Jul 30, 2025Ravie LakshmananCryptocurrency / Browser Security Cybersecurity researchers are calling attention to an ongoing campaign that distributes fake cryptocurrency…
Financial results analysis by Forrester has found that enterprise software providers are ramping up efforts to sell the idea of…
Threat actors are actively exploiting a critical unauthenticated arbitrary file upload vulnerability in the WordPress theme ‘Alone,’ to achieve remote…
A sophisticated North Korean cyber espionage operation known as TraderTraitor has emerged as one of the most formidable threats to…
Large language model (LLM)-powered honeypots are becoming increasingly complex instruments for luring and examining threat actors in the rapidly changing…
Apple released a security update for iOS and iPadOS to patch multiple vulnerabilities, including one that could leak sensitive information…
The National Air Traffic Services (NATS) organisation responsible for air traffic control services at multiple airports in the UK is…
The UNC2891 hacking group, also known as LightBasin, used a 4G-equipped Raspberry Pi hidden in a bank’s network to bypass…
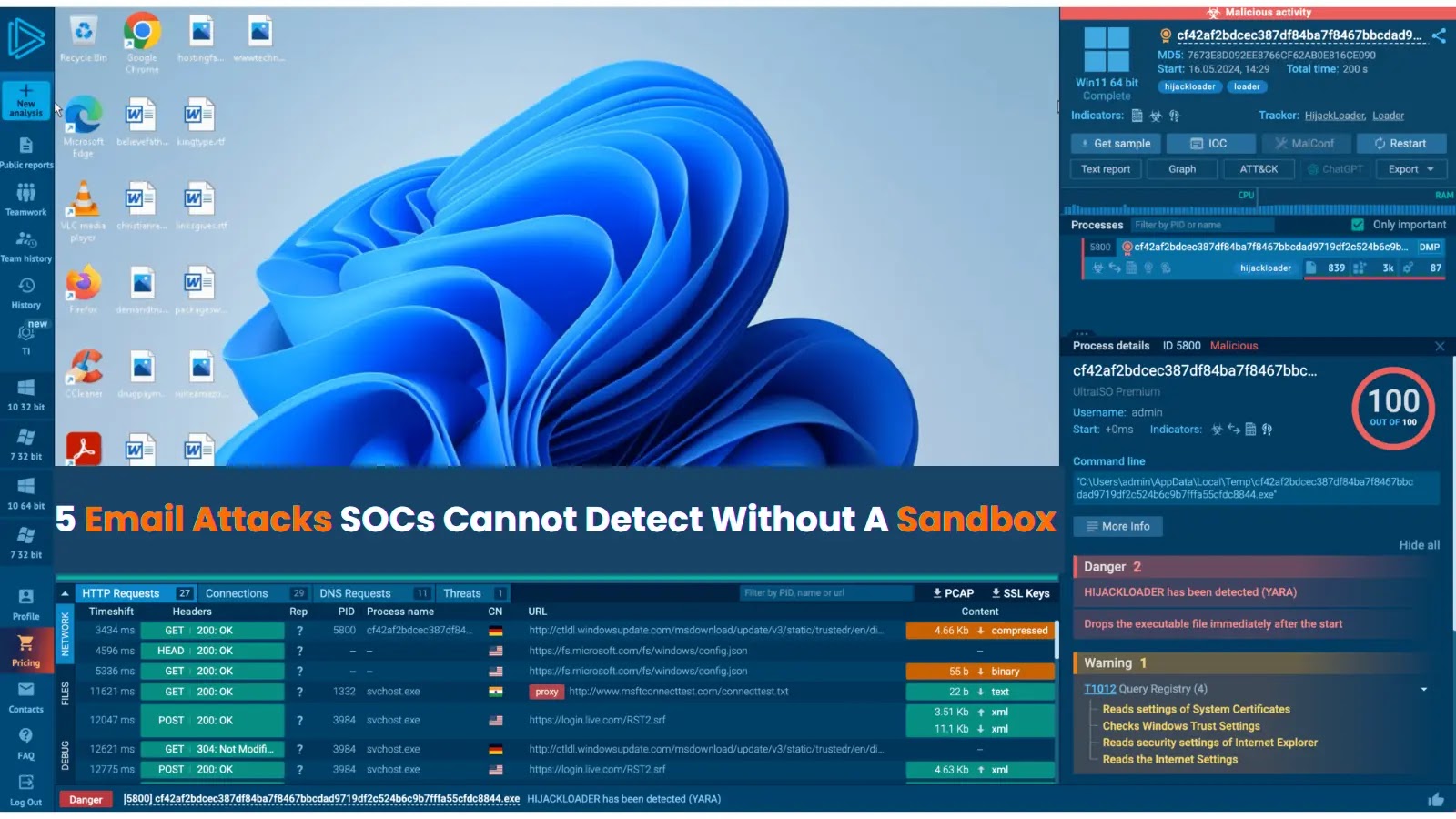
Even with Slack, Teams, and every new communication tool out there, email remains the top attack vector for businesses. Why?…
A sophisticated cyberattack campaign disrupted the Russian IT industry and entities in several other countries, leveraging advanced evasion techniques to…
Jul 30, 2025Ravie LakshmananEncryption / Ransomware Cybersecurity experts have released a decryptor for a ransomware strain called FunkSec, allowing victims…
The Scattered Spider hacking collective is still hard at work refining its tactics and deploying new malware variants in the…