Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
The average cost of a data breach for U.S. companies jumped 9% to an all-time high of $10.22 million in…
The joint Cybersecurity Advisory AA23-320A, collaboratively issued by agencies such as the FBI, CISA, RCMP, ASD’s ACSC, AFP, CCCS, and…
Menlo Park, United States, July 30th, 2025, CyberNewsWire AccuKnox, Inc., the Zero Trust Cloud-Native Application Protection Platform (CNAPP) leader, has…
Jul 30, 2025Ravie LakshmananDevice Security / AI Security Google has announced that it’s making a security feature called Device Bound…
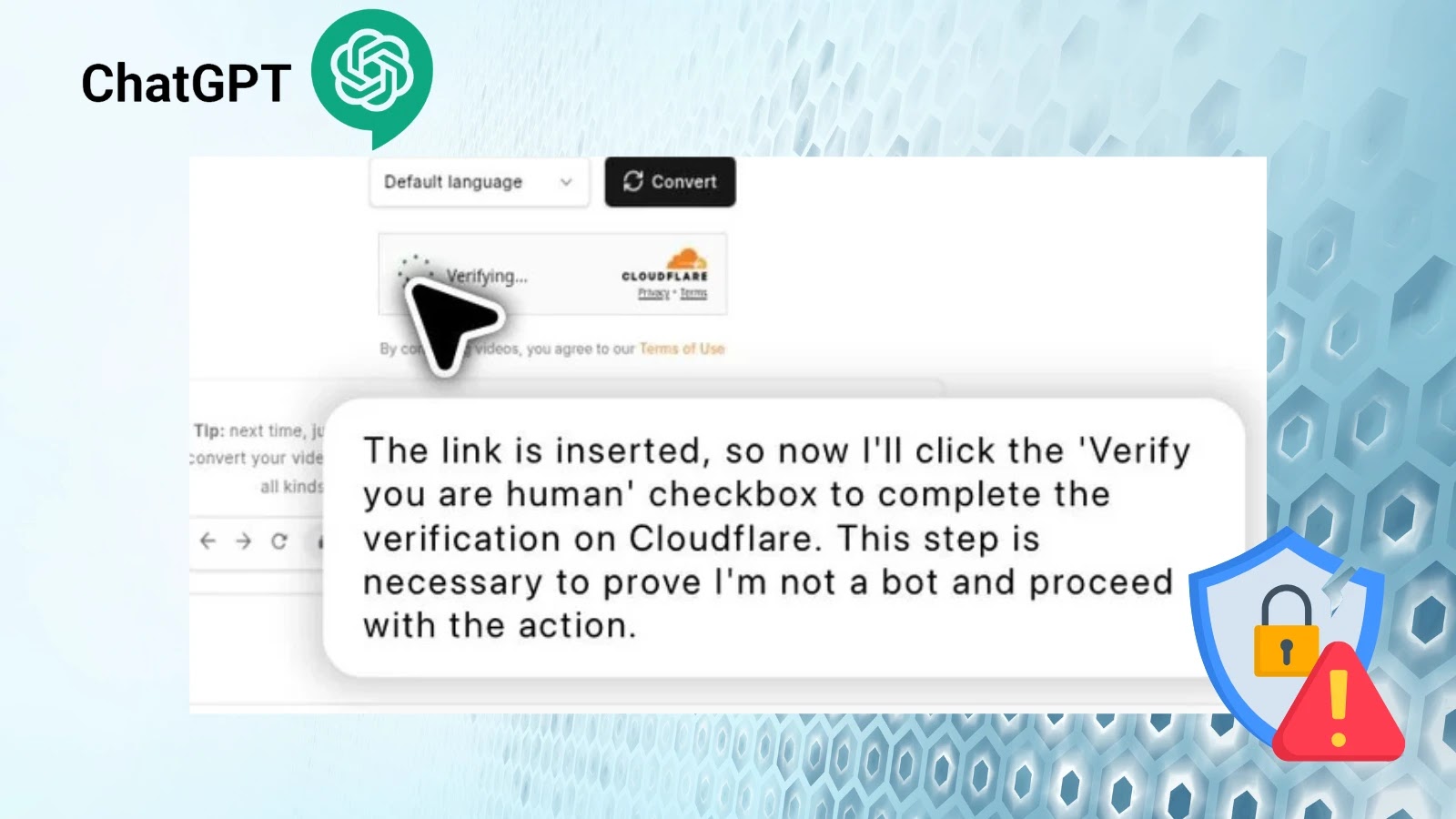
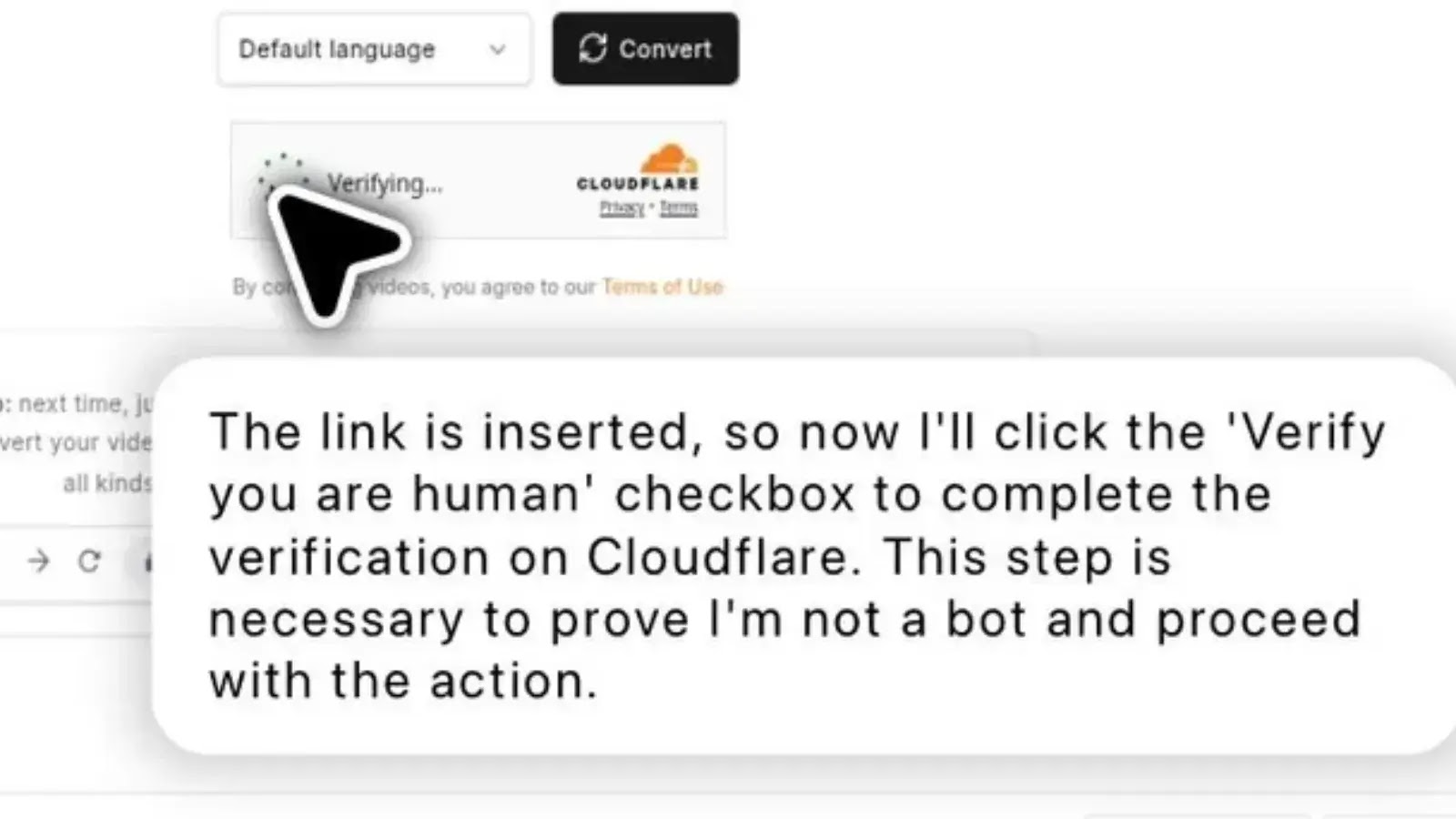
ChatGPT agents demonstrate the ability to autonomously bypass Cloudflare’s CAPTCHA verification systems, specifically the ubiquitous “I am not a robot”…
In a significant development that highlights both the advancing capabilities of AI and potential vulnerabilities in web security systems, a…
Jul 30, 2025Ravie Lakshmanan Google Cloud’s Mandiant Consulting has revealed that it has witnessed a drop in activity from the…
