ToolShell under siege: Check Point analyzes Chinese APT Storm-2603 Pierluigi Paganini August 01, 2025 Storm-2603 group exploits SharePoint flaws and…
Here’s a look at cybersecurity stories that moved the needle, raised the alarm, or offered vital lessons in July 2025…
Microsoft has significantly enhanced its .NET bounty program, announcing substantial updates that expand the program’s scope, streamline award structures, and…
Outflank is pioneering the integration of large language models (LLMs) to expedite research and development workflows while maintaining rigorous quality…
Amazon Web Services (AWS) reported a 17.5% year-on-year increase in revenue to $30.9bn during the second quarter of its 2025…
The Zero Day Initiative is offering a $1 million reward to security researchers who will demonstrate a zero-click WhatsApp exploit…
Trend Micro’s Zero Day Initiative (ZDI) announces an unprecedented $1,000,000 bounty for a zero-click remote code execution (RCE) exploit targeting…
Cybercriminals are increasingly exploiting link wrapping features from vendors like Proofpoint and Intermedia to mask malicious payloads, leveraging the inherent…
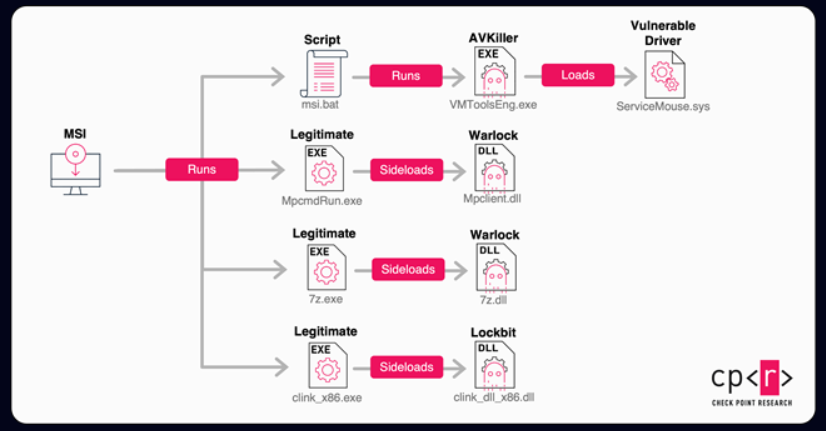
Aug 01, 2025Ravie LakshmananThreat Intelligence / Ransomware The threat actor linked to the exploitation of the recently disclosed security flaws…
CISA released two high-severity Industrial Control Systems (ICS) advisories on July 31, 2025, highlighting critical vulnerabilities in widely deployed industrial…
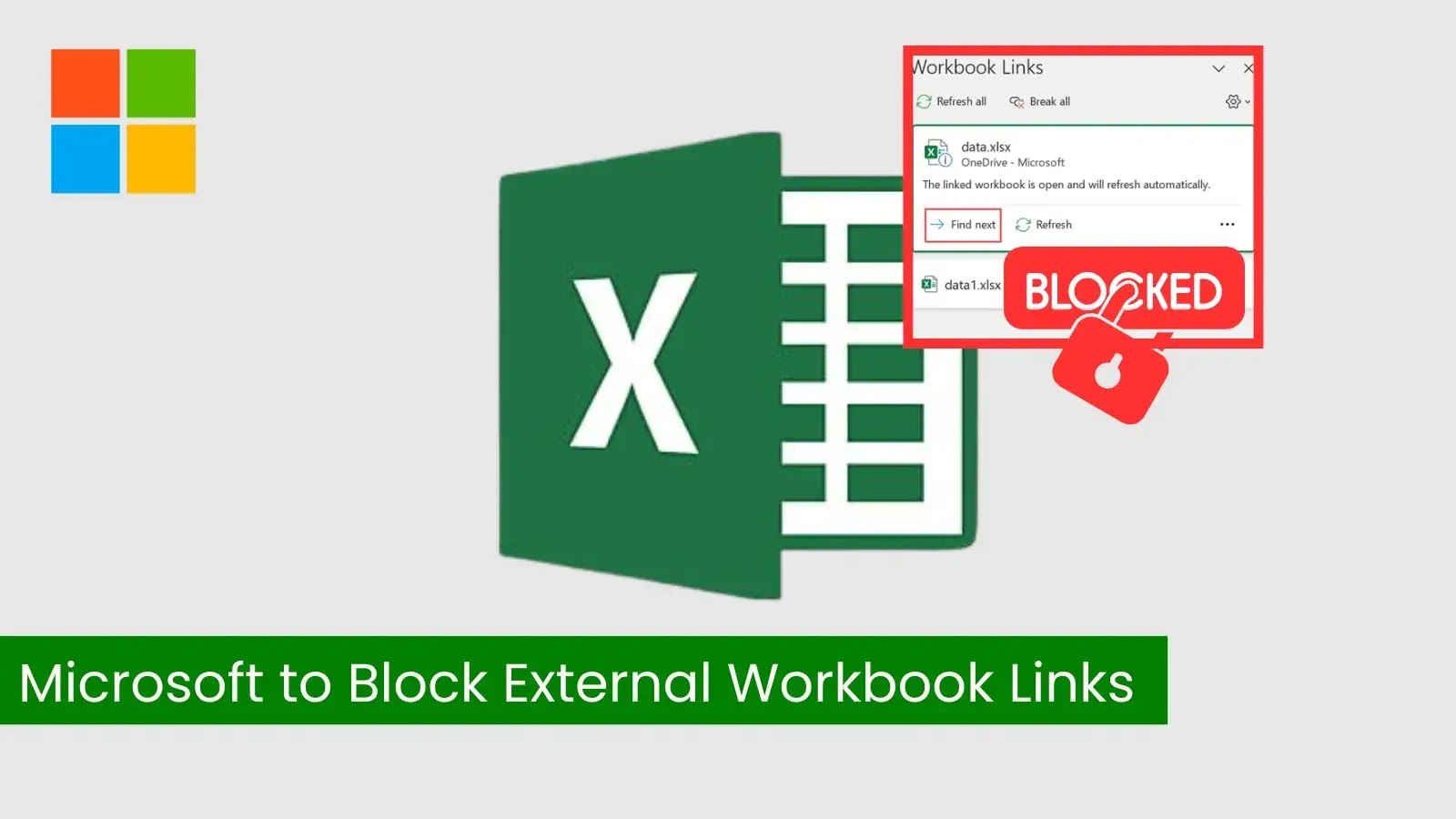
Microsoft announced a significant security enhancement for Excel users, revealing plans to block external workbook links to unsafe file types…
The latest wave of credential-phishing campaigns has revealed an unexpectedly convenient ally for threat actors: the very e-mail security suites…