Jul 30, 2025Ravie LakshmananVulnerability / Threat Intelligence Threat actors have been observed exploiting a now-patched critical SAP NetWeaver flaw to…
The UK’s AI Security Institute is collaborating with several global institutions on a global initiative to ensure artificial intelligence (AI)…
A sophisticated cyberattack targeting a US-based chemicals company has revealed the first observed pairing of SAP NetWeaver exploitation with Auto-Color…
Researchers at Avast have unveiled a free decryptor tool for victims of the FunkSec ransomware, marking a significant step in…
The loosely connected network of threat actors behind several high profile hacks known as Scattered Spider has added new ransomware…
Enterprise applications integrating Large Language Models (LLMs) face unprecedented security vulnerabilities that can be exploited through deceptively simple prompt injection…
Microsoft has unveiled new guidance addressing one of the most pressing security challenges facing enterprise AI deployments: indirect prompt injection…
Identity-based attack paths are behind most breaches today, yet many organizations can’t actually see how those paths form. The 2025…
A major security flaw has been detected in the popular PHP framework CodeIgniter4. The tag of a critical vulnerability, CVE-2025-54418,…
Optus will begin using a generative AI-powered virtual agent, co-developed with Google Cloud, to interpret and support contact centre staff…
Security researchers have discovered alarming vulnerabilities in enterprise Large Language Model (LLM) applications that could allow attackers to bypass authentication…
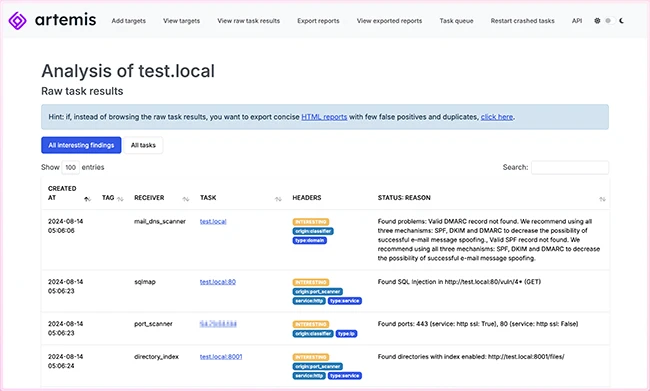
Artemis is an open-source modular vulnerability scanner that checks different aspects of a website’s security and translates the results into…