The year 2025 has been declared the International Year of Quantum Science by the United Nations (UN). Meanwhile, while Western…
Christina Marie Chapman, a 50-year-old woman from Arizona, was sentenced to 102 months in prison after pleading guilty to her…
The recently uncovered Gunra ransomware is the family to weaponize leaked Conti source code, unleashing rapid-fire double-extortion attacks against Windows…
Cybercriminals are using a variety of dishonest tactics in a sophisticated phishing effort aimed at Facebook users in order to…
Jul 25, 2025The Hacker NewsArtificial Intelligence / Data Privacy A recent analysis of enterprise data suggests that generative AI tools…
The Post Office has said it will not pay subpostmasters compensation to cover loss of business and costs as a…
Following U.S. Treasury sanctions imposed on July 1, 2025, the notorious bulletproof hosting provider Aeza Group has rapidly migrated its…
The United States government announced coordinated actions across multiple departments today, offering rewards totaling up to $15 million for information…
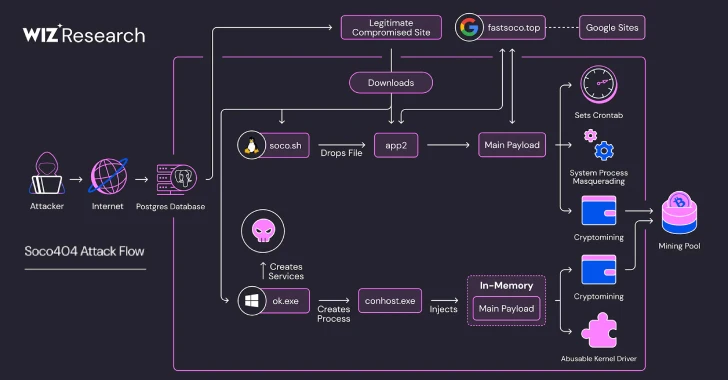
Jul 25, 2025Ravie LakshmananMalware / Cloud Security Threat hunters have disclosed two different malware campaigns that have targeted vulnerabilities and…
There’s an evolution in the receipts market in retail, with several brands making the switch from post-transaction paper to digital…
Microsoft has removed a compatibility hold that prevented some Easy Anti-Cheat users from installing the Windows 11 2024 Update because…
Google Forms, praised for friction-free data collection, has become the unlikely staging ground for rapidly spreading crypto-phishing campaign. First detected…