-based threat actor APT36, widely known as Transparent Tribe, has shifted away from carefully crafted tools to a new approach…
In this post we’ll show you how Java handles unicode escapes in source code strings in a way you might…
ClipXDaemon is a new Linux malware family that hijacks cryptocurrency clipboard data in X11 sessions, operating fully offline without any…
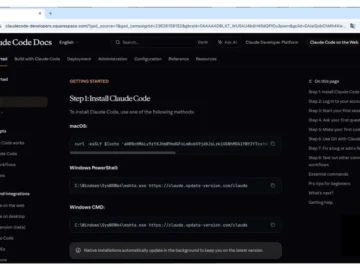
Users looking for Anthropic’s Claude Code agentic AI coding tool are being tricked via fake Claude Code install pages into…
Two Google Chrome extensions have turned malicious after what appears to be a case of ownership transfer, offering attackers a…
Artificial intelligence (AI) is a rapidly growing technology, becoming more embedded in society and business every day, but is the…
Congrats—you got the green light to move forward with improving identity access management (IAM). While you realize this is great…
Flights canceled. Emergency rooms shut down. Centuries-old companies shuttered. Ransomware and other similar cyberattacks have become so routine that even…
The European Commission has prepared a Communication providing practical guidance on applying the Cyber Resilience Act (CRA). It will help…
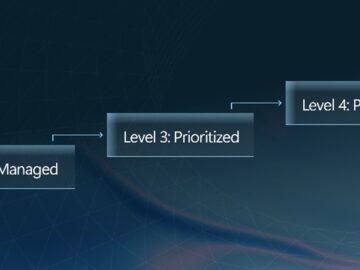
Effective exposure management begins by illuminating and hardening risks across the entire attack surface. Some of the most meaningful shifts…
Every security professional knows the drill. You go home for the holidays and, without volunteering, you become the family’s help…