The Clear Linux OS team has announced the shutdown of the project, marking the end of its 10-year existence in…
A new wave of cyber-attacks has emerged, exploiting Windows shortcut files (.LNK) combined with legitimate system utilities collectively known as…
The government may be seeking to pull back from a diplomatic row with the US over UK demands to require…
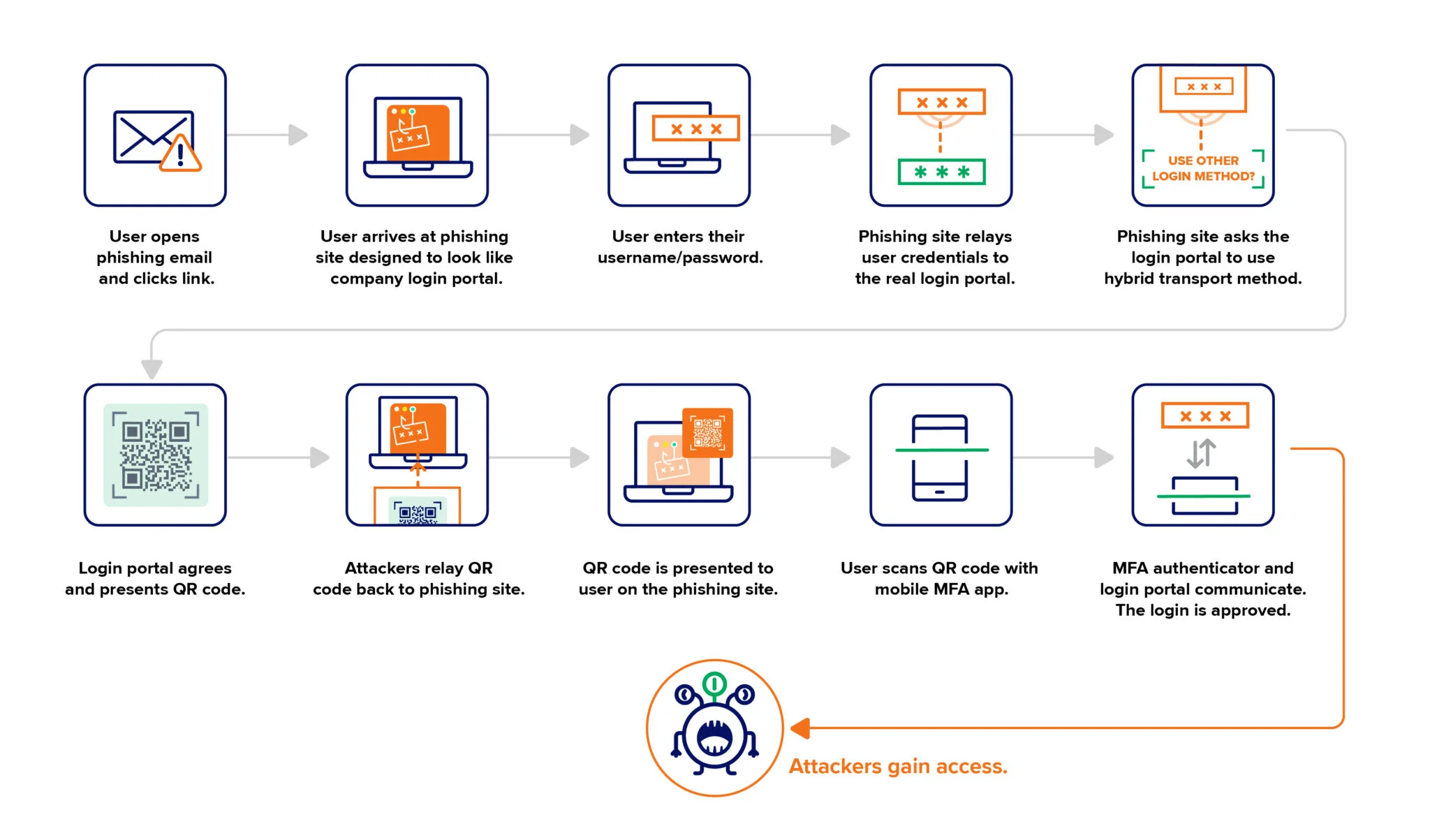
A phishing campaign is bypassing FIDO key authentication by exploiting cross-device sign-in features, a managed detection and response (MDR) provider…
US carrier Alaska Airlines grounded its flights after an IT outage that affected its systems, the company said. The unspecified…
I’ve moved to Chrome > and Safari > as my primary browsers, but nothing compares to Firefox > when it…
Arizona election officials say a hack targeting a statewide online portal for political candidates resulted in the defacement and replacement…
Seqrite Labs APT-Team has uncovered a persistent threat entity, UNG0002 (Unknown Group 0002), orchestrating espionage-driven operations across Asian jurisdictions, including…
An American state’s Army National Guard network was thoroughly hacked by a Chinese cyberespionage group nicknamed “Salt Typhoon,” according to a…
We’ve been debating agnosticism and atheism here for the last couple of weeks. One of the sub-arguments that has pronounced…
Threat actors have leveraged a phishing campaign targeting npm package maintainers, resulting in the compromise of widely used JavaScript tooling…
MuddyWater deploys new DCHSpy variants amid Iran-Israel conflict Pierluigi Paganini July 21, 2025 Iran-linked APT MuddyWater is deploying new DCHSpy…