Researchers have released a report detailing how a recent WinRAR path traversal vulnerability tracked as CVE-2025-8088 was exploited in zero-day…
Threat actors have begun a geographically focused campaign against Israeli infrastructure and corporate entities in a sophisticated cyber incursion discovered…
The Federal Communications Commission has adopted new rules to make it more difficult for foreign firms to apply for licensing…
Researchers have released a report detailing how a recent WinRAR path traversal vulnerability tracked as CVE-2025-8088 was exploited in zero-day…
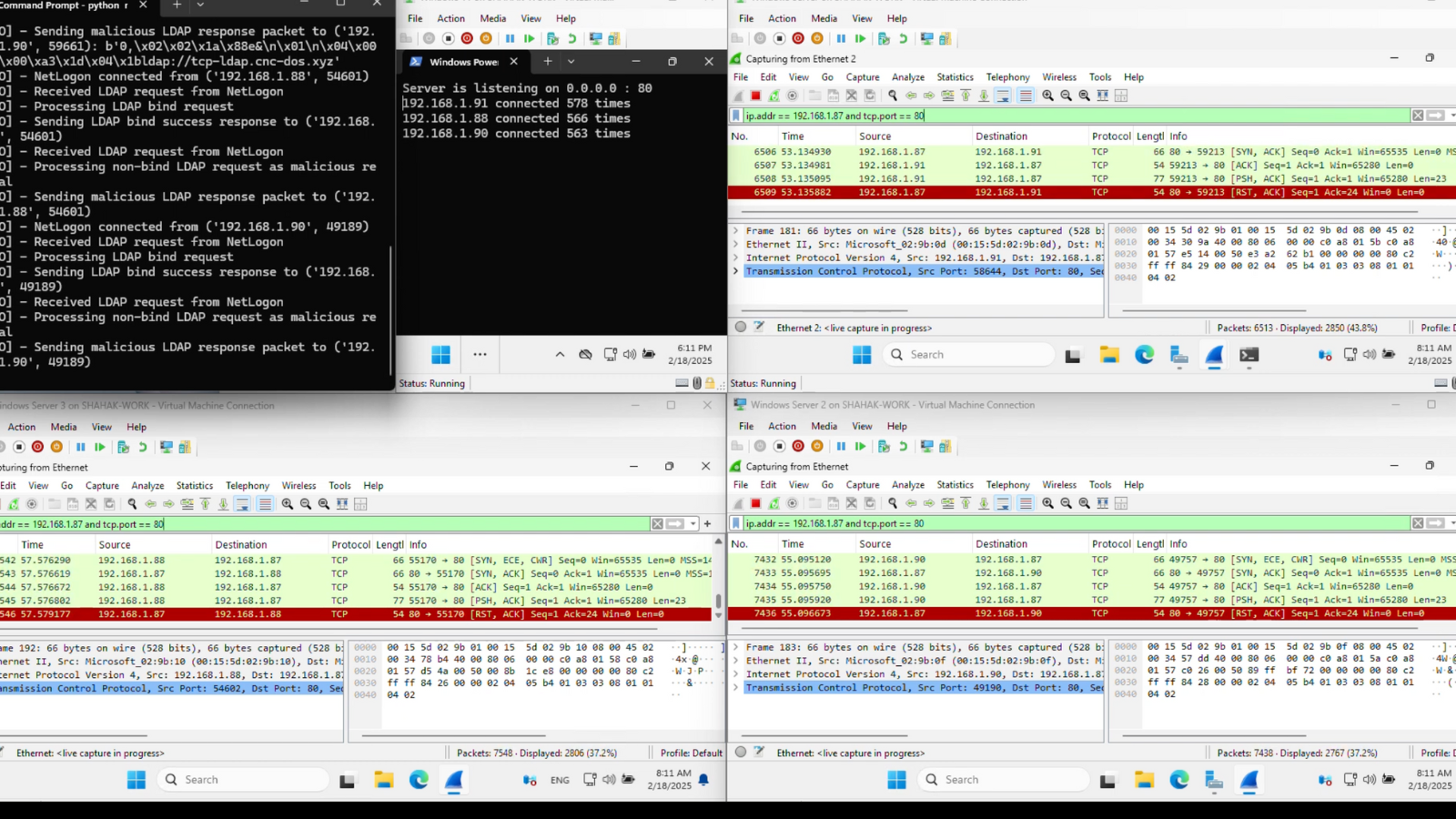
Security researchers have uncovered a “zero-click” denial-of-service chain that can silently turn thousands of Microsoft Windows Domain Controllers (DCs) into…
Aug 11, 2025Ravie LakshmananEncryption / Network Security Cybersecurity researchers have discovered a fresh set of security issues in the Terrestrial…
Chrome sandbox escape nets security researcher $250,000 reward Pierluigi Paganini August 11, 2025 Researcher earns Google Chrome ’s top $250K…
A national security-focused Commerce Department component would get fresh IT investments to help keep dual-use U.S. technologies from ending up…
Microsoft has announced the limited public preview of Windows 365 Reserve, a service that provides temporary desktop access to pre-configured…
United States Attorney for the Southern District of New York, Jay Clayton, alongside FBI Assistant Director in Charge Christopher G….
Three Ghanaian men have been extradited to the US over $100 million fraud involving romance scams and business email compromise…
Aug 11, 2025Ravie LakshmananEncryption / Network Security Cybersecurity researchers have discovered a fresh set of security issues in the Terrestrial…