The demand for skilled tech professionals shows no signs of slowing down in 2025. You may be running a startup…
SAP has announced revenue of €9.027bn for the second quarter of 2025, up 9% year-on-year, and a gross profit of…
Government authorities and cybersecurity teams around the world are responding to a wave of cyberattacks targeting critical vulnerabilities in Microsoft…
Two high-severity vulnerabilities in TP-Link VIGI network video recorder (NVR) systems could allow attackers to execute arbitrary commands on affected…
An AI agent operating within the Replit platform reportedly deleted an entire company database without permission. The incident occurred during…
Multiple organisations have now been hit by Warlock ransomware deployed on their systems via the dangerous ToolShell vulnerability chain in…
Listen to the article 5 min This audio is auto-generated. Please let us know if you have feedback. Sean Plankey,…
A threat actor called EncryptHub has compromised a game on Steam to distribute info-stealing malware to unsuspecting users downloading the…
Threat researchers are warning of twin Chinese-nexus espionage operations—“Operation Chat” and “Operation PhantomPrayers”—that erupted in the weeks preceding the Dalai…
An airline leaving all of its passengers’ travel records vulnerable to hackers would make an attractive target for espionage. Less…
An AI agent operating within the Replit platform reportedly deleted an entire company database without permission. The incident occurred during…
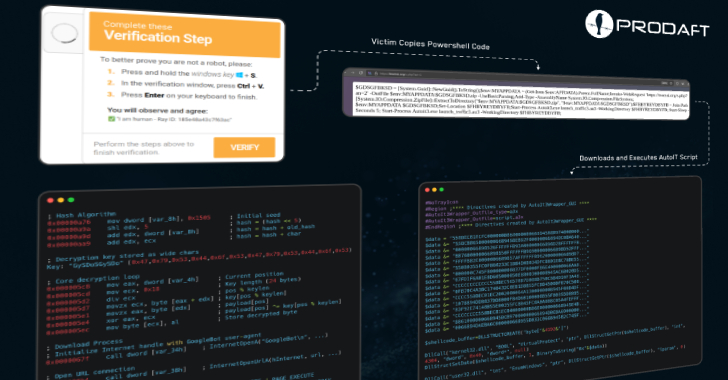
Jul 24, 2025Ravie LakshmananMalware / Cybercrime Cybersecurity researchers have shed light on a new versatile malware loader called CastleLoader that…