Insurance company Allianz Life was breached, exposing the data of most of its 1.4 million American customers. According to Allianz,…
Jul 29, 2025Ravie LakshmananPhishing / Developer Security The maintainers of the Python Package Index (PyPI) repository have issued a warning…
The Austrian government is likely to face legal challenges after it succeeded on its fifth attempt to pass a law…
French telecom giant Orange issued red alert as it responds to a cyberattack targeting its “information systems.” Certain services and…
Microsoft has introduced Copilot Mode, an experimental feature designed to transform Microsoft Edge into a web browser powered by artificial…
Multiple critical vulnerabilities affecting SonicWall’s SMA100 series SSL-VPN appliances, highlighting persistent security flaws in network infrastructure devices. The vulnerabilities, designated…
In the ever-evolving infostealer landscape, 0bj3ctivityStealer emerges as a formidable threat, blending advanced obfuscation with targeted data exfiltration. Discovered earlier…
Jul 29, 2025Ravie LakshmananLLM Security / Vulnerability Cybersecurity researchers have disclosed a now-patched critical security flaw in a popular vibe…
The FBI and the Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday released an updated advisory about the cybercrime collective Scattered…
Hackers were spotted exploiting a critical SAP NetWeaver vulnerability tracked as CVE-2025-31324 to deploy the Auto-Color Linux malware in a…
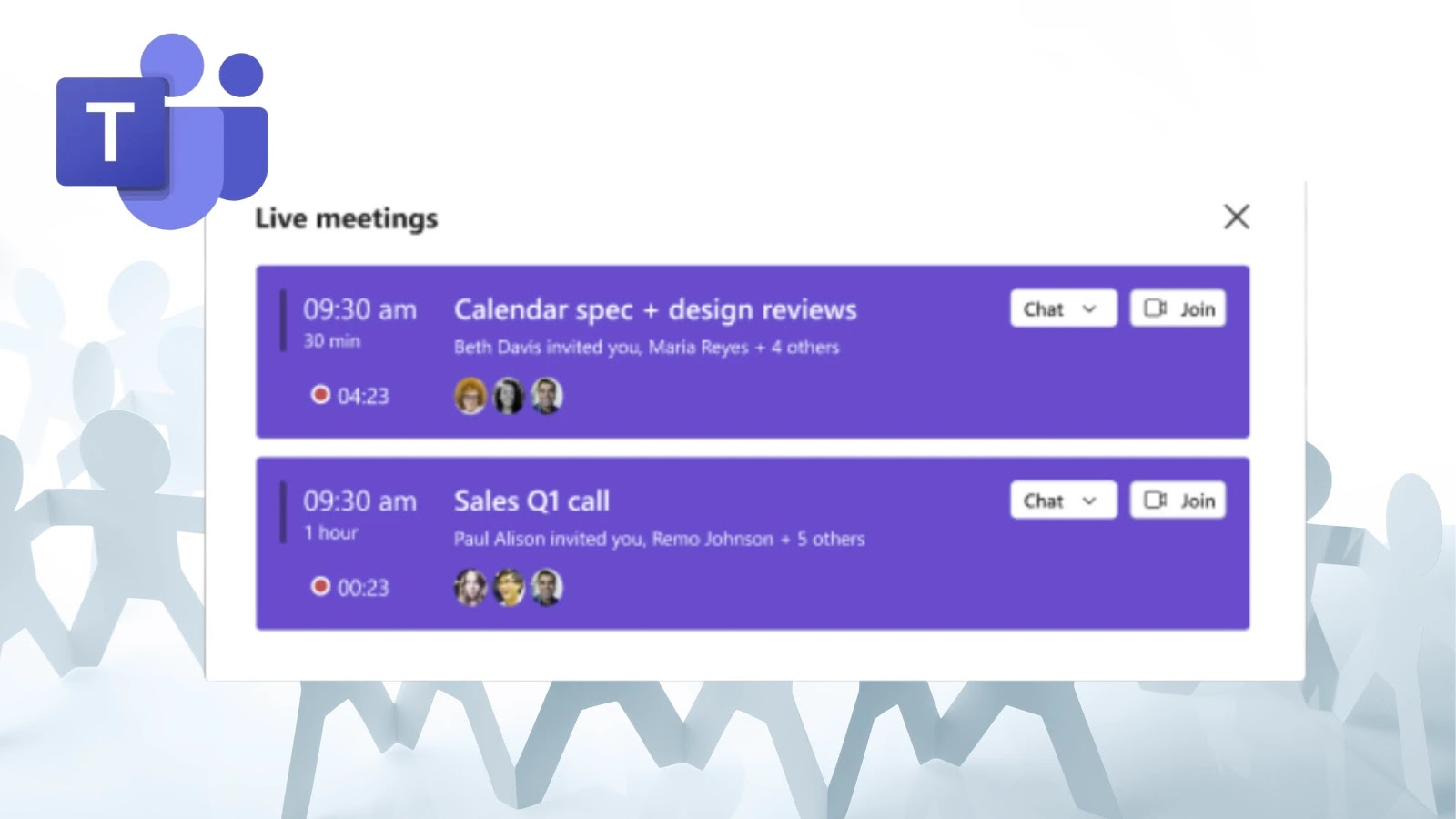
Microsoft Teams is rolling out a significant enhancement to its meeting experience with the introduction of a new meeting join…
The ToxicPanda Android banking trojan has emerged as a significant threat, compromising over 4,500 devices primarily in Portugal and Spain…