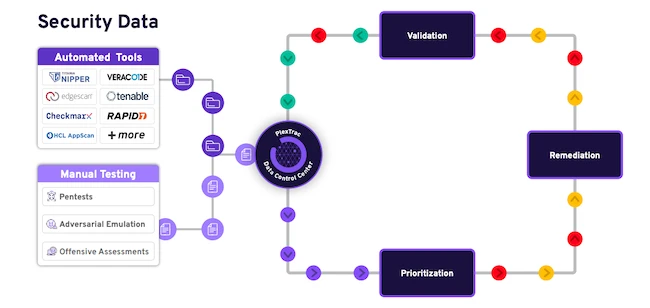
PlexTrac launched enhanced Workflow Automation Engine, a major product update designed to standardize workflows across the vulnerability lifecycle, automate pentest…
Jul 23, 2025Ravie LakshmananWindows Security / Cryptocurrency The Windows banking trojan known as Coyote has become the first known malware…
This is an attempt to show the differences–not without bias, but without hate. Functionality The iPhone focuses on doing a…
The National Nuclear Security Administration (NNSA) has fallen victim to a sophisticated cyber attack exploiting a previously unknown vulnerability in…
A significant cybersecurity breach has exposed vulnerabilities in critical US government infrastructure, as the National Nuclear Security Administration (NNSA) was…
Ukrainian authorities, with help from French police and Europol, have arrested a person suspected of running one of the largest…
With the news always full of stories about massive data breaches, whether they’re genuinely huge or just a false alarm,…
The term liberal arts denotes a curriculum that imparts general knowledge and develops the student’s rational thought and intellectual capabilities,…
Remote Monitoring and Management (RMM) software has long been the silent partner of help-desk engineers, automating patch cycles and troubleshooting…
Synology has issued an urgent security advisory addressing critical vulnerabilities in its BeeDrive desktop application for Windows that could allow…
One or more vulnerabilities affecting Cisco Identity Services Engine (ISE) are being exploited in the wild, Cisco has confirmed by…
Security experts have been talking about Kerberoasting for over a decade, yet this attack continues to evade typical defense methods….