Until recently, the cyber attacker methodology behind the biggest breaches of the last decade or so has been pretty consistent:…
The Linux Foundation has officially released Linux kernel 6.16 on July 27, 2025, marking another milestone in open-source operating system…
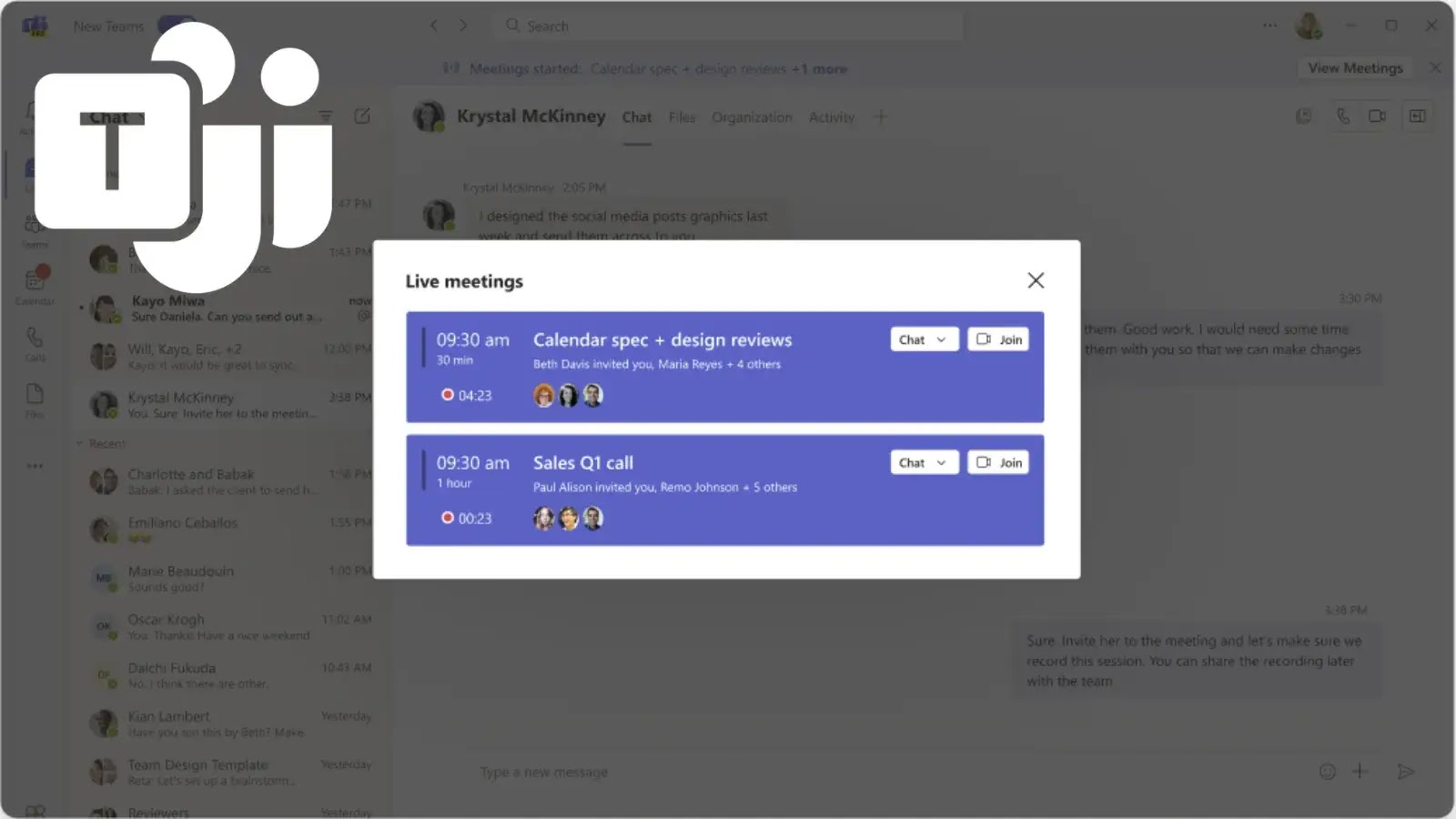
Microsoft Teams is rolling out a new meeting join banner designed to streamline the meeting experience for users who have…
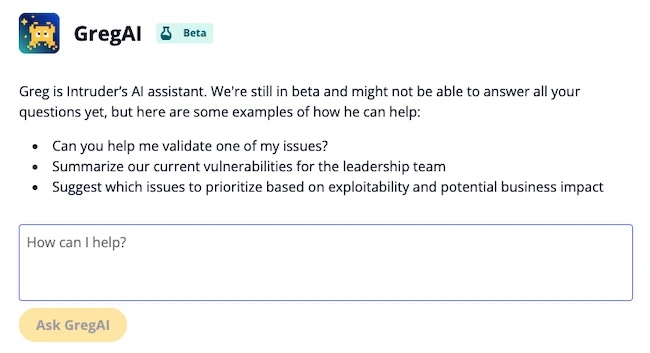
Intruder has launched GregAI, an AI-powered security analyst that offers comprehensive visibility into users’ security infrastructure, now available in beta….
