The FBI and CISA issued updated guidance today on the Scattered Spider threat group, including information on recent attack techniques…
Sean Plankey’s path to leading the Cybersecurity and Infrastructure Security Agency might have one obstacle set to be cleared for…
Aeroflot, Russia’s flag carrier, has suffered a cyberattack that resulted in the cancellation of more than 60 flights and severe…
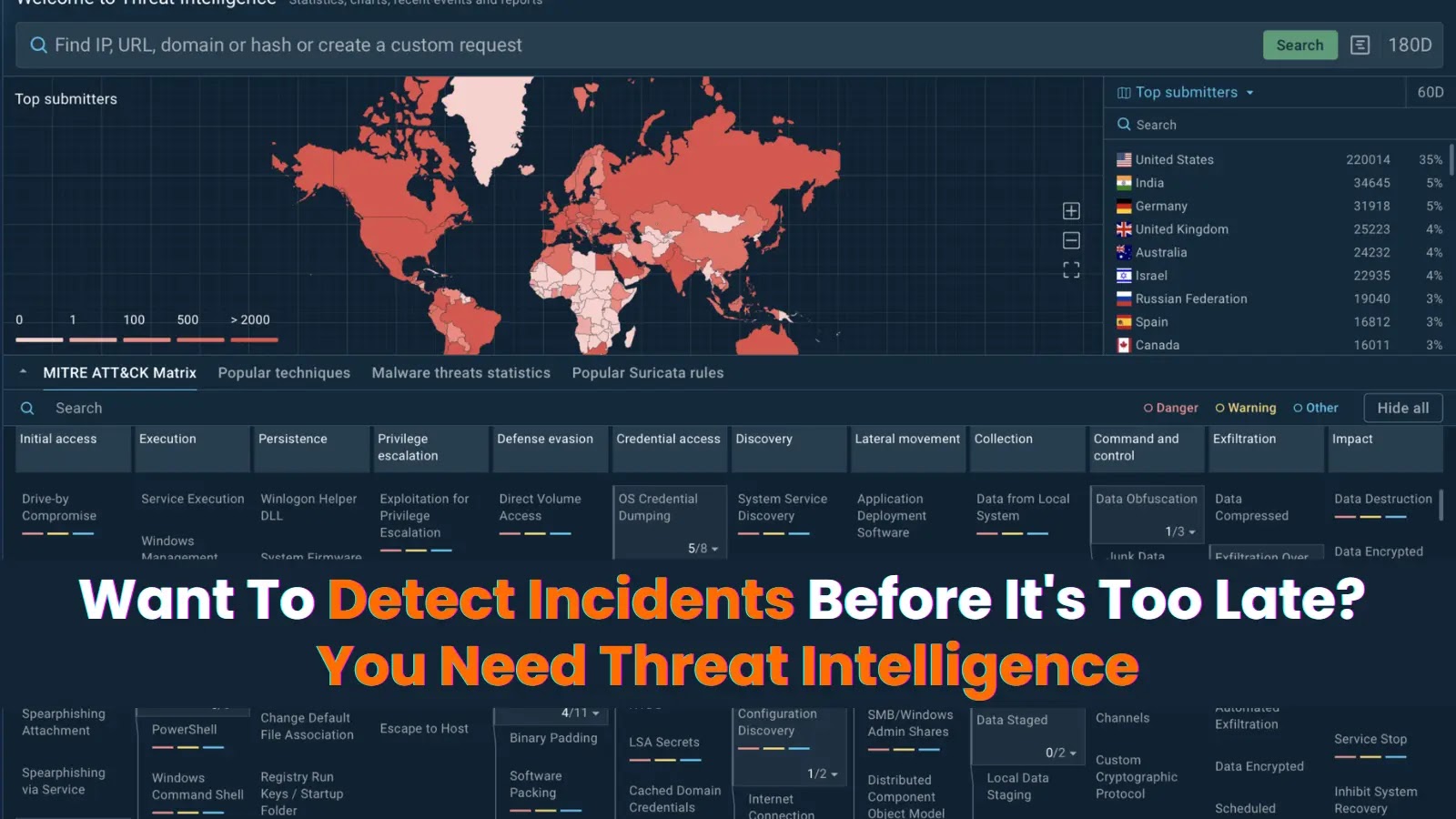
The difference between a minor security incident and a devastating breach often comes down to one critical factor: how quickly…
Cyble Research and Intelligence Labs (CRIL) has uncovered a sophisticated Android banking trojan dubbed RedHook, which disguises itself as legitimate…
The European Commission (EC) has been ignoring calls to reassess Israel’s data adequacy status for over a year, despite “urgent…
Hackers leak images and comments from women dating safety app Tea Pierluigi Paganini July 29, 2025 The dating safety app…
Most of your targets often resort to using content delivery networks (CDNs) or other anti-DDoS reverse proxies to mask their…
As awareness grows around many MFA methods being “phishable” (i.e. not phishing resistant), passwordless, FIDO2-based authentication methods (aka. passkeys) like…
The Python Package Index (PyPI) has issued an urgent warning to developers about an ongoing phishing campaign that exploits domain…
The Qilin ransomware gang has introduced a “Call Lawyer” feature for its affiliates, announced on a Russian-speaking darknet forum. This…
If you thought using a public phone charger was safe, it’s time to think again. Despite years of updates aimed…