Ransomware gangs have increasingly co-opted Remote Monitoring and Management (RMM) tools originally designed for IT operations to orchestrate sophisticated network…
In Britain, describing Marks & Spencer (M&S) as a high-profile retailer is akin to describing King Charles III as a…
India’s cryptocurrency exchange, CoinDCX, after confirming a cyberattack that resulted in a loss of approximately $44 million from its internal…
Image from scientificamerican.com Scientists are now discovering that self-control is a precious, finite resource that can be raised and lowered…
Google has released an urgent security update for Chrome, addressing critical vulnerabilities that could potentially allow attackers to gain complete…
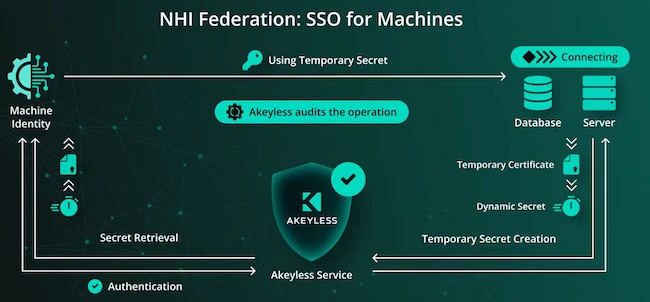
Akeyless launched NHI Federation, a solution that delivers Single Sign-On (SSO) for machines. As organizations increasingly operate workloads across on-premises…
So perhaps you’ve heard the story of evil America trying to enact a draconian immigration policy towards Mexico. It’s the…
Kali Linux maintainers have unveiled two new packages designed to unleash the full potential of the Raspberry Pi’s onboard wireless…
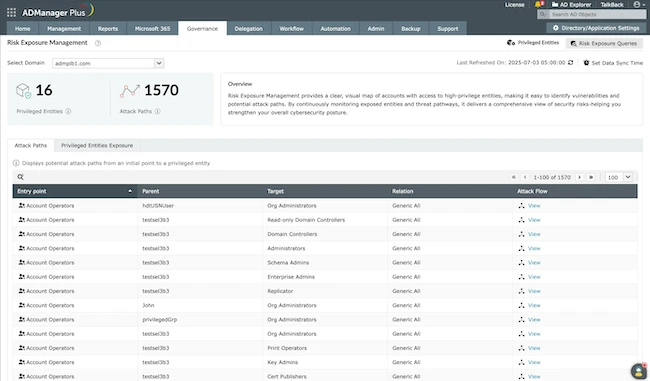
ManageEngine announced identity risk exposure management and local user MFA features in AD360, its converged identity and access management (IAM)…
Image from scientificamerican.com Scientists are now discovering that self-control is a precious, finite resource that can be raised and lowered…
Microsoft has confirmed that Chinese state-sponsored threat actors are actively exploiting critical zero-day vulnerabilities in on-premises SharePoint servers, prompting urgent…
Mozilla has today released Firefox 141, addressing a broad spectrum of security vulnerabilities that range from high-impact memory safety bugs…