Until recently, the cyber attacker methodology behind the biggest breaches of the last decade or so has been pretty consistent:…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical alert, adding three high-impact vulnerabilities to its Known…
Apple quietly slipped a game-changing developer feature into its WWDC 25 announcements: a native containerization stack that lets Macs run…
Python developers are being warned about a sophisticated phishing campaign targeting users of the Python Package Index (PyPI) through fraudulent…
Cleaning products giant Clorox has sued its IT services partner, Cognizant, alleging that a devastating August 2023 ransomware attack that…
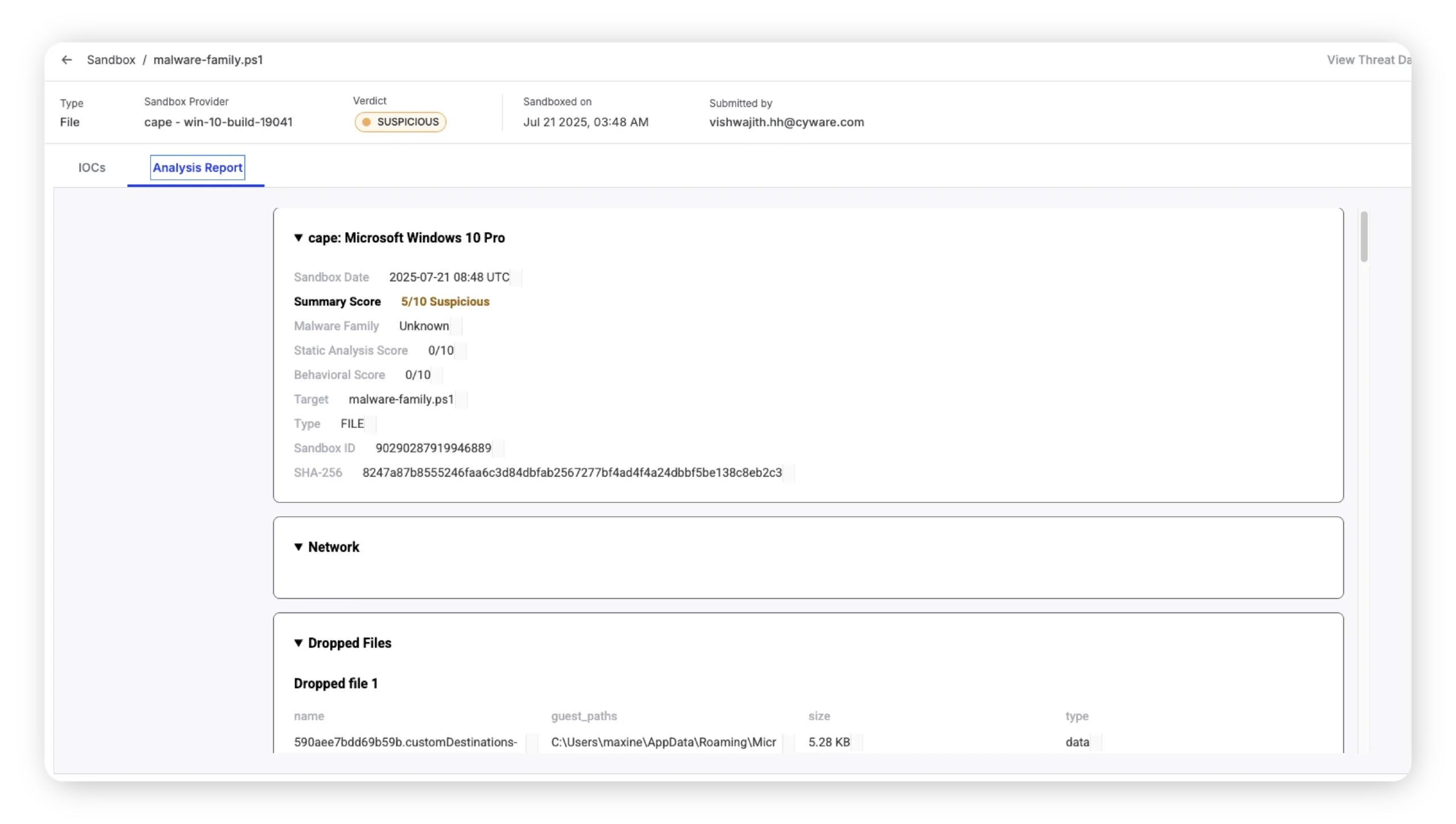
Cyware expanded its Cyware Intelligence Suite, an enhanced threat intelligence program-in-a-box that consolidates threat management capabilities into a streamlined, logical…
Romania’s National Cyber Security Directorate (DNSC) has sounded the alarm on an active phishing campaign exploiting the identity of the…
Pro-Ukraine hacktivists claim cyberattack on Russian Airline Aeroflot that caused the cancellation of +100 flights Pierluigi Paganini July 29, 2025…