A newly identified loader malware dubbed CastleLoader has emerged as a significant threat since early 2025, rapidly evolving into a…
Chennai, India, July 25th, 2025, CyberNewsWire xonPlus, a real-time digital risk alerting system, officially launches today to help security teams…
Chennai, India, July 25th, 2025, CyberNewsWire xonPlus, a real-time digital risk alerting system, officially launches today to help security teams…
Chennai, India, July 25th, 2025, CyberNewsWire xonPlus, a real-time digital risk alerting system, officially launches today to help security teams…
A sophisticated Russian-aligned threat actor known as Hive0156 has intensified its cyber espionage campaigns against Ukrainian government and military organizations,…
International law enforcement agencies delivered a significant blow to cybercriminals this week with the successful takedown of critical infrastructure belonging…
Before rushing to prove that you’re not a robot, be wary of deceptive human verification pages as an increasingly popular…
Beginning today, millions of adults trying to access pornography in the United Kingdom will be required to prove that they…
A significant security breach has exposed critical vulnerabilities in Amazon’s artificial intelligence infrastructure, with hackers successfully injecting malicious computer-wiping commands…
It’s been six months since the EU’s Digital Operational Resilience Act (DORA) came into effect, but a new Censuswide survey…
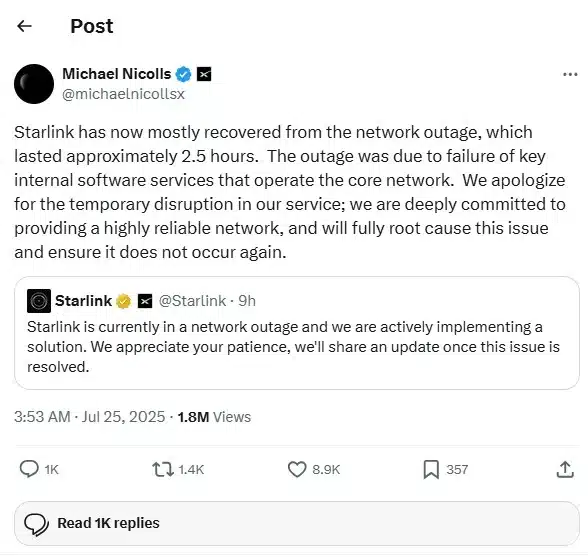
SpaceX’s Starlink internet service suffered a major international outage, disconnecting tens of thousands of users for over two hours. The…
Spoofed Microsoft SharePoint notifications have been a familiar lure for corporate users, but a wave of campaigns traced between March…