The Senate voted to confirm Sean Cairncross as national cyber director Saturday, giving the Trump administration one of its top…
A Pi-hole donor has reported receiving spam email to an address created exclusively for their donation to the popular network-level…
Welcome to this week’s edition of Cybersecurity News Recap! In this issue, we bring you the latest updates and critical developments…
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malware…
Akira Ransomware targets SonicWall VPNs in likely zero-day attacks Pierluigi Paganini August 03, 2025 Akira ransomware targets fully patched SonicWall…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. The U.S….
A new round of the weekly Security Affairs newsletter has arrived! Every week, the best security articles from Security Affairs…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Review: LLM Engineer’s HandbookFor all…
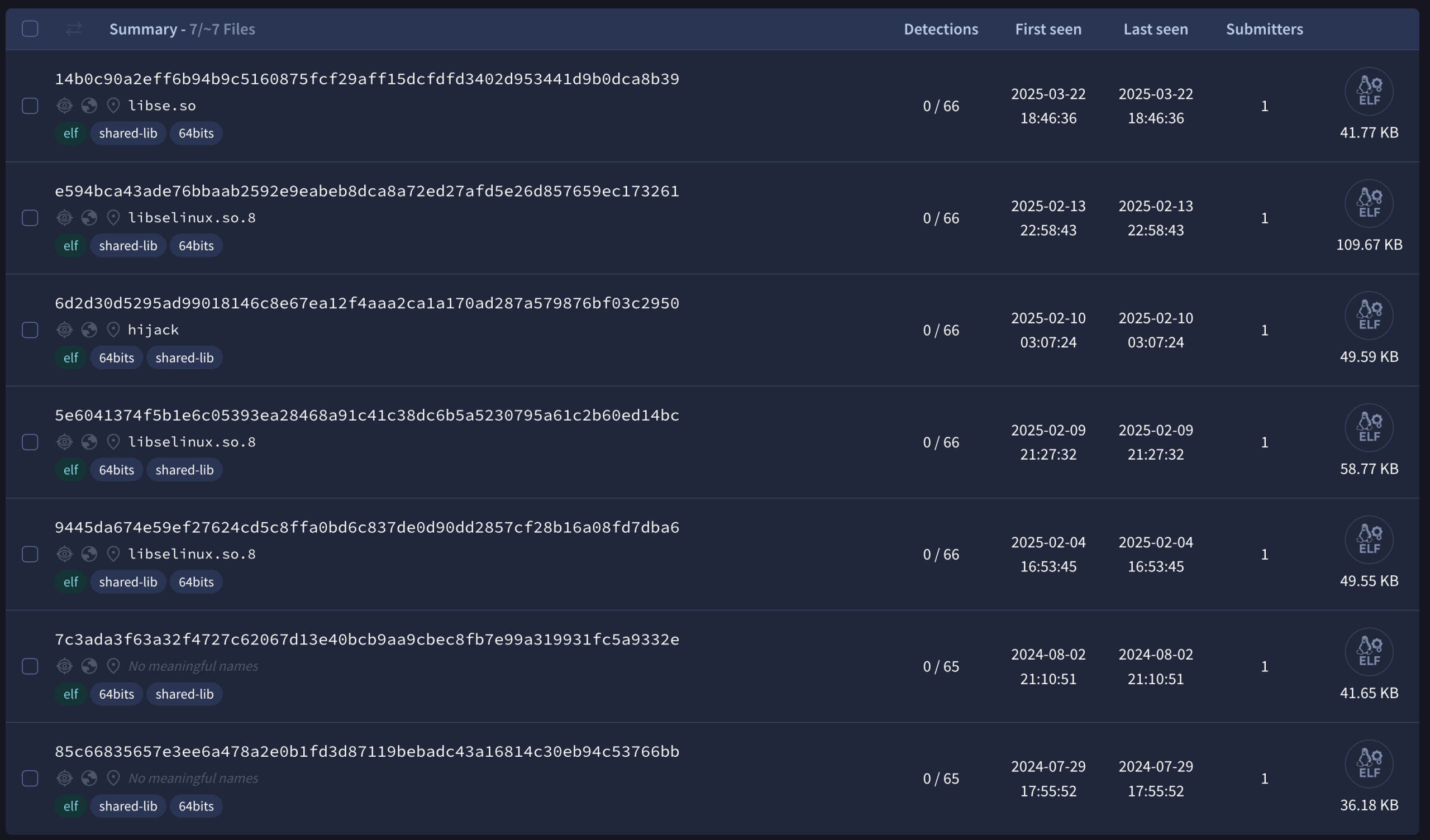
New Linux backdoor Plague bypasses auth via malicious PAM module Pierluigi Paganini August 02, 2025 A stealthy Linux backdoor named…
China Presses Nvidia Over Alleged Backdoors in H20 Chips Amid Tech Tensions Pierluigi Paganini August 02, 2025 China questioned Nvidia…
A new and deceptive multi-stage malware campaign has been identified by the Lat61 Threat Intelligence team at security firm Point…
Telecommunications organizations in Southeast Asia have been targeted by a state-sponsored threat actor known as CL-STA-0969 to facilitate remote control…