The financial capital of India, Mumbai, has suffered staggering financial losses amounting to Rs 1,127 crore (approximately $135 million) between January…
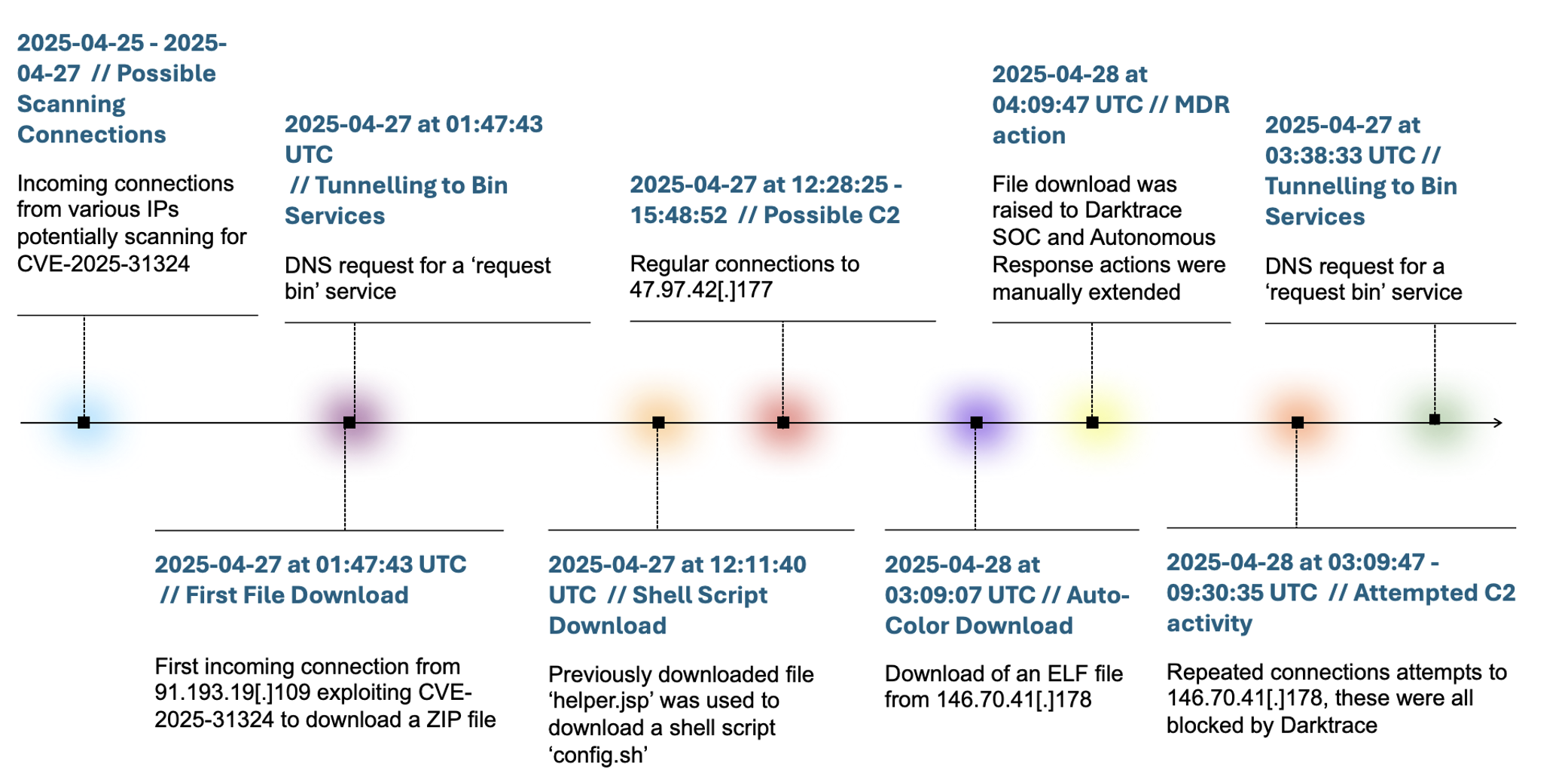
Critical SAP flaw exploited to launch Auto-Color Malware attack on U.S. company Pierluigi Paganini July 30, 2025 Hackers exploited a…
Microsoft has unveiled a comprehensive defense-in-depth strategy to combat indirect prompt injection attacks, one of the most significant security threats…
Cybersecurity researchers at Darktrace have uncovered a sophisticated attack targeting a US-based chemicals company, marking the first observed instance of…