The state of Minnesota has activated the National Guard to assist the city of St. Paul after a massive cyberattack…
French telecommunications giant Orange confirmed it suffered a significant cyberattack on Friday, July 25th, targeting one of its critical information…
It’s unsettling to think that our food supply chain could be targeted or that the safety of our food could…
Not all browser add-ons are handy helpers – some may contain far more than you have bargained for 29 Jul…
Australia has retained its position as the fourth most targeted country in the world for cyberattacks on operational technology (OT)…
Google has released an emergency security update for its Chrome browser to address critical vulnerabilities that could allow attackers to…
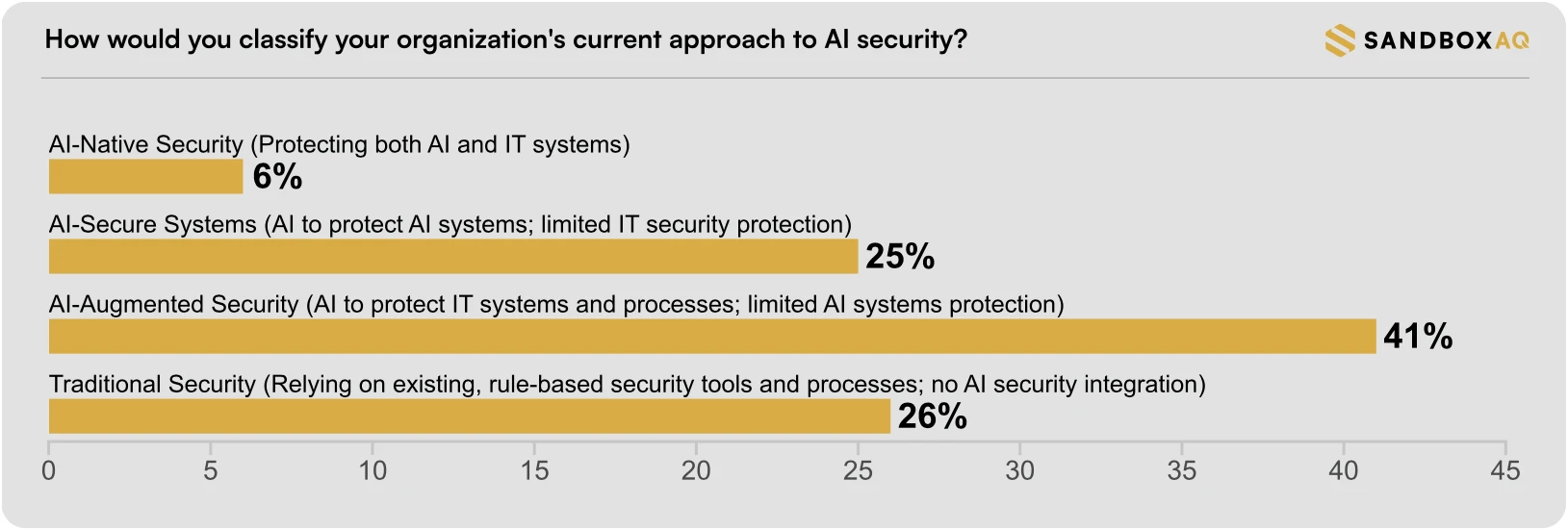
Although 79% of organizations are already running AI in production, only 6% have put in place a comprehensive security strategy…
Cybercriminals have launched a sophisticated multi-vector attack campaign targeting fans and teams ahead of the 2025 Belgian Grand Prix, scheduled…
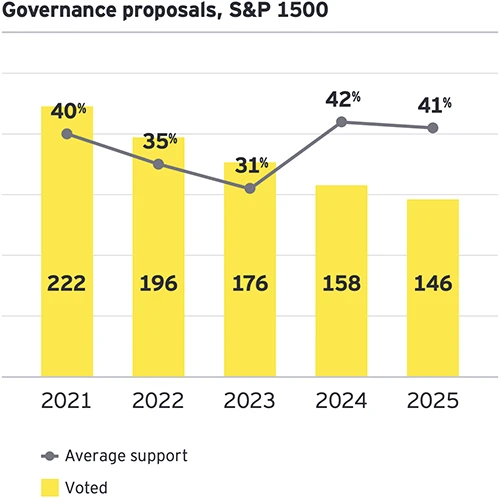
Corporate boards are adjusting to a more uncertain proxy landscape, according to EY’s 2025 Proxy Season Review. The report highlights…
A financially motivated threat actor known as Lionishackers has emerged as a significant player in the illicit marketplace for corporate…
Google has issued an urgent security update for its Chrome browser, patching several vulnerabilities, including a high-severity vulnerability that could…
Australia will include YouTube in its world-first ban on social media for teenagers, reversing an earlier decision to exempt the…